Ransomware Protection Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,200
- Team License (2~5 Users) $ 4,200
- Corporate License (>5 Users) $ 5,200
The Ransomware Protection market stands as a critical pillar in the cybersecurity domain, addressing the escalating menace of malicious software that encrypts data and demands payment for decryption, often leading to operational paralysis and financial devastation. This sector encompasses advanced detection, prevention, and recovery mechanisms, including endpoint security, backup immutability, and threat intelligence, tailored to fortify digital infrastructures against sophisticated attacks. Distinguished by its proactive, multi-layered approach—integrating AI-driven anomaly detection, behavioral analysis, and automated response—ransomware protection mitigates risks in an era of hybrid work, cloud proliferation, and geopolitical cyber tensions. As attackers evolve with tactics like double extortion and supply chain compromises, the market's emphasis on resilience, compliance, and zero-trust principles ensures continuity for organizations. The global Ransomware Protection market is estimated to reach a valuation of approximately USD 20–30 billion in 2025, with compound annual growth rates projected in the range of 11.0%–16.0% through 2030. Momentum stems from surging attack volumes, regulatory mandates for data safeguarding, and the integration of generative AI for predictive defenses, underscoring its indispensable role in safeguarding critical assets.
Application Analysis and Market Segmentation
● BFSI Applications
In banking, financial services, and insurance (BFSI), ransomware protection is paramount due to the sector's high-value data and regulatory scrutiny, employing solutions like air-gapped backups and real-time monitoring to prevent fund disruptions. This segment's growth at 12%–15% annually reflects rising digital transactions and compliance needs under frameworks like PCI-DSS. Trends favor AI-enhanced fraud correlation, with immutable storage thwarting encryption attempts, enabling seamless recovery and maintaining trust in fintech ecosystems.
● IT & Telecom Applications
IT and telecom firms rely on ransomware defenses for network integrity, using endpoint detection and response (EDR) to shield vast infrastructures. Projected to grow at 11%–14%, driven by 5G vulnerabilities, the focus is on scalable, cloud-native tools. Developments include automated orchestration for incident isolation, addressing supply chain risks prevalent in telecom hardware.
● Government & Defense Applications
Public sector entities prioritize sovereign data protection through hardened perimeters and threat hunting, with growth estimated at 10%–13% amid nation-state threats. Trends emphasize federated intelligence sharing and quantum-resistant encryption, ensuring operational continuity in defense networks.
● Healthcare & Life Sciences Applications
Healthcare's sensitive patient data demands HIPAA-compliant recovery, with ransomware often targeting EHR systems. This area anticipates 13%–16% growth, fueled by telehealth expansions. Innovations like biometric-secured backups and AI triage for attack vectors mitigate downtime in life-critical environments.
● Education Applications
Educational institutions protect learning platforms with affordable, user-friendly solutions, growing at 9%–12% as remote education persists. Trends include gamified training modules and endpoint hardening for student devices.
● Retail/Consumer Goods Applications
Retail leverages protection for e-commerce resilience, with 11%–14% growth from omnichannel threats. Location-agnostic backups and behavioral analytics counter peak-season attacks.
● Energy & Utilities Applications
Critical infrastructure in energy demands OT/IT convergence for protection, expanding at 12%–15%. Trends focus on SCADA-secure immutability against disruptive outages.
● Media & Entertainment Applications
Content creators safeguard IP with cloud-focused defenses, at 10%–13% growth. Streaming-optimized recovery ensures minimal disruption.
● Others Applications
Varied sectors like manufacturing see 9%–12% growth, with customized hybrid solutions addressing niche vulnerabilities.
● Solutions Component
Solutions, including software and appliances, lead with proactive features like machine learning classifiers, growing at 12%–15%. Trends highlight integrated platforms blending prevention and forensics.
● Services Component
Professional services for consulting and managed detection grow at 10%–13%, emphasizing training and 24/7 response to build organizational maturity.
Regional Market Distribution and Geographic Trends
● Asia-Pacific: 13%–16% growth annually, led by China's state-backed cyber initiatives and India's digital economy boom, where BFSI and healthcare digitize rapidly.
● North America: 11%–14% growth, dominated by U.S. regulatory pushes like CISA guidelines, with enterprises fortifying cloud migrations.
● Europe: 10%–13% growth, driven by GDPR enforcement in Germany and France, focusing on cross-border data flows.
● Latin America: 12%–15% growth, with Brazil and Mexico advancing telecom and retail protections amid rising attacks.
● Middle East & Africa: 11.5%–14.5% growth, supported by UAE's smart city defenses and South Africa's financial sector resilience.
Key Market Players and Competitive Landscape
● CrowdStrike Holdings Inc. – A leader in EDR, CrowdStrike's Falcon platform excels in AI-powered ransomware blocking, contributing significantly to its $3+ billion 2024 ARR amid cloud security surges.
● SentinelOne Inc. – Specializing in autonomous defenses, SentinelOne's Singularity integrates recovery, driving 40%+ YoY growth in its FY2024 revenues over $600 million.
● Zerto – Focused on replication for continuity, Zerto's hypervisor-agnostic solutions bolster VMware integrations, enhancing HPE's portfolio post-acquisition.
● Acronis International GmbH – Offering cyber protection suites with backup immutability, Acronis reports robust SMB adoption, integral to its diversified cybersecurity revenues.
● Bitdefender – Renowned for gravityzone endpoint security, Bitdefender's layered defenses target healthcare, with steady enterprise expansions.
● Kaspersky Lab – Providing global threat intelligence, Kaspersky's solutions emphasize multi-vector protection, navigating geopolitical challenges.
● Sophos Ltd. – Intercept X features adaptive ransomware rollback, supporting its MSP-focused model in growing services revenues.
● Malwarebytes Inc. – Specializing in remediation, Malwarebytes' Nebula platform aids rapid recovery for mid-market.
● McAfee Corp. – MVISION integrates AI for prediction, bolstering Trellix's post-merger portfolio.
● Trend Micro Inc. – Apex One delivers behavioral analysis, key to its Asia-Pacific stronghold.
● Palo Alto Networks Inc. – Cortex XDR unifies detection, driving its $8+ billion 2024 revenues.
● Cisco Systems Inc. – SecureX orchestrates responses, leveraging networking synergies.
Industry Value Chain Analysis
The ransomware protection value chain is defense-oriented, from intelligence gathering to resilient recovery, with value amplified in integrated, automated layers.
Raw Materials and Upstream Supply
Threat feeds and hardware like secure chips form the base, sourced from intel firms and semiconductor leaders. Integrated providers like Palo Alto benefit from in-house R&D, optimizing sensor data flows.
Production and Processing
Development involves algorithm tuning for detection engines and compliance certification. Quality hinges on false-positive minimization, with AI simulations ensuring robustness.
Distribution and Logistics
Cloud marketplaces and partner channels enable rapid deployment, with SLAs guaranteeing uptime. Global logistics prioritize encrypted updates to counter supply disruptions.
Downstream Processing and Application Integration
● BFSI: Embedded in transaction gateways for real-time halts.
● Healthcare: Layered into EHR for segmented recovery.
Integration adds forensic value, turning incidents into intelligence.
End-User Industries
Critical sectors like government extract maximum ROI through minimized downtime, with services enhancing long-term posture.
Market Opportunities and Challenges
● Opportunities
AI advancements enable predictive blocking in cloud-heavy environments, especially Asia-Pacific's digitization. Regulatory waves like NIS2 spur demand for compliant services, while SMB-focused bundles open untapped markets. Zero-trust integrations with IoT offer premium upsell paths.
● Challenges
Evolving attacker tactics, including AI-phishing, outpace defenses, demanding continuous R&D. Skill shortages hinder adoption, with integration complexities in legacy systems inflating costs. Geopolitical bans fragment supply chains, while alert fatigue burdens SOC teams.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Ransomware Protection Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Ransomware Protection Market in North America (2020-2030)
8.1 Ransomware Protection Market Size
8.2 Ransomware Protection Market by End Use
8.3 Competition by Players/Suppliers
8.4 Ransomware Protection Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Ransomware Protection Market in South America (2020-2030)
9.1 Ransomware Protection Market Size
9.2 Ransomware Protection Market by End Use
9.3 Competition by Players/Suppliers
9.4 Ransomware Protection Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Ransomware Protection Market in Asia & Pacific (2020-2030)
10.1 Ransomware Protection Market Size
10.2 Ransomware Protection Market by End Use
10.3 Competition by Players/Suppliers
10.4 Ransomware Protection Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Ransomware Protection Market in Europe (2020-2030)
11.1 Ransomware Protection Market Size
11.2 Ransomware Protection Market by End Use
11.3 Competition by Players/Suppliers
11.4 Ransomware Protection Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Ransomware Protection Market in MEA (2020-2030)
12.1 Ransomware Protection Market Size
12.2 Ransomware Protection Market by End Use
12.3 Competition by Players/Suppliers
12.4 Ransomware Protection Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Ransomware Protection Market (2020-2025)
13.1 Ransomware Protection Market Size
13.2 Ransomware Protection Market by End Use
13.3 Competition by Players/Suppliers
13.4 Ransomware Protection Market Size by Type
Chapter 14 Global Ransomware Protection Market Forecast (2025-2030)
14.1 Ransomware Protection Market Size Forecast
14.2 Ransomware Protection Application Forecast
14.3 Competition by Players/Suppliers
14.4 Ransomware Protection Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 CrowdStrike Holdings Inc.
15.1.1 Company Profile
15.1.2 Main Business and Ransomware Protection Information
15.1.3 SWOT Analysis of CrowdStrike Holdings Inc.
15.1.4 CrowdStrike Holdings Inc. Ransomware Protection Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 SentinelOne Inc.
15.2.1 Company Profile
15.2.2 Main Business and Ransomware Protection Information
15.2.3 SWOT Analysis of SentinelOne Inc.
15.2.4 SentinelOne Inc. Ransomware Protection Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 Zerto
15.3.1 Company Profile
15.3.2 Main Business and Ransomware Protection Information
15.3.3 SWOT Analysis of Zerto
15.3.4 Zerto Ransomware Protection Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 Acronis International GmbH
15.4.1 Company Profile
15.4.2 Main Business and Ransomware Protection Information
15.4.3 SWOT Analysis of Acronis International GmbH
15.4.4 Acronis International GmbH Ransomware Protection Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 Bitdefender
15.5.1 Company Profile
15.5.2 Main Business and Ransomware Protection Information
15.5.3 SWOT Analysis of Bitdefender
15.5.4 Bitdefender Ransomware Protection Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 Kaspersky Lab
15.6.1 Company Profile
15.6.2 Main Business and Ransomware Protection Information
15.6.3 SWOT Analysis of Kaspersky Lab
15.6.4 Kaspersky Lab Ransomware Protection Sales, Revenue, Price and Gross Margin (2020-2025)
15.7 Sophos Ltd.
15.7.1 Company Profile
15.7.2 Main Business and Ransomware Protection Information
15.7.3 SWOT Analysis of Sophos Ltd.
15.7.4 Sophos Ltd. Ransomware Protection Sales, Revenue, Price and Gross Margin (2020-2025)
15.8 Malwarebytes Inc.
15.8.1 Company Profile
15.8.2 Main Business and Ransomware Protection Information
15.8.3 SWOT Analysis of Malwarebytes Inc.
15.8.4 Malwarebytes Inc. Ransomware Protection Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of Ransomware Protection Report
Table Data Sources of Ransomware Protection Report
Table Major Assumptions of Ransomware Protection Report
Table Ransomware Protection Classification
Table Ransomware Protection Applications
Table Drivers of Ransomware Protection Market
Table Restraints of Ransomware Protection Market
Table Opportunities of Ransomware Protection Market
Table Threats of Ransomware Protection Market
Table Raw Materials Suppliers
Table Different Production Methods of Ransomware Protection
Table Cost Structure Analysis of Ransomware Protection
Table Key End Users
Table Latest News of Ransomware Protection Market
Table Merger and Acquisition
Table Planned/Future Project of Ransomware Protection Market
Table Policy of Ransomware Protection Market
Table 2020-2030 North America Ransomware Protection Market Size
Table 2020-2030 North America Ransomware Protection Market Size by Application
Table 2020-2025 North America Ransomware Protection Key Players Revenue
Table 2020-2025 North America Ransomware Protection Key Players Market Share
Table 2020-2030 North America Ransomware Protection Market Size by Type
Table 2020-2030 United States Ransomware Protection Market Size
Table 2020-2030 Canada Ransomware Protection Market Size
Table 2020-2030 Mexico Ransomware Protection Market Size
Table 2020-2030 South America Ransomware Protection Market Size
Table 2020-2030 South America Ransomware Protection Market Size by Application
Table 2020-2025 South America Ransomware Protection Key Players Revenue
Table 2020-2025 South America Ransomware Protection Key Players Market Share
Table 2020-2030 South America Ransomware Protection Market Size by Type
Table 2020-2030 Brazil Ransomware Protection Market Size
Table 2020-2030 Argentina Ransomware Protection Market Size
Table 2020-2030 Chile Ransomware Protection Market Size
Table 2020-2030 Peru Ransomware Protection Market Size
Table 2020-2030 Asia & Pacific Ransomware Protection Market Size
Table 2020-2030 Asia & Pacific Ransomware Protection Market Size by Application
Table 2020-2025 Asia & Pacific Ransomware Protection Key Players Revenue
Table 2020-2025 Asia & Pacific Ransomware Protection Key Players Market Share
Table 2020-2030 Asia & Pacific Ransomware Protection Market Size by Type
Table 2020-2030 China Ransomware Protection Market Size
Table 2020-2030 India Ransomware Protection Market Size
Table 2020-2030 Japan Ransomware Protection Market Size
Table 2020-2030 South Korea Ransomware Protection Market Size
Table 2020-2030 Southeast Asia Ransomware Protection Market Size
Table 2020-2030 Australia Ransomware Protection Market Size
Table 2020-2030 Europe Ransomware Protection Market Size
Table 2020-2030 Europe Ransomware Protection Market Size by Application
Table 2020-2025 Europe Ransomware Protection Key Players Revenue
Table 2020-2025 Europe Ransomware Protection Key Players Market Share
Table 2020-2030 Europe Ransomware Protection Market Size by Type
Table 2020-2030 Germany Ransomware Protection Market Size
Table 2020-2030 France Ransomware Protection Market Size
Table 2020-2030 United Kingdom Ransomware Protection Market Size
Table 2020-2030 Italy Ransomware Protection Market Size
Table 2020-2030 Spain Ransomware Protection Market Size
Table 2020-2030 Belgium Ransomware Protection Market Size
Table 2020-2030 Netherlands Ransomware Protection Market Size
Table 2020-2030 Austria Ransomware Protection Market Size
Table 2020-2030 Poland Ransomware Protection Market Size
Table 2020-2030 Russia Ransomware Protection Market Size
Table 2020-2030 MEA Ransomware Protection Market Size
Table 2020-2030 MEA Ransomware Protection Market Size by Application
Table 2020-2025 MEA Ransomware Protection Key Players Revenue
Table 2020-2025 MEA Ransomware Protection Key Players Market Share
Table 2020-2030 MEA Ransomware Protection Market Size by Type
Table 2020-2030 Egypt Ransomware Protection Market Size
Table 2020-2030 Israel Ransomware Protection Market Size
Table 2020-2030 South Africa Ransomware Protection Market Size
Table 2020-2030 Gulf Cooperation Council Countries Ransomware Protection Market Size
Table 2020-2030 Turkey Ransomware Protection Market Size
Table 2020-2025 Global Ransomware Protection Market Size by Region
Table 2020-2025 Global Ransomware Protection Market Size Share by Region
Table 2020-2025 Global Ransomware Protection Market Size by Application
Table 2020-2025 Global Ransomware Protection Market Share by Application
Table 2020-2025 Global Ransomware Protection Key Vendors Revenue
Table 2020-2025 Global Ransomware Protection Key Vendors Market Share
Table 2020-2025 Global Ransomware Protection Market Size by Type
Table 2020-2025 Global Ransomware Protection Market Share by Type
Table 2025-2030 Global Ransomware Protection Market Size by Region
Table 2025-2030 Global Ransomware Protection Market Size Share by Region
Table 2025-2030 Global Ransomware Protection Market Size by Application
Table 2025-2030 Global Ransomware Protection Market Share by Application
Table 2025-2030 Global Ransomware Protection Key Vendors Revenue
Table 2025-2030 Global Ransomware Protection Key Vendors Market Share
Table 2025-2030 Global Ransomware Protection Market Size by Type
Table 2025-2030 Ransomware Protection Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Ransomware Protection Picture
Figure 2020-2030 North America Ransomware Protection Market Size and CAGR
Figure 2020-2030 South America Ransomware Protection Market Size and CAGR
Figure 2020-2030 Asia & Pacific Ransomware Protection Market Size and CAGR
Figure 2020-2030 Europe Ransomware Protection Market Size and CAGR
Figure 2020-2030 MEA Ransomware Protection Market Size and CAGR
Figure 2020-2025 Global Ransomware Protection Market Size and Growth Rate
Figure 2025-2030 Global Ransomware Protection Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
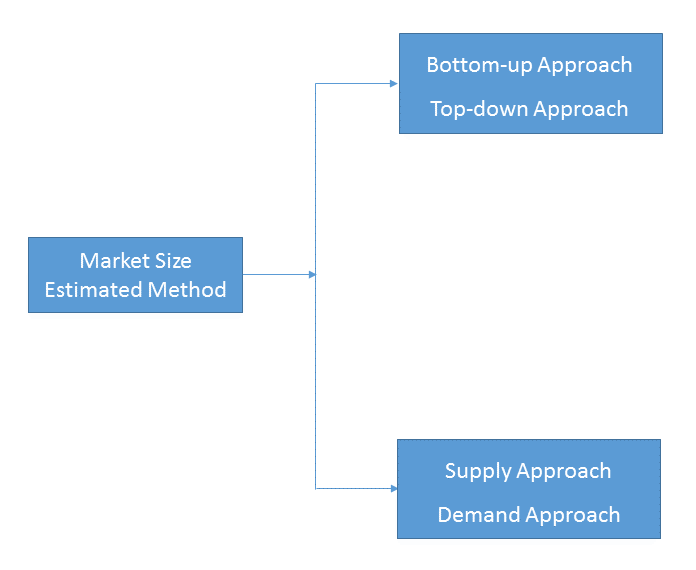
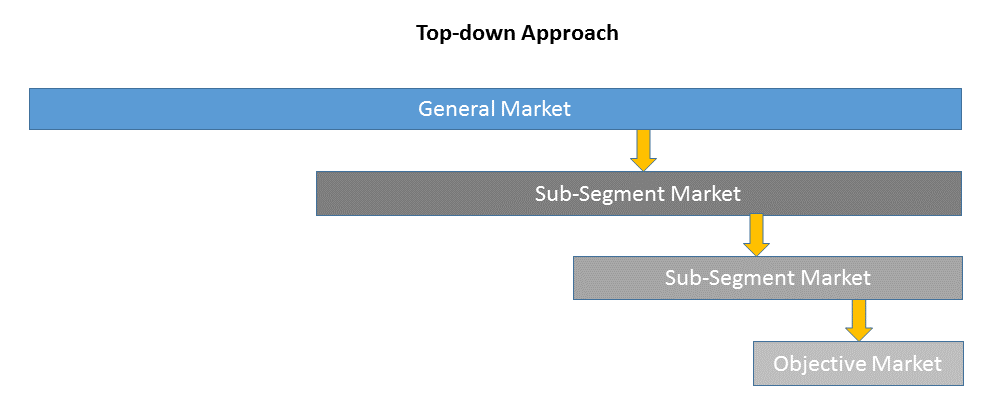
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
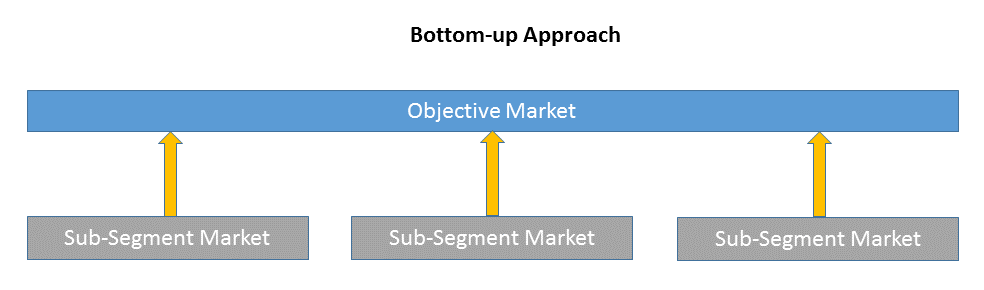
Bottom-up approach size the objective market by collecting the sub-segment information.
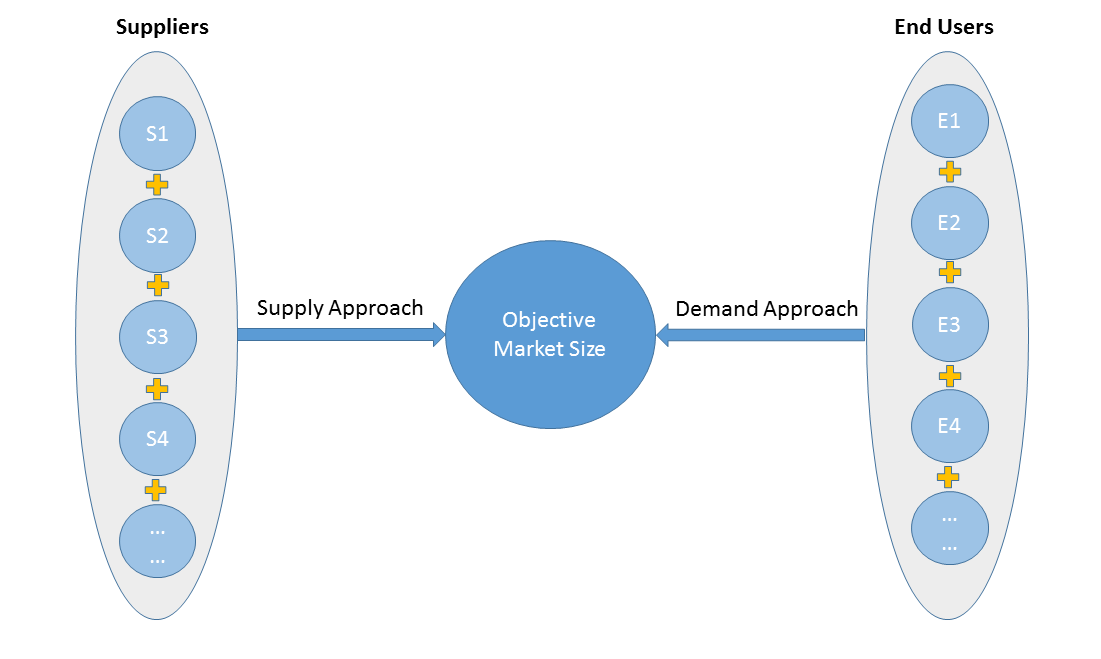
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
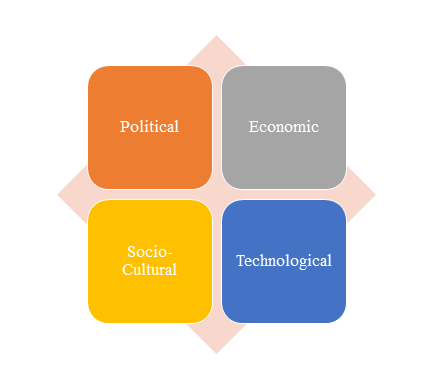
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
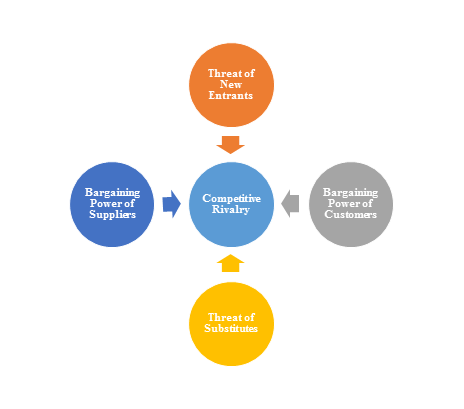
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
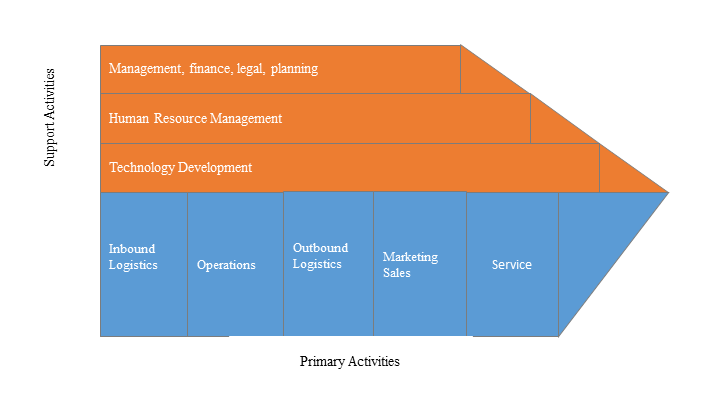
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
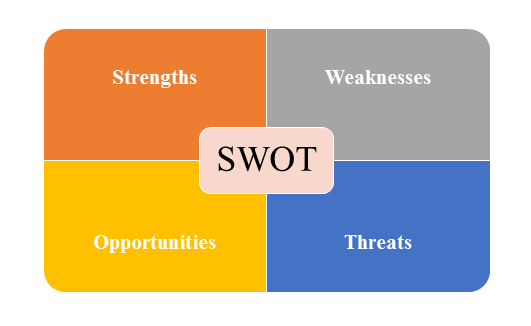
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |