Vulnerability Management Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,200
- Team License (2~5 Users) $ 4,200
- Corporate License (>5 Users) $ 5,200
Introduction
The vulnerability management market focuses on solutions and services designed to identify, prioritize, and mitigate security vulnerabilities in an organization’s IT infrastructure and software systems, a critical subfield of IT risk management. This process involves continuously scanning for vulnerabilities, such as misconfigured firewalls that could allow malware infiltration or unpatched flaws in operating systems’ remote desktop protocols that might enable unauthorized device access. The vulnerability management lifecycle encompasses key stages: discovery, assessment, remediation, and reporting, leveraging tools like vulnerability scanners, configuration management systems, and threat intelligence platforms. The market is driven by the escalating frequency and sophistication of cyberattacks, stringent regulatory requirements, and the rapid adoption of digital transformation across industries. In China, the Ministry of Industry and Information Technology, the Cyberspace Administration, and the Ministry of Public Security jointly issued the “Network Product Security Vulnerability Management Regulations,” effective September 1, 2021, underscoring global emphasis on cybersecurity compliance. The market serves large enterprises and small to medium-sized enterprises (SMEs), with solutions deployed either on-premises or in the cloud. North America leads demand due to its advanced cybersecurity ecosystem, while Asia Pacific grows rapidly due to increasing digitalization. Emerging trends include AI-driven vulnerability prioritization, integration with DevSecOps, and automation for real-time threat response. Challenges such as high implementation costs, skill shortages, and evolving threat landscapes pose hurdles to market growth.
Market Size and Growth Forecast
The global vulnerability management market is projected to reach USD 17–20 billion by 2025, with an estimated compound annual growth rate (CAGR) of 7%–9% through 2030. This growth is fueled by rising cyber threats, regulatory mandates, and the increasing adoption of cloud-based solutions, supported by advancements in AI and automation for vulnerability management.
Regional Analysis
North America is expected to lead the vulnerability management market with a growth rate of 7.5%–9.5%, driven by the United States and Canada. The U.S. dominates due to its robust cybersecurity infrastructure, high-profile data breaches, and stringent regulations like GDPR and CCPA influencing global standards. Companies like Rapid7 and Tenable drive innovation in this region. Canada’s growing tech sector and government cybersecurity initiatives contribute to steady demand, with trends focusing on cloud-based solutions.
Asia Pacific follows with a growth rate of 8%–10%, led by China, India, and Japan. China’s market is propelled by rapid digitalization, government regulations like the 2021 Vulnerability Management Regulations, and increasing cyber threats, supporting local adoption. India’s expanding IT and fintech sectors drive demand for affordable solutions, while Japan’s focus on enterprise security fuels growth in advanced tools.
Europe, with a growth rate of 6.5%–8.5%, is driven by Germany, France, and the UK. Germany’s industrial and financial sectors prioritize vulnerability management to protect critical infrastructure, while France and the UK emphasize compliance with GDPR and cybersecurity frameworks. Trends include AI-driven threat detection and cloud adoption.
South America, with a growth rate of 6%–8%, sees demand in Brazil and Argentina, driven by digital transformation in banking and retail. Brazil’s growing cybersecurity awareness fuels adoption, though budget constraints limit broader penetration.
The Middle East and Africa, with a growth rate of 5.5%–7.5%, are led by the UAE and South Africa. The UAE’s smart city initiatives and financial sector drive demand, while South Africa’s enterprise growth supports adoption. Limited cybersecurity expertise poses challenges.
Application Analysis
Large Enterprises: Expected to grow at 7%–9%, this segment dominates due to complex IT infrastructures and high exposure to cyber threats. Solutions focus on comprehensive scanning, real-time monitoring, and integration with enterprise security systems, with trends emphasizing automation and AI-driven prioritization.
SMEs: With a growth rate of 7.5%–9.5%, this segment is driven by increasing digital adoption and cost-effective cloud-based solutions. Trends include scalable, user-friendly tools and managed services to address limited in-house expertise.
Type Analysis
Cloud: Projected to grow at 8%–10%, cloud-based solutions dominate due to their scalability, lower upfront costs, and ease of deployment. Trends focus on integration with cloud-native platforms, DevSecOps, and real-time threat intelligence.
On-Premises: Expected to grow at 6%–8%, this segment serves organizations with stringent data control requirements, such as financial institutions. Trends include hybrid deployments and enhanced security for legacy systems.
Key Market Players
Infinite Group: A U.S.-based company, Infinite Group provides comprehensive vulnerability management solutions, focusing on enterprise-grade cybersecurity and managed services for threat detection and remediation.
Rapid7: A U.S. firm, Rapid7 offers cloud and on-premises vulnerability management platforms, known for advanced analytics, automation, and integration with DevSecOps for large enterprises and SMEs.
Qualys: A U.S. manufacturer, Qualys specializes in cloud-based vulnerability management solutions, emphasizing real-time scanning, compliance reporting, and scalability for global enterprises.
Tenable: A U.S. company, Tenable provides vulnerability management tools with AI-driven prioritization and comprehensive asset discovery, targeting both large enterprises and SMEs across industries.
Porter’s Five Forces Analysis
●Threat of New Entrants: Moderate. The vulnerability management market has high barriers, including significant R&D costs for advanced scanning and AI technologies, as well as the need for regulatory compliance and established trust. Leaders like Qualys and Tenable dominate, but new players offering niche, cloud-based solutions can emerge, slightly increasing the threat.
●Threat of Substitutes: Low to Moderate. Alternatives like manual penetration testing or basic security software exist, but vulnerability management solutions offer unmatched automation and scalability for continuous monitoring. Open-source tools pose a moderate threat in cost-sensitive SME markets.
●Bargaining Power of Buyers: Moderate to High. Enterprises and SMEs have negotiating power due to multiple vendors and subscription-based pricing models, particularly in cloud solutions. However, specialized AI-driven platforms limit switching options, balancing buyer power.
●Bargaining Power of Suppliers: Moderate. Suppliers of cybersecurity software components, cloud infrastructure, and threat intelligence feeds hold some leverage, but global cloud providers and diverse supply chains reduce their power.
●Competitive Rivalry: High. The market is highly competitive, with players like Rapid7, Qualys, and Tenable competing on innovation, scalability, and integration capabilities. Emerging vendors offering affordable cloud solutions intensify rivalry, particularly in the SME segment.
Market Opportunities and Challenges
Opportunities
●Rising Cyber Threats: The increasing frequency of cyberattacks, such as ransomware and phishing, drives demand for advanced vulnerability management solutions across all regions.
●Regulatory Compliance: Global regulations, like China’s 2021 Vulnerability Management Regulations and GDPR in Europe, create opportunities for compliance-focused tools in enterprises.
●Cloud Adoption: The shift to cloud-based IT infrastructure, especially in North America and Asia Pacific, boosts demand for scalable, cloud-native vulnerability management solutions.
●AI and Automation: Integration of AI for threat prioritization and automation for real-time remediation enhances solution appeal, particularly for large enterprises.
●Emerging Market Growth: Rapid digitalization in India, Brazil, and the UAE offers potential for cost-effective, cloud-based solutions tailored to SMEs.
Challenges
●High Implementation Costs: Deploying comprehensive vulnerability management systems, especially on-premises, requires significant investment, limiting adoption in SMEs and emerging markets.
●Skill Shortages: The need for skilled cybersecurity professionals to manage and interpret vulnerability data is scarce, particularly in South America and the Middle East and Africa.
●Evolving Threat Landscape: Rapidly changing cyber threats, including zero-day vulnerabilities, require continuous updates to scanning and remediation tools, challenging vendors.
●Regulatory Complexity: Compliance with diverse global cybersecurity regulations increases development and deployment costs, particularly in Europe and North America.
●Integration Challenges: Integrating vulnerability management with existing IT and DevSecOps workflows can be complex, hindering adoption in organizations with legacy systems.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 Introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 Industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Vulnerability Management Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Vulnerability Management Market in North America (2020-2030)
8.1 Vulnerability Management Market Size
8.2 Vulnerability Management Market by End Use
8.3 Competition by Players/Suppliers
8.4 Vulnerability Management Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Vulnerability Management Market in South America (2020-2030)
9.1 Vulnerability Management Market Size
9.2 Vulnerability Management Market by End Use
9.3 Competition by Players/Suppliers
9.4 Vulnerability Management Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Vulnerability Management Market in Asia & Pacific (2020-2030)
10.1 Vulnerability Management Market Size
10.2 Vulnerability Management Market by End Use
10.3 Competition by Players/Suppliers
10.4 Vulnerability Management Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Vulnerability Management Market in Europe (2020-2030)
11.1 Vulnerability Management Market Size
11.2 Vulnerability Management Market by End Use
11.3 Competition by Players/Suppliers
11.4 Vulnerability Management Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Vulnerability Management Market in MEA (2020-2030)
12.1 Vulnerability Management Market Size
12.2 Vulnerability Management Market by End Use
12.3 Competition by Players/Suppliers
12.4 Vulnerability Management Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Vulnerability Management Market (2020-2025)
13.1 Vulnerability Management Market Size
13.2 Vulnerability Management Market by End Use
13.3 Competition by Players/Suppliers
13.4 Vulnerability Management Market Size by Type
Chapter 14 Global Vulnerability Management Market Forecast (2025-2030)
14.1 Vulnerability Management Market Size Forecast
14.2 Vulnerability Management Application Forecast
14.3 Competition by Players/Suppliers
14.4 Vulnerability Management Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Infinite Group
15.1.1 Company Profile
15.1.2 Main Business and Vulnerability Management Information
15.1.3 SWOT Analysis of Infinite Group
15.1.4 Infinite Group Vulnerability Management Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 Rapid 7
15.2.1 Company Profile
15.2.2 Main Business and Vulnerability Management Information
15.2.3 SWOT Analysis of Rapid 7
15.2.4 Rapid 7 Vulnerability Management Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 Qualys
15.3.1 Company Profile
15.3.2 Main Business and Vulnerability Management Information
15.3.3 SWOT Analysis of Qualys
15.3.4 Qualys Vulnerability Management Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 Tenable
15.4.1 Company Profile
15.4.2 Main Business and Vulnerability Management Information
15.4.3 SWOT Analysis of Tenable
15.4.4 Tenable Vulnerability Management Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope Of Vulnerability Management Report
Table Data Sources Of Vulnerability Management Report
Table Major Assumptions Of Vulnerability Management Report
Table Vulnerability Management Classification
Table Vulnerability Management Applications
Table Drivers Of Vulnerability Management Market
Table Restraints Of Vulnerability Management Market
Table Opportunities Of Vulnerability Management Market
Table Threats Of Vulnerability Management Market
Table Raw Materials Suppliers
Table Different Production Methods Of Vulnerability Management
Table Cost Structure Analysis Of Vulnerability Management
Table Key End Users
Table Latest News Of Vulnerability Management Market
Table Merger And Acquisition
Table Planned/Future Project Of Vulnerability Management Market
Table Policy Of Vulnerability Management Market
Table 2020-2030 North America Vulnerability Management Market Size
Table 2020-2030 North America Vulnerability Management Market Size By Application
Table 2020-2025 North America Vulnerability Management Key Players Revenue
Table 2020-2025 North America Vulnerability Management Key Players Market Share
Table 2020-2030 North America Vulnerability Management Market Size By Type
Table 2020-2030 United States Vulnerability Management Market Size
Table 2020-2030 Canada Vulnerability Management Market Size
Table 2020-2030 Mexico Vulnerability Management Market Size
Table 2020-2030 South America Vulnerability Management Market Size
Table 2020-2030 South America Vulnerability Management Market Size By Application
Table 2020-2025 South America Vulnerability Management Key Players Revenue
Table 2020-2025 South America Vulnerability Management Key Players Market Share
Table 2020-2030 South America Vulnerability Management Market Size By Type
Table 2020-2030 Brazil Vulnerability Management Market Size
Table 2020-2030 Argentina Vulnerability Management Market Size
Table 2020-2030 Chile Vulnerability Management Market Size
Table 2020-2030 Peru Vulnerability Management Market Size
Table 2020-2030 Asia & Pacific Vulnerability Management Market Size
Table 2020-2030 Asia & Pacific Vulnerability Management Market Size By Application
Table 2020-2025 Asia & Pacific Vulnerability Management Key Players Revenue
Table 2020-2025 Asia & Pacific Vulnerability Management Key Players Market Share
Table 2020-2030 Asia & Pacific Vulnerability Management Market Size By Type
Table 2020-2030 China Vulnerability Management Market Size
Table 2020-2030 India Vulnerability Management Market Size
Table 2020-2030 Japan Vulnerability Management Market Size
Table 2020-2030 South Korea Vulnerability Management Market Size
Table 2020-2030 Southeast Asia Vulnerability Management Market Size
Table 2020-2030 Australia Vulnerability Management Market Size
Table 2020-2030 Europe Vulnerability Management Market Size
Table 2020-2030 Europe Vulnerability Management Market Size By Application
Table 2020-2025 Europe Vulnerability Management Key Players Revenue
Table 2020-2025 Europe Vulnerability Management Key Players Market Share
Table 2020-2030 Europe Vulnerability Management Market Size By Type
Table 2020-2030 Germany Vulnerability Management Market Size
Table 2020-2030 France Vulnerability Management Market Size
Table 2020-2030 United Kingdom Vulnerability Management Market Size
Table 2020-2030 Italy Vulnerability Management Market Size
Table 2020-2030 Spain Vulnerability Management Market Size
Table 2020-2030 Belgium Vulnerability Management Market Size
Table 2020-2030 Netherlands Vulnerability Management Market Size
Table 2020-2030 Austria Vulnerability Management Market Size
Table 2020-2030 Poland Vulnerability Management Market Size
Table 2020-2030 Russia Vulnerability Management Market Size
Table 2020-2030 Mea Vulnerability Management Market Size
Table 2020-2030 Mea Vulnerability Management Market Size By Application
Table 2020-2025 Mea Vulnerability Management Key Players Revenue
Table 2020-2025 Mea Vulnerability Management Key Players Market Share
Table 2020-2030 Mea Vulnerability Management Market Size By Type
Table 2020-2030 Egypt Vulnerability Management Market Size
Table 2020-2030 Israel Vulnerability Management Market Size
Table 2020-2030 South Africa Vulnerability Management Market Size
Table 2020-2030 Gulf Cooperation Council Countries Vulnerability Management Market Size
Table 2020-2030 Turkey Vulnerability Management Market Size
Table 2020-2025 Global Vulnerability Management Market Size By Region
Table 2020-2025 Global Vulnerability Management Market Size Share By Region
Table 2020-2025 Global Vulnerability Management Market Size By Application
Table 2020-2025 Global Vulnerability Management Market Share By Application
Table 2020-2025 Global Vulnerability Management Key Vendors Revenue
Table 2020-2025 Global Vulnerability Management Key Vendors Market Share
Table 2020-2025 Global Vulnerability Management Market Size By Type
Table 2020-2025 Global Vulnerability Management Market Share By Type
Table 2025-2030 Global Vulnerability Management Market Size By Region
Table 2025-2030 Global Vulnerability Management Market Size Share By Region
Table 2025-2030 Global Vulnerability Management Market Size By Application
Table 2025-2030 Global Vulnerability Management Market Share By Application
Table 2025-2030 Global Vulnerability Management Key Vendors Revenue
Table 2025-2030 Global Vulnerability Management Key Vendors Market Share
Table 2025-2030 Global Vulnerability Management Market Size By Type
Table 2025-2030 Vulnerability Management Global Market Share By Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Vulnerability Management Picture
Figure 2020-2030 North America Vulnerability Management Market Size And Cagr
Figure 2020-2030 South America Vulnerability Management Market Size And Cagr
Figure 2020-2030 Asia & Pacific Vulnerability Management Market Size And Cagr
Figure 2020-2030 Europe Vulnerability Management Market Size And Cagr
Figure 2020-2030 Mea Vulnerability Management Market Size And Cagr
Figure 2020-2025 Global Vulnerability Management Market Size And Growth Rate
Figure 2025-2030 Global Vulnerability Management Market Size And Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
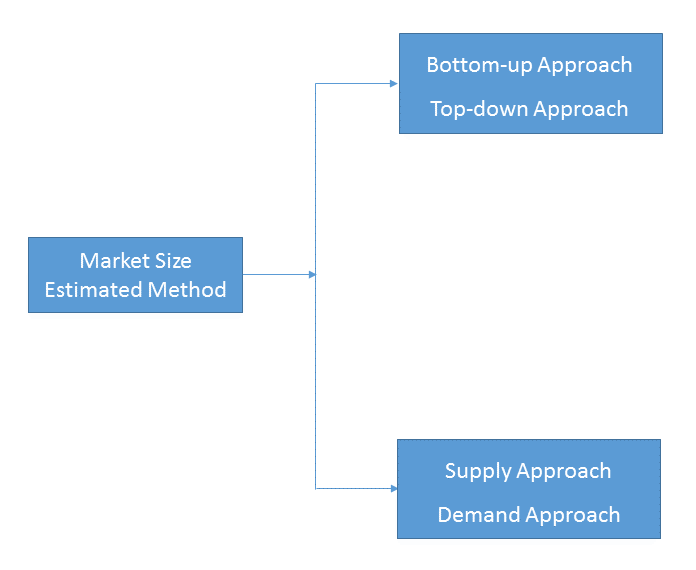
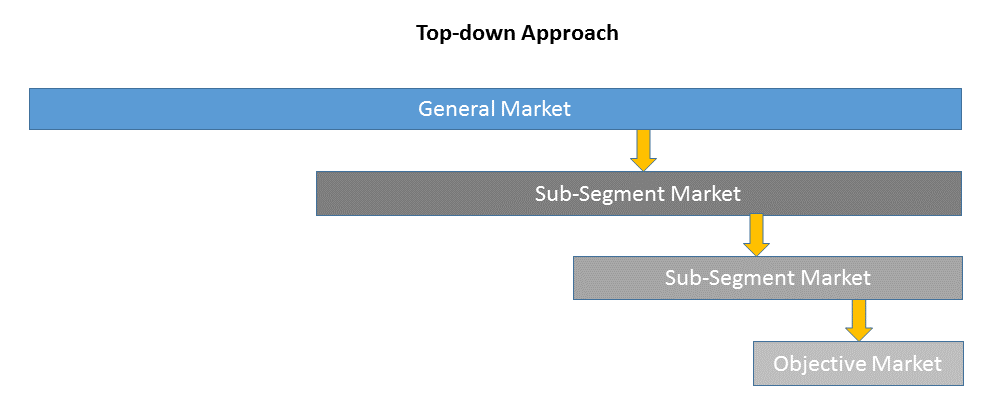
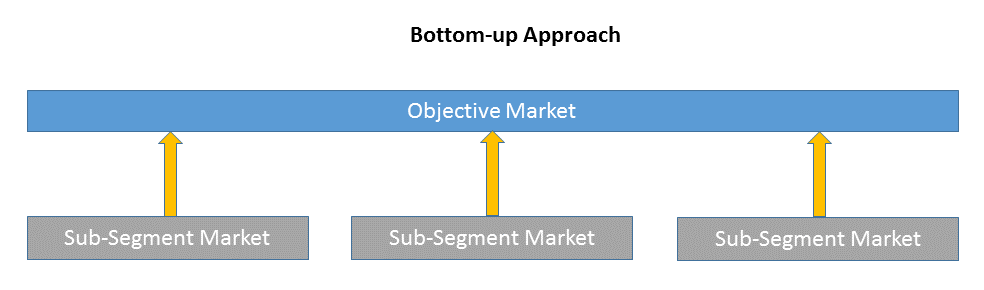
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
Bottom-up approach size the objective market by collecting the sub-segment information.
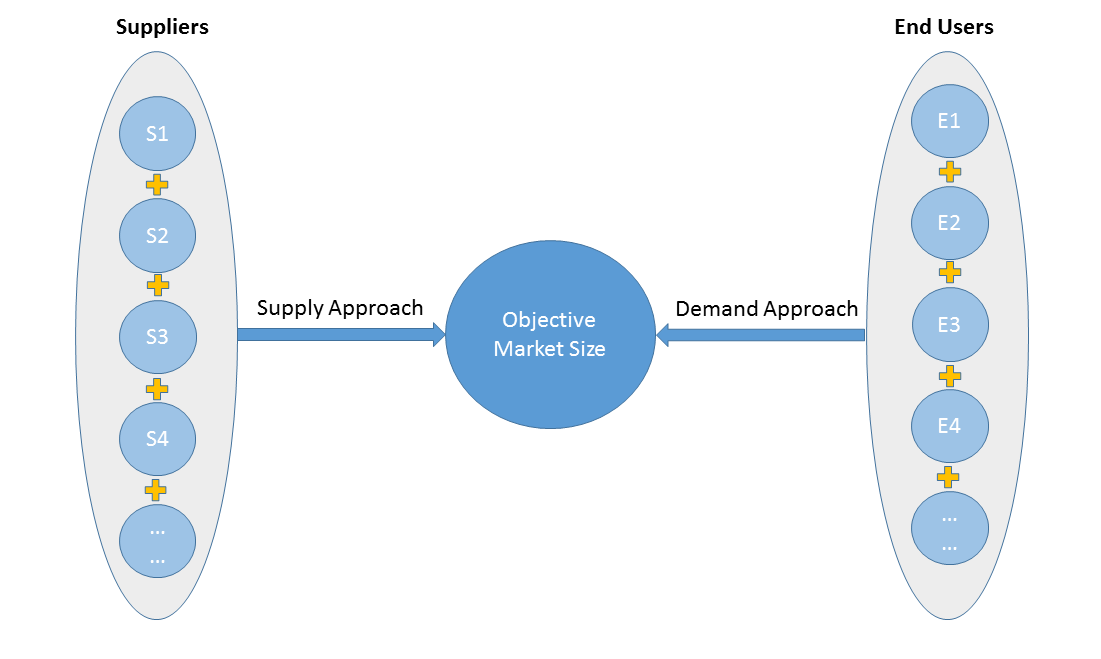
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
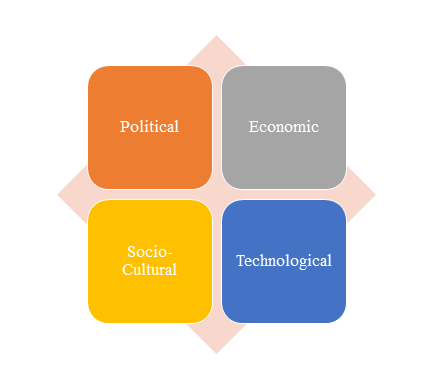
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
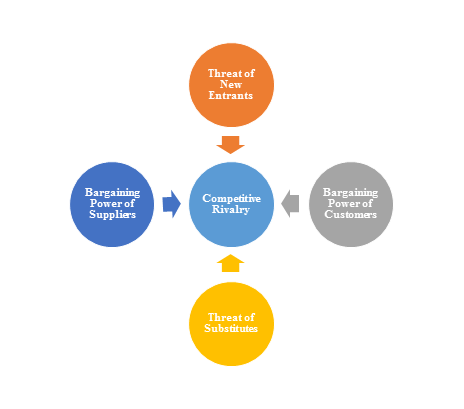
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
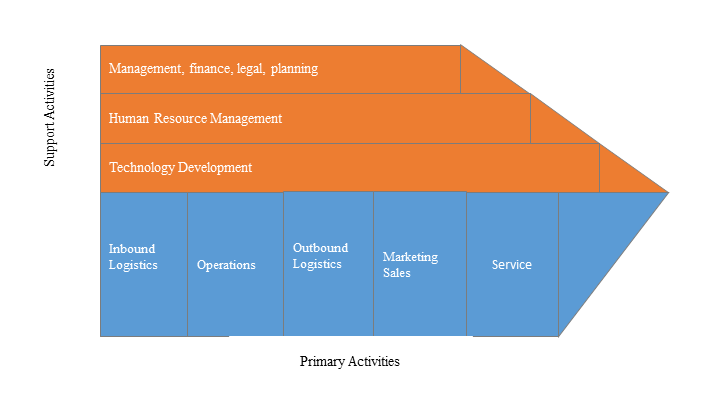
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
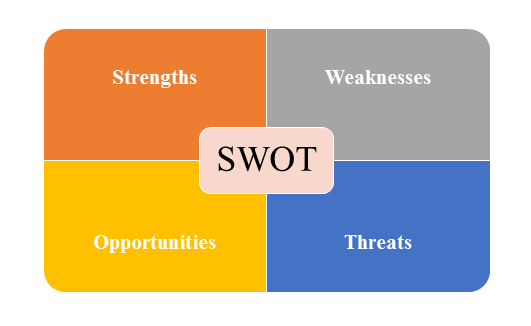
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |