Security Service Edge Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,200
- Team License (2~5 Users) $ 4,200
- Corporate License (>5 Users) $ 5,200
The Security Service Edge (SSE) market embodies a pivotal evolution in cybersecurity architecture, converging essential security functions such as secure web gateways, cloud access security brokers, zero-trust network access, and firewall-as-a-service into a cloud-native delivery model. This framework addresses the limitations of traditional perimeter-based security by enabling consistent protection for distributed workforces, hybrid cloud environments, and remote access scenarios. SSE's core appeal lies in its scalability, reduced latency through edge computing, and integration with broader secure access service edge (SASE) ecosystems, making it indispensable for organizations navigating the complexities of digital transformation. As enterprises increasingly adopt multi-cloud strategies and face escalating threats from ransomware, phishing, and supply chain attacks, SSE provides a unified platform that simplifies policy enforcement, enhances visibility, and minimizes operational overhead. The global SSE market is estimated to reach a valuation of approximately USD 4.0–8.0 billion in 2025, with compound annual growth rates projected in the range of 15%–25% through 2030. This robust expansion is fueled by the proliferation of remote and hybrid work models, stringent data privacy regulations like GDPR and CCPA, and the imperative for resilient defenses against sophisticated cyber adversaries. While the market remains fragmented with varying maturity levels across regions, its strategic importance in fortifying digital perimeters positions it as a high-priority investment for forward-thinking enterprises.
Application Analysis and Market Segmentation
● IT and Telecommunication Applications
The IT and telecommunication sector stands as a cornerstone for SSE adoption, leveraging its capabilities to secure vast networks, protect against distributed denial-of-service (DDoS) attacks, and ensure seamless connectivity in 5G-enabled infrastructures. SSE's zero-trust principles align perfectly with the sector's need for granular access controls and real-time threat intelligence, particularly in managing edge devices and IoT endpoints. This application segment is poised for the most vigorous expansion, with annual growth rates estimated at 25%–28%, propelled by the surge in data traffic from streaming services, cloud migrations, and edge computing deployments. Trends indicate a shift toward AI-infused SSE solutions that automate anomaly detection and predictive threat hunting, enabling telecom providers to offer differentiated managed security services. In mature markets, telecom giants are bundling SSE with SD-WAN for end-to-end visibility, while emerging deployments focus on cost-effective scaling to support rural broadband initiatives.
● BFSI Applications
In the banking, financial services, and insurance (BFSI) domain, SSE serves as a bulwark against financial fraud, insider threats, and compliance breaches, facilitating secure transactions across global branches and digital banking platforms. Its cloud-delivered model supports micro-segmentation and behavioral analytics, crucial for safeguarding sensitive customer data amid rising incidents of account takeovers and API vulnerabilities. The BFSI segment anticipates annual growth rates of 20%–24%, driven by regulatory pressures for continuous monitoring and the integration of SSE with robotic process automation for fraud prevention. Key developments include the adoption of SSE-embedded digital wallets and blockchain-secured ledgers, with financial institutions prioritizing solutions that offer low-latency decryption for encrypted traffic inspection. As fintech disruptors proliferate, traditional banks are accelerating SSE implementations to bridge legacy system gaps, fostering a more agile and resilient financial ecosystem.
● Government & Public Sector Applications
Government entities rely on SSE to protect classified networks, citizen data portals, and critical infrastructure from state-sponsored cyber espionage and ransomware campaigns. By enforcing least-privilege access and integrating with sovereign cloud environments, SSE ensures compliance with frameworks like NIST and FedRAMP, while enabling secure collaboration across agencies. This segment is expected to grow at 18%–22% annually, bolstered by geopolitical tensions and investments in smart city projects that demand robust edge security. Emerging trends highlight the use of SSE for zero-trust architectures in public cloud migrations, with governments in democratic nations emphasizing audit trails and AI-driven incident response to mitigate insider risks. As e-governance expands, SSE's role in securing remote administrative functions and IoT-enabled public services will intensify, promoting transparency and trust in digital public interactions.
● Healthcare Applications
Healthcare organizations deploy SSE to secure electronic health records, telemedicine platforms, and connected medical devices against breaches that could compromise patient privacy and care delivery. Its adaptive access controls and data loss prevention features are vital for HIPAA-compliant environments, where hybrid workforces access sensitive information from diverse endpoints. Growth in this segment is projected at 19%–23% per year, spurred by the digital health boom, including wearable tech and AI diagnostics, which amplify attack surfaces. Developments point to SSE integrations with electronic medical record systems for real-time threat correlation, alongside a focus on ransomware-resistant backups. As telehealth adoption surges post-pandemic, healthcare providers are prioritizing SSE for endpoint protection in under-resourced facilities, enhancing overall sector resilience and accelerating innovation in personalized medicine.
● Retail and e-Commerce Applications
For retail and e-commerce, SSE fortifies online storefronts, supply chain visibility, and customer data flows against card-not-present fraud and botnet-driven disruptions. By inspecting east-west traffic in cloud-native retail platforms, it prevents inventory manipulation and ensures PCI-DSS adherence during peak shopping seasons. The segment forecasts annual growth of 17%–21%, supported by omnichannel strategies and the rise of social commerce, which necessitate agile security for global payment gateways. Trends include SSE-enhanced personalization engines that balance security with user experience, using machine learning to detect anomalous shopping patterns. As e-commerce penetrates emerging markets, retailers are embedding SSE in edge caches to reduce checkout abandonment from security friction, driving sustained revenue growth through trusted digital experiences.
● Manufacturing Applications
Manufacturing leverages SSE to secure industrial control systems, supply chain IoT, and remote operations against operational technology (OT) exploits like Stuxnet variants. Its convergence of IT-OT security provides visibility into factory floors, mitigating downtime from cyber-physical attacks. Expected growth rates stand at 16%–20% annually, aligned with Industry 4.0 initiatives and smart factory rollouts that integrate AI for predictive maintenance. Key evolutions involve SSE platforms with protocol-aware inspection for legacy machinery, enabling safe cloud uplifts without overhauls. As global supply chains digitize, manufacturers are adopting SSE for vendor risk management, fostering collaborative ecosystems while safeguarding intellectual property and production continuity.
● Education Applications
Educational institutions use SSE to protect learning management systems, remote classrooms, and research data from phishing and credential stuffing, ensuring uninterrupted access for students and faculty. Its scalable deployment suits budget-constrained environments, supporting edtech integrations like virtual labs. This segment projects 15%–19% yearly growth, driven by hybrid learning models and rising edtech investments in AI tutoring tools. Trends emphasize SSE for federated identity management across campuses, with a push toward privacy-preserving analytics for student performance tracking. As online education globalizes, institutions are prioritizing SSE to counter region-specific threats, enhancing digital equity and research integrity.
● Other Applications
Miscellaneous uses encompass energy utilities for grid security and media for content delivery protection, with variable growth of 14%–18% annually, contingent on sector-specific digitalization paces. These niches benefit from SSE's modularity, allowing tailored deployments that evolve with emerging threats.
By Component
● Solutions
SSE solutions, encompassing core software platforms and integrated security stacks, dominate with estimated annual growth of 22%–26%, reflecting demand for turnkey deployments that consolidate vendors and streamline operations. Innovations in AI-orchestrated solutions are accelerating adoption, offering automated policy tuning and threat remediation to outpace evolving attack vectors.
● Services
Professional and managed services, including consulting, integration, and ongoing support, are set to expand at 18%–22% per year, as organizations seek expertise to navigate SSE implementations amid skills gaps. Trends favor outcome-based services that include training and optimization, ensuring long-term efficacy in dynamic threat landscapes.
Regional Market Distribution and Geographic Trends
● North America: 18%–22% growth annually, spearheaded by the United States where robust cloud ecosystems and federal mandates drive SSE uptake among Fortune 500 firms and government agencies. Canada complements this with fintech and healthcare digitalization, emphasizing zero-trust for cross-border data flows.
● Asia-Pacific: 22%–26% growth, dominated by China’s state-backed cybersecurity push and India’s burgeoning IT outsourcing sector, where SSE secures hyperscale data centers and e-governance portals. Japan and South Korea focus on manufacturing OT convergence, accelerating regional edge security maturity.
● Europe: 17%–21% growth, with Germany leading in industrial IoT protections and the UK advancing post-Brexit data sovereignty via SSE for financial hubs. France and the Netherlands prioritize privacy-compliant deployments in retail and public sectors.
● Latin America: 16%–20% growth, propelled by Brazil’s e-commerce surge and Mexico’s manufacturing nearshoring, where SSE addresses supply chain vulnerabilities and supports digital inclusion initiatives.
● Middle East & Africa: 15%–19% growth, anchored in the UAE and Saudi Arabia’s Vision 2030 smart city ambitions, alongside South Africa’s BFSI digital transformation, focusing on SSE for oil & gas critical infrastructure and mobile banking security.
Key Market Players and Competitive Landscape
Zscaler emerges as a frontrunner, commanding significant market presence through its cloud-native Zero Trust Exchange platform, which integrates SSE functionalities with over 500 enterprise customers globally, reporting substantial revenue from SSE-driven subscriptions in recent fiscal periods. Cisco bolsters its portfolio via the Umbrella suite, leveraging extensive networking heritage to deliver SSE with seamless SD-WAN integration, appealing to large-scale deployments in telecom and manufacturing. Broadcom, post its VMware acquisition, enhances SSE offerings with advanced endpoint protection, targeting hybrid environments and boasting strong penetration in North American enterprises. Palo Alto Networks dominates with Prisma Access, a comprehensive SSE solution emphasizing AI-powered threat prevention, as highlighted in its annual disclosures showing accelerated adoption in government and healthcare verticals. Netskope differentiates through its NewEdge infrastructure, providing low-latency SSE for global workforces, with a focus on data-centric security that resonates in BFSI and education sectors. Fortinet integrates SSE into its Security Fabric, offering cost-effective unified threat management that gains traction in mid-market manufacturing and retail. Emerging players like Twingate emphasize lightweight zero-trust access, carving niches in remote-first SMBs with agile, subscription-based models. Perimeter 81 streamlines SSE for distributed teams via intuitive dashboards, appealing to European SMEs in e-commerce. Forcepoint advances behavioral analytics in SSE, strengthening insider threat detection for public sector clients. Skyhigh Security (formerly McAfee Enterprise) excels in cloud security posture management within SSE, supporting multi-cloud strategies in IT services. Versa Networks rounds out the landscape with carrier-grade SSE, enabling service providers to white-label solutions for telco expansions in Asia-Pacific.
Industry Value Chain Analysis
The SSE value chain is inherently digital and layered, spanning from foundational cloud infrastructure to end-user orchestration, with value accrual skewed toward innovative providers and integrated service delivery.
Raw Materials and Upstream Supply
Upstream elements revolve around cloud computing resources, including hyperscale data centers, edge nodes, and semiconductor components for AI acceleration. Providers like AWS, Azure, and Google Cloud supply the foundational PoPs (points of presence) essential for SSE's global footprint. Dependency on high-bandwidth optics and secure hardware ensures low-latency delivery, while upstream innovations in quantum-resistant encryption fortify the chain against future threats. Integrated players benefit from economies in spectrum allocation and renewable-powered facilities, mitigating costs and enhancing sustainability.
Production and Processing
Core production involves developing and refining SSE software stacks, incorporating secure web gateways, CASBs, and ZTNA modules with embedded AI for threat analytics. Vendors like Zscaler and Palo Alto Networks invest heavily in R&D for protocol inspection and policy engines, ensuring interoperability with SASE frameworks. Quality controls emphasize scalability testing and compliance certifications, adding premium value through customizable APIs that adapt to vertical-specific needs. This stage's emphasis on open standards fosters ecosystem partnerships, reducing silos in multi-vendor environments.
Distribution and Logistics
Distribution occurs via cloud marketplaces and direct SaaS subscriptions, with channel partners like VARs and MSSPs handling tailored integrations. Global CDN networks enable just-in-time provisioning, minimizing deployment friction for remote setups. Export dynamics favor North American and European hubs supplying Asia-Pacific, where regulatory variances necessitate localized data residency. Reliable SLAs and automated onboarding streamline logistics, supporting subscription renewals and upselling advanced features.
Downstream Processing and Application Integration
● IT and Telecommunication: SSE integrates with SDN controllers for dynamic routing, enhancing visibility in 5G cores.
● BFSI: Embedded in core banking systems for real-time transaction shielding.
● Government & Public Sector: Layered over sovereign clouds for federated access controls.
● Healthcare: Coupled with EHR platforms for encrypted data flows.
● Retail and e-Commerce: Synced with CMS for fraud-proof checkouts.
● Manufacturing: Fused with MES for OT-IT convergence.
● Education: Aligned with LMS for secure virtual collaborations.
● Others: Adapted for utility SCADA or media DRM.
Downstream value amplifies through bespoke configurations, transforming raw SSE into sector-optimized defenses.
End-User Industries
Ultimate consumption resides with enterprises across verticals, where SSE drives ROI via reduced breach costs and operational efficiencies. High-value capture occurs in compliance-heavy sectors, with feedback loops informing upstream enhancements for sustained relevance.
Market Opportunities and Challenges
● Opportunities
The accelerating shift to zero-trust paradigms amid hybrid cloud proliferation presents expansive avenues for SSE providers to capture untapped mid-market segments through affordable, as-a-service models. Asia-Pacific's digital economy boom, coupled with MEA's infrastructure investments, unlocks premium pricing for localized solutions tailored to regulatory nuances. AI and ML integrations offer differentiation in predictive security, enabling proactive defenses that appeal to BFSI and healthcare for advanced threat hunting. Partnerships with telcos for bundled SSE-SD-WAN services can accelerate adoption in IT/telecom, while sustainability-focused edge deployments align with green data center mandates. Niche verticals like education and manufacturing harbor growth via OT security retrofits, fostering innovation in resilient supply chains and remote learning ecosystems.
● Challenges
Intense competition among incumbents risks commoditization, pressuring margins as customers demand vendor consolidation without performance trade-offs. Skills shortages in cybersecurity talent hinder effective SSE orchestration, exacerbating implementation delays in resource-strapped regions like Latin America. Evolving regulations, such as varying data sovereignty rules across Europe and Asia-Pacific, complicate global scaling and raise compliance overheads. Integration complexities with legacy systems pose barriers in manufacturing and government sectors, where brownfield environments resist seamless zero-trust shifts. Supply chain disruptions in upstream cloud hardware could inflate costs, while the rapid pace of threat innovation outstrips SSE evolution, demanding continuous R&D investments that strain smaller players.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Security Service Edge Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Security Service Edge Market in North America (2020-2030)
8.1 Security Service Edge Market Size
8.2 Security Service Edge Market by End Use
8.3 Competition by Players/Suppliers
8.4 Security Service Edge Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Security Service Edge Market in South America (2020-2030)
9.1 Security Service Edge Market Size
9.2 Security Service Edge Market by End Use
9.3 Competition by Players/Suppliers
9.4 Security Service Edge Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Security Service Edge Market in Asia & Pacific (2020-2030)
10.1 Security Service Edge Market Size
10.2 Security Service Edge Market by End Use
10.3 Competition by Players/Suppliers
10.4 Security Service Edge Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Security Service Edge Market in Europe (2020-2030)
11.1 Security Service Edge Market Size
11.2 Security Service Edge Market by End Use
11.3 Competition by Players/Suppliers
11.4 Security Service Edge Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Security Service Edge Market in MEA (2020-2030)
12.1 Security Service Edge Market Size
12.2 Security Service Edge Market by End Use
12.3 Competition by Players/Suppliers
12.4 Security Service Edge Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Security Service Edge Market (2020-2025)
13.1 Security Service Edge Market Size
13.2 Security Service Edge Market by End Use
13.3 Competition by Players/Suppliers
13.4 Security Service Edge Market Size by Type
Chapter 14 Global Security Service Edge Market Forecast (2025-2030)
14.1 Security Service Edge Market Size Forecast
14.2 Security Service Edge Application Forecast
14.3 Competition by Players/Suppliers
14.4 Security Service Edge Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Zscaler
15.1.1 Company Profile
15.1.2 Main Business and Security Service Edge Information
15.1.3 SWOT Analysis of Zscaler
15.1.4 Zscaler Security Service Edge Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 Cisco
15.2.1 Company Profile
15.2.2 Main Business and Security Service Edge Information
15.2.3 SWOT Analysis of Cisco
15.2.4 Cisco Security Service Edge Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 Broadcom
15.3.1 Company Profile
15.3.2 Main Business and Security Service Edge Information
15.3.3 SWOT Analysis of Broadcom
15.3.4 Broadcom Security Service Edge Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 Palo Alto Networks
15.4.1 Company Profile
15.4.2 Main Business and Security Service Edge Information
15.4.3 SWOT Analysis of Palo Alto Networks
15.4.4 Palo Alto Networks Security Service Edge Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 Netskope
15.5.1 Company Profile
15.5.2 Main Business and Security Service Edge Information
15.5.3 SWOT Analysis of Netskope
15.5.4 Netskope Security Service Edge Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 Fortinet
15.6.1 Company Profile
15.6.2 Main Business and Security Service Edge Information
15.6.3 SWOT Analysis of Fortinet
15.6.4 Fortinet Security Service Edge Sales, Revenue, Price and Gross Margin (2020-2025)
15.7 Twingate
15.7.1 Company Profile
15.7.2 Main Business and Security Service Edge Information
15.7.3 SWOT Analysis of Twingate
15.7.4 Twingate Security Service Edge Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of Security Service Edge Report
Table Data Sources of Security Service Edge Report
Table Major Assumptions of Security Service Edge Report
Table Security Service Edge Classification
Table Security Service Edge Applications
Table Drivers of Security Service Edge Market
Table Restraints of Security Service Edge Market
Table Opportunities of Security Service Edge Market
Table Threats of Security Service Edge Market
Table Raw Materials Suppliers
Table Different Production Methods of Security Service Edge
Table Cost Structure Analysis of Security Service Edge
Table Key End Users
Table Latest News of Security Service Edge Market
Table Merger and Acquisition
Table Planned/Future Project of Security Service Edge Market
Table Policy of Security Service Edge Market
Table 2020-2030 North America Security Service Edge Market Size
Table 2020-2030 North America Security Service Edge Market Size by Application
Table 2020-2025 North America Security Service Edge Key Players Revenue
Table 2020-2025 North America Security Service Edge Key Players Market Share
Table 2020-2030 North America Security Service Edge Market Size by Type
Table 2020-2030 United States Security Service Edge Market Size
Table 2020-2030 Canada Security Service Edge Market Size
Table 2020-2030 Mexico Security Service Edge Market Size
Table 2020-2030 South America Security Service Edge Market Size
Table 2020-2030 South America Security Service Edge Market Size by Application
Table 2020-2025 South America Security Service Edge Key Players Revenue
Table 2020-2025 South America Security Service Edge Key Players Market Share
Table 2020-2030 South America Security Service Edge Market Size by Type
Table 2020-2030 Brazil Security Service Edge Market Size
Table 2020-2030 Argentina Security Service Edge Market Size
Table 2020-2030 Chile Security Service Edge Market Size
Table 2020-2030 Peru Security Service Edge Market Size
Table 2020-2030 Asia & Pacific Security Service Edge Market Size
Table 2020-2030 Asia & Pacific Security Service Edge Market Size by Application
Table 2020-2025 Asia & Pacific Security Service Edge Key Players Revenue
Table 2020-2025 Asia & Pacific Security Service Edge Key Players Market Share
Table 2020-2030 Asia & Pacific Security Service Edge Market Size by Type
Table 2020-2030 China Security Service Edge Market Size
Table 2020-2030 India Security Service Edge Market Size
Table 2020-2030 Japan Security Service Edge Market Size
Table 2020-2030 South Korea Security Service Edge Market Size
Table 2020-2030 Southeast Asia Security Service Edge Market Size
Table 2020-2030 Australia Security Service Edge Market Size
Table 2020-2030 Europe Security Service Edge Market Size
Table 2020-2030 Europe Security Service Edge Market Size by Application
Table 2020-2025 Europe Security Service Edge Key Players Revenue
Table 2020-2025 Europe Security Service Edge Key Players Market Share
Table 2020-2030 Europe Security Service Edge Market Size by Type
Table 2020-2030 Germany Security Service Edge Market Size
Table 2020-2030 France Security Service Edge Market Size
Table 2020-2030 United Kingdom Security Service Edge Market Size
Table 2020-2030 Italy Security Service Edge Market Size
Table 2020-2030 Spain Security Service Edge Market Size
Table 2020-2030 Belgium Security Service Edge Market Size
Table 2020-2030 Netherlands Security Service Edge Market Size
Table 2020-2030 Austria Security Service Edge Market Size
Table 2020-2030 Poland Security Service Edge Market Size
Table 2020-2030 Russia Security Service Edge Market Size
Table 2020-2030 MEA Security Service Edge Market Size
Table 2020-2030 MEA Security Service Edge Market Size by Application
Table 2020-2025 MEA Security Service Edge Key Players Revenue
Table 2020-2025 MEA Security Service Edge Key Players Market Share
Table 2020-2030 MEA Security Service Edge Market Size by Type
Table 2020-2030 Egypt Security Service Edge Market Size
Table 2020-2030 Israel Security Service Edge Market Size
Table 2020-2030 South Africa Security Service Edge Market Size
Table 2020-2030 Gulf Cooperation Council Countries Security Service Edge Market Size
Table 2020-2030 Turkey Security Service Edge Market Size
Table 2020-2025 Global Security Service Edge Market Size by Region
Table 2020-2025 Global Security Service Edge Market Size Share by Region
Table 2020-2025 Global Security Service Edge Market Size by Application
Table 2020-2025 Global Security Service Edge Market Share by Application
Table 2020-2025 Global Security Service Edge Key Vendors Revenue
Table 2020-2025 Global Security Service Edge Key Vendors Market Share
Table 2020-2025 Global Security Service Edge Market Size by Type
Table 2020-2025 Global Security Service Edge Market Share by Type
Table 2025-2030 Global Security Service Edge Market Size by Region
Table 2025-2030 Global Security Service Edge Market Size Share by Region
Table 2025-2030 Global Security Service Edge Market Size by Application
Table 2025-2030 Global Security Service Edge Market Share by Application
Table 2025-2030 Global Security Service Edge Key Vendors Revenue
Table 2025-2030 Global Security Service Edge Key Vendors Market Share
Table 2025-2030 Global Security Service Edge Market Size by Type
Table 2025-2030 Security Service Edge Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Security Service Edge Picture
Figure 2020-2030 North America Security Service Edge Market Size and CAGR
Figure 2020-2030 South America Security Service Edge Market Size and CAGR
Figure 2020-2030 Asia & Pacific Security Service Edge Market Size and CAGR
Figure 2020-2030 Europe Security Service Edge Market Size and CAGR
Figure 2020-2030 MEA Security Service Edge Market Size and CAGR
Figure 2020-2025 Global Security Service Edge Market Size and Growth Rate
Figure 2025-2030 Global Security Service Edge Market Size and Growth Rate
Research Methodology
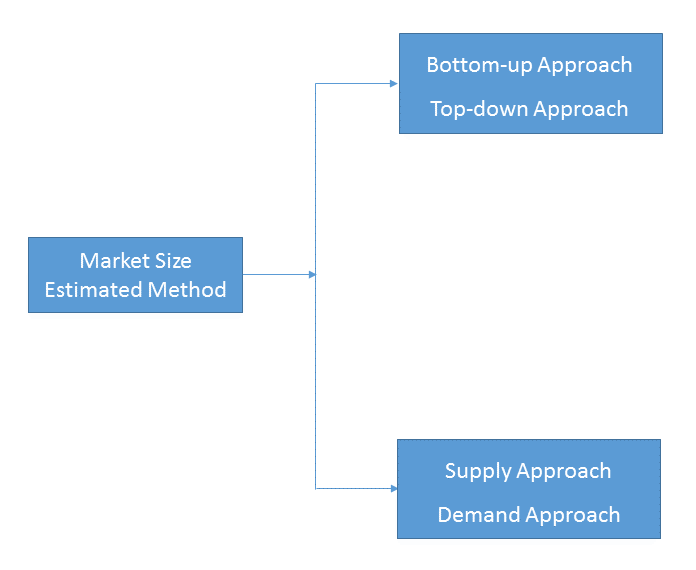
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
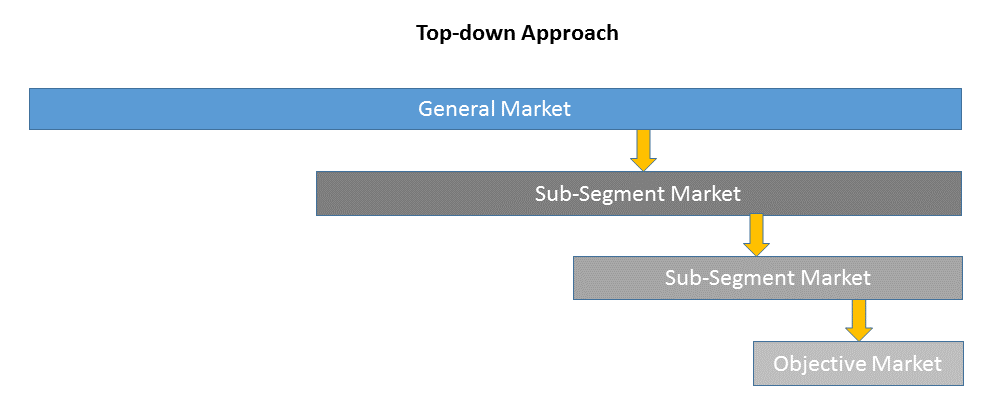
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
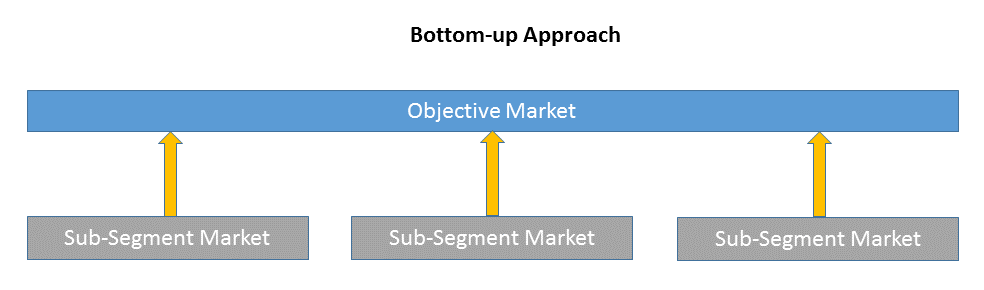
Bottom-up approach size the objective market by collecting the sub-segment information.
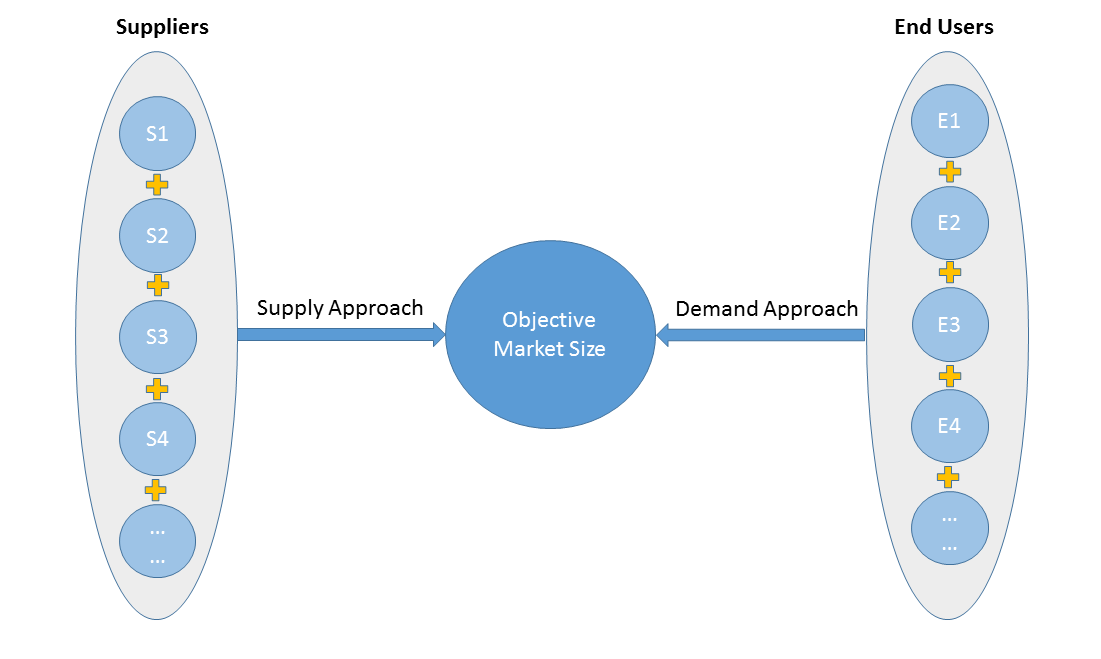
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
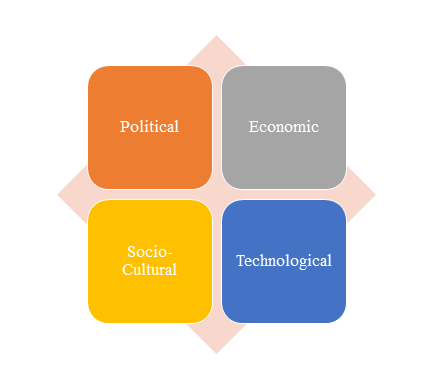
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
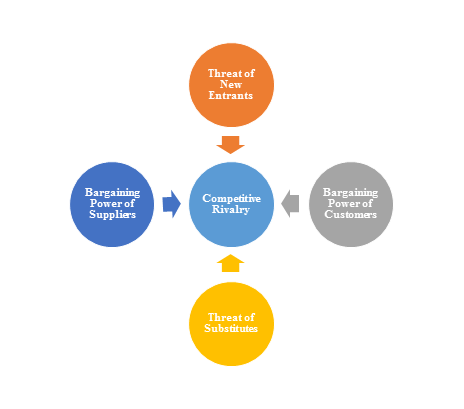
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
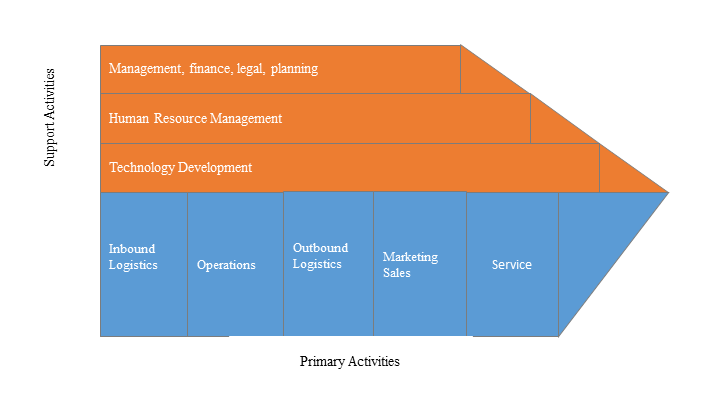
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
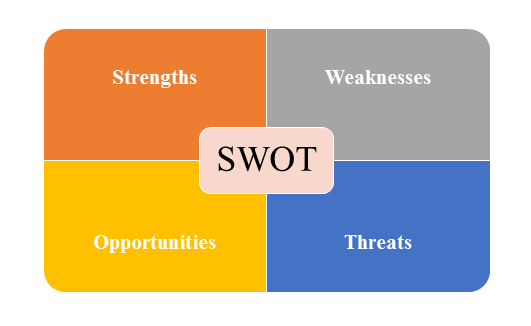
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |