Threat Intelligence Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,600
- Team License (2~5 Users) $ 4,600
- Corporate License (>5 Users) $ 5,600
The Threat Intelligence market is a dynamic and rapidly evolving segment within the broader cybersecurity industry, driven by the increasing complexity and frequency of cyber threats targeting organizations worldwide. Threat Intelligence refers to the collection, analysis, and dissemination of data related to potential or existing cyber threats, enabling organizations to proactively defend against attacks, mitigate risks, and enhance their security posture. This market encompasses solutions and services that provide actionable insights into threat actors, their tactics, techniques, and procedures (TTPs), as well as vulnerabilities and attack vectors. The market is characterized by its critical role in enabling organizations to anticipate and respond to cyber incidents, ranging from malware and phishing to advanced persistent threats (APTs) and ransomware. Its importance has grown with the digital transformation of industries, the proliferation of cloud computing, and the rising sophistication of cybercriminals.
The global Threat Intelligence market is estimated to reach a valuation of approximately USD 8.0–15.0 billion in 2025, with a compound annual growth rate (CAGR) projected in the range of 9.0%–16.0% through 2030. This robust growth is fueled by escalating cyber threats, increased regulatory pressures, and the growing adoption of proactive cybersecurity strategies across enterprises. The market benefits from the integration of artificial intelligence (AI), machine learning (ML), and automation, which enhance the speed and accuracy of threat detection and response. Additionally, the shift toward hybrid and multi-cloud environments, coupled with the expansion of Internet of Things (IoT) ecosystems, is driving demand for comprehensive threat intelligence solutions that can address diverse and evolving attack surfaces.
Application Analysis and Market Segmentation
The Threat Intelligence market is segmented by application into Small and Medium Enterprises (SMEs) and Large Enterprises, each with distinct needs and growth trajectories.
SMEs: Threat Intelligence for SMEs is gaining traction as smaller organizations increasingly recognize the need for robust cybersecurity despite limited resources. These solutions are typically designed to be cost-effective, scalable, and easy to deploy, often delivered through cloud-based platforms. SMEs are expected to see annual growth rates of 10%–15%, driven by the rising incidence of cyber threats targeting smaller businesses, such as ransomware and phishing campaigns. The affordability of subscription-based services and managed security offerings is enabling SMEs to adopt threat intelligence, particularly in industries like retail, healthcare, and financial services, where data breaches can have significant consequences. The trend toward simplified, user-friendly dashboards and automated threat feeds is further accelerating adoption among SMEs, which often lack dedicated cybersecurity teams.
Large Enterprises: Large Enterprises dominate the Threat Intelligence market due to their complex IT environments, higher exposure to sophisticated threats, and greater financial capacity to invest in advanced cybersecurity solutions. This segment is anticipated to grow at 8%–14% annually, supported by the need to protect critical infrastructure, intellectual property, and customer data across global operations. Large Enterprises leverage threat intelligence for advanced use cases, such as threat hunting, incident response, and integration with Security Operations Centers (SOCs). The growing adoption of zero-trust architectures and the need to comply with stringent regulations, such as GDPR and CCPA, are key drivers. Additionally, large organizations are increasingly investing in customized threat intelligence services tailored to their industry-specific risks, such as financial fraud or supply chain attacks.
By Type: Solution and Services
The market is further segmented by type into Solutions and Services, each playing a critical role in delivering actionable threat intelligence.
Solutions: Threat Intelligence Solutions include platforms, software, and tools that collect, analyze, and deliver threat data to organizations. These solutions often integrate with existing security infrastructure, such as Security Information and Event Management (SIEM) systems, firewalls, and endpoint protection platforms. The Solutions segment is expected to grow at 9%–15% annually, driven by the demand for real-time threat detection, automated analysis, and integration with AI-driven analytics. Key trends include the rise of cloud-native platforms, which offer scalability and flexibility, and the incorporation of open-source intelligence (OSINT) and dark web monitoring to provide comprehensive threat visibility. The development of industry-specific threat intelligence feeds, tailored to sectors like finance, healthcare, and critical infrastructure, is also boosting growth in this segment.
Services: Threat Intelligence Services encompass consulting, managed security services, and professional services, such as threat assessments and incident response support. This segment is projected to grow at 10%–16% annually, reflecting the increasing reliance on third-party expertise to augment in-house capabilities. Managed Threat Intelligence Services are particularly popular, as they allow organizations to outsource complex tasks like threat monitoring and analysis to specialized providers. The rise of Managed Detection and Response (MDR) services, which combine threat intelligence with proactive response, is a significant growth driver. Additionally, services focused on threat intelligence sharing and collaboration, such as Information Sharing and Analysis Centers (ISACs), are gaining momentum as organizations seek to leverage collective intelligence to combat cyber threats.
Regional Market Distribution and Geographic Trends
The Threat Intelligence market exhibits varied growth patterns across regions, influenced by regional cybersecurity maturity, regulatory environments, and digital adoption rates.
Asia-Pacific: The Asia-Pacific region is expected to experience annual growth of 12%–18%, driven by rapid digitalization, increasing cyber threats, and growing investments in cybersecurity infrastructure. China, India, and Japan are key markets, with China leading due to its large-scale digital economy and rising incidents of state-sponsored cyberattacks. India’s growth is fueled by its expanding IT and financial services sectors, while Japan’s focus on securing critical infrastructure and preparing for global events drives demand. The region’s diverse regulatory landscape and increasing adoption of cloud-based solutions are key trends shaping the market.
North America: North America, particularly the United States, remains the largest market, with projected growth of 8%–13% annually. The U.S. dominates due to its advanced cybersecurity ecosystem, high incidence of cyber threats, and significant investments by enterprises and government agencies. The region’s focus on compliance with regulations like NIST and CMMC, coupled with the adoption of advanced technologies like AI and ML, supports market expansion. Canada also contributes to growth, particularly in financial services and healthcare.
Europe: Europe is anticipated to grow at 7%–12% annually, with Germany, the UK, and France as key markets. The region’s stringent data protection regulations, such as GDPR, drive demand for threat intelligence to ensure compliance and protect sensitive data. The rise of cyber threats targeting critical infrastructure, such as energy and transportation, is prompting European governments and enterprises to invest in advanced solutions. Collaborative initiatives, such as EU-wide threat intelligence sharing, are also emerging as a key trend.
Latin America: Latin America is projected to grow at 9%–14% annually, with Brazil and Mexico leading due to their growing digital economies and increasing cybersecurity awareness. The region faces challenges like budget constraints and a shortage of skilled cybersecurity professionals, but the rise of cloud-based threat intelligence solutions is enabling broader adoption. Financial services and retail are key sectors driving demand.
Middle East & Africa: The Middle East & Africa region is expected to grow at 10%–15% annually, with the Gulf Cooperation Council (GCC) countries, particularly the UAE and Saudi Arabia, as major contributors. The region’s focus on digital transformation, driven by initiatives like Saudi Vision 2030, is increasing the need for robust cybersecurity measures. The rise of cyber threats targeting oil and gas, financial services, and government sectors is a key driver.
Key Market Players and Competitive Landscape
The Threat Intelligence market is highly competitive, with a mix of established technology giants and specialized cybersecurity firms. Key players include:
CrowdStrike: A leader in endpoint security and threat intelligence, CrowdStrike offers its Falcon platform, which integrates real-time threat intelligence with incident response capabilities. Its focus on cloud-native solutions and AI-driven analytics positions it as a market leader.
Palo Alto Networks: Known for its comprehensive cybersecurity portfolio, Palo Alto Networks provides threat intelligence through its Cortex XDR platform, which integrates with its firewalls and cloud security solutions.
Microsoft: Leveraging its global cloud infrastructure, Microsoft offers threat intelligence through its Defender suite and Azure Sentinel, focusing on AI-driven insights and integration with enterprise ecosystems.
FireEye (Mandiant): A pioneer in threat intelligence, Mandiant provides advanced threat research and incident response services, with a focus on nation-state and advanced persistent threats.
IBM: IBM’s X-Force threat intelligence platform combines AI, threat research, and global threat data to deliver actionable insights, particularly for large enterprises.
Recorded Future: Specializing in real-time threat intelligence, Recorded Future leverages OSINT and dark web monitoring to provide predictive insights for proactive defense.
Anomali: Anomali focuses on threat intelligence management, offering platforms to aggregate and analyze threat data, enabling organizations to operationalize intelligence effectively.
These companies compete on innovation, integration capabilities, and the ability to provide actionable, industry-specific intelligence. Partnerships with industry-specific ISACs and government agencies are also key to maintaining a competitive edge.
Industry Value Chain Analysis
The Threat Intelligence value chain is complex, spanning data collection, analysis, dissemination, and integration into cybersecurity operations, with value concentrated in actionable insights and integration with enterprise systems.
Raw Data and Upstream Inputs: The value chain begins with the collection of raw threat data from diverse sources, including open-source intelligence (OSINT), dark web forums, internal security logs, and third-party feeds. Data providers, such as Intel 471 and Digital Shadows, specialize in aggregating and curating this data, ensuring its relevance and accuracy. The quality and breadth of data sources are critical, as they determine the effectiveness of downstream analysis.
Analysis and Processing: At this stage, raw data is processed using AI, ML, and human expertise to identify patterns, correlate threats, and generate actionable intelligence. Companies like CrowdStrike and Recorded Future excel in this phase, leveraging proprietary algorithms and threat research teams to produce high-quality intelligence. The ability to provide real-time, context-rich insights is a key differentiator, particularly for high-risk industries like finance and healthcare.
Distribution and Delivery: Threat intelligence is delivered through platforms, APIs, or managed services to end-users. Cloud-based platforms, such as those offered by Palo Alto Networks and Microsoft, enable seamless integration with existing security tools, while managed services from firms like FireEye provide hands-on support. Distribution channels must ensure low latency and compatibility with diverse IT environments to maximize value.
Integration and Application: Downstream, organizations integrate threat intelligence into their security operations, including SIEM systems, firewalls, and incident response workflows. This stage adds significant value by enabling proactive defense, threat hunting, and compliance with regulatory requirements. Industry-specific intelligence, tailored to sectors like retail or energy, enhances the relevance of the intelligence.
End-User Industries: The ultimate value is realized by end-users, including enterprises, government agencies, and SMEs across sectors like finance, healthcare, and critical infrastructure. These industries leverage threat intelligence to protect assets, comply with regulations, and maintain operational continuity, capturing high margins through enhanced security and risk mitigation.
Market Opportunities and Challenges
Opportunities: The Threat Intelligence market offers significant growth potential, driven by the increasing sophistication of cyber threats and the global push for digital transformation. The rise of AI and ML technologies presents opportunities to enhance the speed and accuracy of threat detection, enabling vendors to offer differentiated solutions. The growing adoption of cloud-based and managed services is expanding access to threat intelligence for SMEs and emerging markets, particularly in Asia-Pacific and Latin America. Additionally, collaboration through ISACs and public-private partnerships is creating new avenues for sharing intelligence and combating threats collectively. The increasing focus on industry-specific intelligence, such as for healthcare or financial services, also offers premium pricing opportunities.
Challenges: The market faces several challenges, including the complexity of integrating threat intelligence into diverse IT environments, which can limit adoption among resource-constrained organizations. The rapid evolution of cyber threats requires continuous investment in research and development, increasing costs for vendors. Data overload and the challenge of distinguishing actionable intelligence from noise remain significant hurdles. Additionally, the market’s reliance on skilled cybersecurity professionals, coupled with a global shortage of talent, poses operational constraints. Competition from open-source and low-cost alternatives, as well as the risk of commoditization in certain segments, could pressure margins for vendors.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Threat Intelligence Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Threat Intelligence Market in North America (2020-2030)
8.1 Threat Intelligence Market Size
8.2 Threat Intelligence Market by End Use
8.3 Competition by Players/Suppliers
8.4 Threat Intelligence Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Threat Intelligence Market in South America (2020-2030)
9.1 Threat Intelligence Market Size
9.2 Threat Intelligence Market by End Use
9.3 Competition by Players/Suppliers
9.4 Threat Intelligence Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Threat Intelligence Market in Asia & Pacific (2020-2030)
10.1 Threat Intelligence Market Size
10.2 Threat Intelligence Market by End Use
10.3 Competition by Players/Suppliers
10.4 Threat Intelligence Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Threat Intelligence Market in Europe (2020-2030)
11.1 Threat Intelligence Market Size
11.2 Threat Intelligence Market by End Use
11.3 Competition by Players/Suppliers
11.4 Threat Intelligence Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Threat Intelligence Market in MEA (2020-2030)
12.1 Threat Intelligence Market Size
12.2 Threat Intelligence Market by End Use
12.3 Competition by Players/Suppliers
12.4 Threat Intelligence Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Threat Intelligence Market (2020-2025)
13.1 Threat Intelligence Market Size
13.2 Threat Intelligence Market by End Use
13.3 Competition by Players/Suppliers
13.4 Threat Intelligence Market Size by Type
Chapter 14 Global Threat Intelligence Market Forecast (2025-2030)
14.1 Threat Intelligence Market Size Forecast
14.2 Threat Intelligence Application Forecast
14.3 Competition by Players/Suppliers
14.4 Threat Intelligence Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Anomali
15.1.1 Company Profile
15.1.2 Main Business and Threat Intelligence Information
15.1.3 SWOT Analysis of Anomali
15.1.4 Anomali Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 Bitdefender
15.2.1 Company Profile
15.2.2 Main Business and Threat Intelligence Information
15.2.3 SWOT Analysis of Bitdefender
15.2.4 Bitdefender Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 Cisco
15.3.1 Company Profile
15.3.2 Main Business and Threat Intelligence Information
15.3.3 SWOT Analysis of Cisco
15.3.4 Cisco Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 CrowdStrike
15.4.1 Company Profile
15.4.2 Main Business and Threat Intelligence Information
15.4.3 SWOT Analysis of CrowdStrike
15.4.4 CrowdStrike Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 Cyble
15.5.1 Company Profile
15.5.2 Main Business and Threat Intelligence Information
15.5.3 SWOT Analysis of Cyble
15.5.4 Cyble Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 Digital Shadows
15.6.1 Company Profile
15.6.2 Main Business and Threat Intelligence Information
15.6.3 SWOT Analysis of Digital Shadows
15.6.4 Digital Shadows Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.7 FireEye (Mandiant)
15.7.1 Company Profile
15.7.2 Main Business and Threat Intelligence Information
15.7.3 SWOT Analysis of FireEye (Mandiant)
15.7.4 FireEye (Mandiant) Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.8 Fortinet
15.8.1 Company Profile
15.8.2 Main Business and Threat Intelligence Information
15.8.3 SWOT Analysis of Fortinet
15.8.4 Fortinet Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.9 Google (Mandiant)
15.9.1 Company Profile
15.9.2 Main Business and Threat Intelligence Information
15.9.3 SWOT Analysis of Google (Mandiant)
15.9.4 Google (Mandiant) Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.10 Group-IB
15.10.1 Company Profile
15.10.2 Main Business and Threat Intelligence Information
15.10.3 SWOT Analysis of Group-IB
15.10.4 Group-IB Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.11 IBM
15.11.1 Company Profile
15.11.2 Main Business and Threat Intelligence Information
15.11.3 SWOT Analysis of IBM
15.11.4 IBM Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
15.12 Intel 471
15.12.1 Company Profile
15.12.2 Main Business and Threat Intelligence Information
15.12.3 SWOT Analysis of Intel 471
15.12.4 Intel 471 Threat Intelligence Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of Threat Intelligence Report
Table Data Sources of Threat Intelligence Report
Table Major Assumptions of Threat Intelligence Report
Table Threat Intelligence Classification
Table Threat Intelligence Applications
Table Drivers of Threat Intelligence Market
Table Restraints of Threat Intelligence Market
Table Opportunities of Threat Intelligence Market
Table Threats of Threat Intelligence Market
Table Raw Materials Suppliers
Table Different Production Methods of Threat Intelligence
Table Cost Structure Analysis of Threat Intelligence
Table Key End Users
Table Latest News of Threat Intelligence Market
Table Merger and Acquisition
Table Planned/Future Project of Threat Intelligence Market
Table Policy of Threat Intelligence Market
Table 2020-2030 North America Threat Intelligence Market Size
Table 2020-2030 North America Threat Intelligence Market Size by Application
Table 2020-2025 North America Threat Intelligence Key Players Revenue
Table 2020-2025 North America Threat Intelligence Key Players Market Share
Table 2020-2030 North America Threat Intelligence Market Size by Type
Table 2020-2030 United States Threat Intelligence Market Size
Table 2020-2030 Canada Threat Intelligence Market Size
Table 2020-2030 Mexico Threat Intelligence Market Size
Table 2020-2030 South America Threat Intelligence Market Size
Table 2020-2030 South America Threat Intelligence Market Size by Application
Table 2020-2025 South America Threat Intelligence Key Players Revenue
Table 2020-2025 South America Threat Intelligence Key Players Market Share
Table 2020-2030 South America Threat Intelligence Market Size by Type
Table 2020-2030 Brazil Threat Intelligence Market Size
Table 2020-2030 Argentina Threat Intelligence Market Size
Table 2020-2030 Chile Threat Intelligence Market Size
Table 2020-2030 Peru Threat Intelligence Market Size
Table 2020-2030 Asia & Pacific Threat Intelligence Market Size
Table 2020-2030 Asia & Pacific Threat Intelligence Market Size by Application
Table 2020-2025 Asia & Pacific Threat Intelligence Key Players Revenue
Table 2020-2025 Asia & Pacific Threat Intelligence Key Players Market Share
Table 2020-2030 Asia & Pacific Threat Intelligence Market Size by Type
Table 2020-2030 China Threat Intelligence Market Size
Table 2020-2030 India Threat Intelligence Market Size
Table 2020-2030 Japan Threat Intelligence Market Size
Table 2020-2030 South Korea Threat Intelligence Market Size
Table 2020-2030 Southeast Asia Threat Intelligence Market Size
Table 2020-2030 Australia Threat Intelligence Market Size
Table 2020-2030 Europe Threat Intelligence Market Size
Table 2020-2030 Europe Threat Intelligence Market Size by Application
Table 2020-2025 Europe Threat Intelligence Key Players Revenue
Table 2020-2025 Europe Threat Intelligence Key Players Market Share
Table 2020-2030 Europe Threat Intelligence Market Size by Type
Table 2020-2030 Germany Threat Intelligence Market Size
Table 2020-2030 France Threat Intelligence Market Size
Table 2020-2030 United Kingdom Threat Intelligence Market Size
Table 2020-2030 Italy Threat Intelligence Market Size
Table 2020-2030 Spain Threat Intelligence Market Size
Table 2020-2030 Belgium Threat Intelligence Market Size
Table 2020-2030 Netherlands Threat Intelligence Market Size
Table 2020-2030 Austria Threat Intelligence Market Size
Table 2020-2030 Poland Threat Intelligence Market Size
Table 2020-2030 Russia Threat Intelligence Market Size
Table 2020-2030 MEA Threat Intelligence Market Size
Table 2020-2030 MEA Threat Intelligence Market Size by Application
Table 2020-2025 MEA Threat Intelligence Key Players Revenue
Table 2020-2025 MEA Threat Intelligence Key Players Market Share
Table 2020-2030 MEA Threat Intelligence Market Size by Type
Table 2020-2030 Egypt Threat Intelligence Market Size
Table 2020-2030 Israel Threat Intelligence Market Size
Table 2020-2030 South Africa Threat Intelligence Market Size
Table 2020-2030 Gulf Cooperation Council Countries Threat Intelligence Market Size
Table 2020-2030 Turkey Threat Intelligence Market Size
Table 2020-2025 Global Threat Intelligence Market Size by Region
Table 2020-2025 Global Threat Intelligence Market Size Share by Region
Table 2020-2025 Global Threat Intelligence Market Size by Application
Table 2020-2025 Global Threat Intelligence Market Share by Application
Table 2020-2025 Global Threat Intelligence Key Vendors Revenue
Table 2020-2025 Global Threat Intelligence Key Vendors Market Share
Table 2020-2025 Global Threat Intelligence Market Size by Type
Table 2020-2025 Global Threat Intelligence Market Share by Type
Table 2025-2030 Global Threat Intelligence Market Size by Region
Table 2025-2030 Global Threat Intelligence Market Size Share by Region
Table 2025-2030 Global Threat Intelligence Market Size by Application
Table 2025-2030 Global Threat Intelligence Market Share by Application
Table 2025-2030 Global Threat Intelligence Key Vendors Revenue
Table 2025-2030 Global Threat Intelligence Key Vendors Market Share
Table 2025-2030 Global Threat Intelligence Market Size by Type
Table 2025-2030 Threat Intelligence Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Threat Intelligence Picture
Figure 2020-2030 North America Threat Intelligence Market Size and CAGR
Figure 2020-2030 South America Threat Intelligence Market Size and CAGR
Figure 2020-2030 Asia & Pacific Threat Intelligence Market Size and CAGR
Figure 2020-2030 Europe Threat Intelligence Market Size and CAGR
Figure 2020-2030 MEA Threat Intelligence Market Size and CAGR
Figure 2020-2025 Global Threat Intelligence Market Size and Growth Rate
Figure 2025-2030 Global Threat Intelligence Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
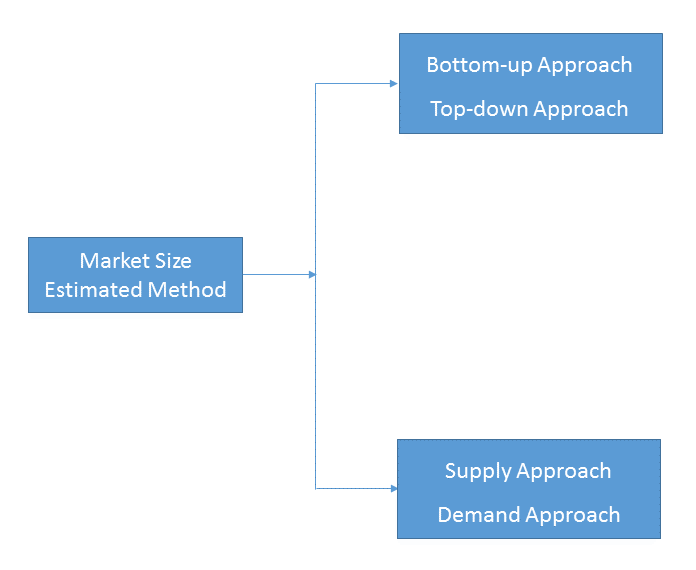
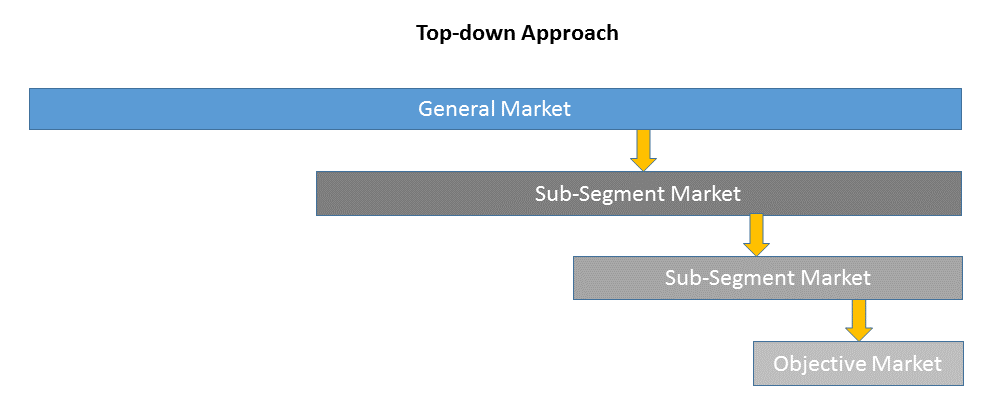
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
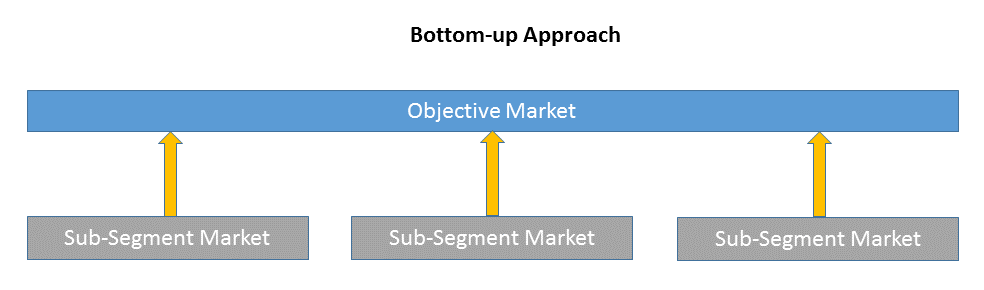
Bottom-up approach size the objective market by collecting the sub-segment information.
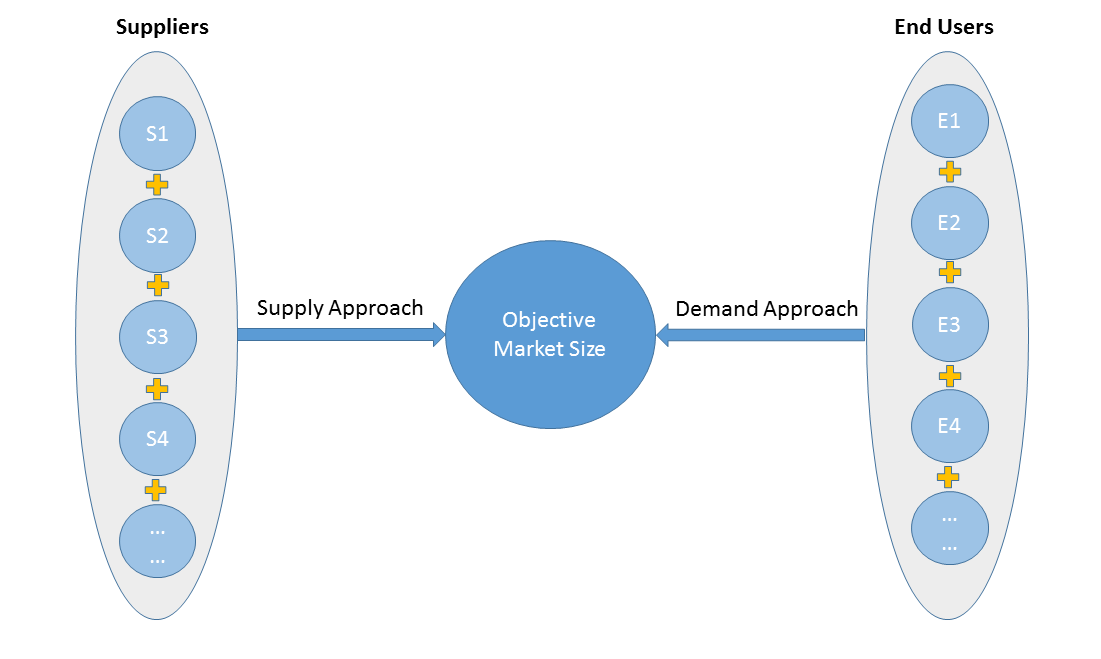
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
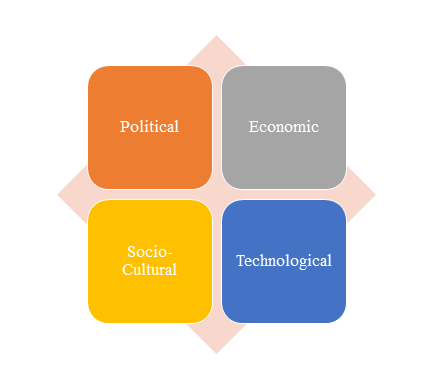
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
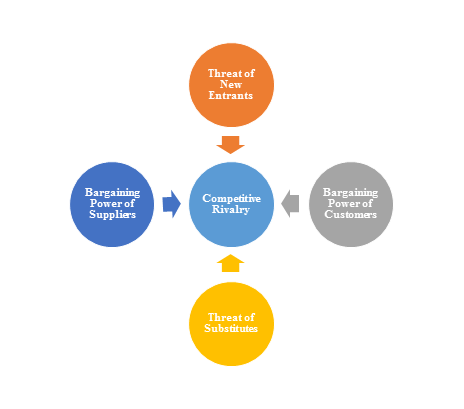
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
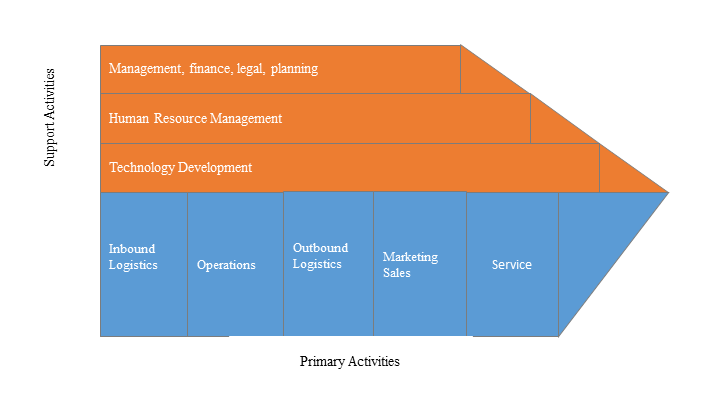
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
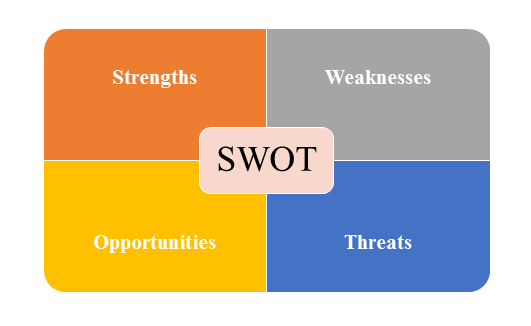
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |