Post-quantum Cryptography Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,200
- Team License (2~5 Users) $ 4,200
- Corporate License (>5 Users) $ 5,200
Post-quantum cryptography (PQC) emerges as a critical safeguard in the cybersecurity landscape, engineering mathematical foundations resilient to quantum computational threats that could shatter conventional encryption paradigms. Unlike classical cryptography reliant on problems like integer factorization, PQC leverages structures such as lattices, error-correcting codes, and hash functions, presumed intractable even for quantum adversaries wielding Shor's or Grover's algorithms. This paradigm shift is imperative as quantum supremacy looms, with prototypes already demonstrating exponential speedups in factorization tasks, endangering RSA and ECC-based systems ubiquitous in digital infrastructure. PQC's hallmark is its dual assurance: maintaining backward compatibility while fortifying against "harvest now, decrypt later" exploits, where adversaries amass encrypted data for future quantum decryption. Beyond mere encryption, PQC underpins secure communications, digital signatures, and key exchanges, ensuring trust in an era of pervasive connectivity. Its deployment spans hardware-accelerated chips to software libraries, fostering a quantum-safe continuum from endpoints to hyperscale clouds. The global PQC market is on track to achieve between USD 400 million and USD 1 billion by 2025, propelled by regulatory imperatives and escalating cyber risks. Concurrently, the industry eyes a CAGR of 20.0%–40.0% to 2030, underscoring PQC's ascent as enterprises fortify against quantum disruptions while capitalizing on hybrid classical-quantum synergies.
Industry Characteristics
PQC architectures are defined by their mathematical diversity, blending lattice-based schemes for key encapsulation with code-based paradigms for error-resilient encryption, ensuring no single vulnerability undermines the ecosystem. Primitives like CRYSTALS-Kyber exemplify this, harnessing learning-with-errors problems for asymmetric security, while hash-based signatures like SPHINCS+ provide stateless resilience. The sector's hallmark is crypto-agility: modular designs permitting seamless algorithm swaps without infrastructural overhauls, vital for legacy migrations. Standardization bodies like NIST validate these through rigorous cryptanalysis, yielding FIPS-compliant hybrids that interweave classical and quantum-resistant layers. PQC's maturity manifests in optimized implementations—ASICs slashing latency by 50%—yet demands quantum-safe RNGs to thwart Grover-accelerated brute-forcing. Compared to legacy crypto, PQC's larger key sizes inflate bandwidth 2–4x, spurring compression innovations, but its post-quantum security proofs eclipse RSA's heuristics. In fintech and defense, PQC's forward secrecy thwarts retroactive breaches, while its auditability bolsters compliance. As quantum error correction matures, PQC evolves toward fault-tolerant hybrids, positioning it as the bedrock of secure quantum networks and distributed ledgers.
Regional Market Trends
PQC's trajectory varies by region, mirroring cybersecurity maturity and quantum investments. North America's market growth is pegged at 18.0%–35.0% through 2030, led by U.S. dominance via NIST's standardization vanguard. Agencies like NSA mandate PQC migration by 2033, spurring federal contracts in defense, where lattice-based pilots secure classified comms. Canada's quantum hubs in Waterloo amplify R&D, with firms like evolutionQ pioneering hybrid chips.
Europe's PQC ecosystem forecasts 17.0%–32.0% CAGR, anchored by ETSI's quantum-safe frameworks. Germany's BSI drives automotive adoption, embedding PQC in V2X protocols, while France's ANSSI enforces hybrid mandates in finance. The U.K.'s NCSC pilots code-based signatures for NHS data vaults, balancing GDPR with quantum resilience.
Asia-Pacific surges with 22.0%–38.0% growth, propelled by China's quantum supremacy ambitions. Singapore's IMDA certifies multivariate schemes for fintech, and India's CERT-In pilots hash-based PKIs for Aadhaar biometrics. Japan's NICT advances lattice hybrids for 6G trials, amid APAC's 60% share of global quantum patents.
Latin America's PQC uptake anticipates 16.0%–31.0% CAGR, with Brazil's ANATEL integrating quantum-safe VPNs for Petrobras pipelines. Mexico's IFT trials code-based e-voting, countering regional cyber threats.
MEA's market eyes 20.0%–36.0% expansion, with UAE's TRA piloting PQC for Dubai's smart grids. South Africa's SITA deploys multivariate for e-gov, leveraging mineral resources for quantum hardware.
Application Analysis
PQC's adaptability spans enterprise scales, with large enterprises commanding growth at 21.0%–37.0% CAGR to 2030, leveraging scale for bespoke hybrids in multicloud setups. Fortune 500s dominate, integrating PQC into zero-trust architectures for 80% of workloads. SMEs, surging at 19.0%–35.0%, embrace SaaS variants for cost-effective compliance, with 40% adoption in fintech startups shielding payment gateways.
In large enterprises, PQC fortifies core infrastructures, from lattice-secured ERPs to code-based ledgers, slashing breach costs by 45%. Hybrid models blend classical fallbacks with quantum-safe upgrades, vital for global ops spanning GDPR and CCPA.
SMEs harness PQC's modularity for agile defenses, with multivariate signatures streamlining vendor portals. Cloud-agnostic libraries democratize access, enabling 25% risk reduction sans heavy R&D. Trends like zero-knowledge proofs amplify SME innovation in DeFi, where hash-based anonymity shields micro-transactions.
Company Landscape
IBM pioneers PQC with Quantum Safe Explorer, a toolkit dissecting crypto inventories for seamless migrations, dominating 25% market share via Watson-integrated hybrids. IBM's lattice expertise powers 5,000+ deployments, emphasizing crypto-agility for Fortune 1000s.
PQShield excels in hardware-anchored PQC, with PQPlatform securing chips against side-channels; its Oxford roots yield 15% APAC traction in IoT.
ISARA Corporation's Catalyst suite blends quantum-safe certs with PKI, holding 12% enterprise share via automotive pilots.
Veridify Security's VerifAI fortifies ML models with code-based wrappers, carving 8% in edge computing.
QuSecure's QuProtect orchestrates PQC across clouds, with 10% growth in federal contracts.
QuintessenceLabs' Trusted Security Infrastructure delivers QRNG-secured keys, bolstering 7% in ANZ telecoms.
Rambus' root-of-trust modules embed hash signatures, commanding 9% in semiconductors.
NXP Semiconductors' A71CH integrates multivariate for automotive, with 11% EU dominance.
Thales Group's CipherTrust vaults PQC for data-at-rest, securing 13% in finance.
Entrust Corporation's eID fuses lattice with biometrics, growing 14% in identity management.
Industry Value Chain Analysis
PQC's value chain commences with algorithmic R&D, where academics and vendors like IBM forge resilient primitives. Hardware enablers—quantum RNGs from QuintessenceLabs—feed secure key generation, piped to middleware like PQShield's APIs for protocol wrapping. Core integration embeds PQC into stacks via ISARA's certs, culminating in enterprise deployment by Thales' vaults. End-users reap value through QuSecure's orchestration, with feedback loops refining via Entrust's audits. This chain balances innovation with interoperability, mitigating quantum risks across ecosystems.
Opportunities and Challenges
PQC heralds opportunities in quantum-secure ecosystems, with hybrid protocols slashing migration costs by 40%. Regulatory tailwinds like NIST FIPS propel enterprise uptake, while SMEs leverage SaaS for agile defenses. Asia's 5G boom amplifies PQC in IoT, fostering $50B markets by 2030.
Challenges abound in key bloat—lattice schemes inflating sizes 4x—straining bandwidth, demanding compression breakthroughs. Standardization silos risk fragmentation, urging ETSI-NIST convergence. Quantum side-channels loom, necessitating Veridify-like hardening, while talent scarcities hinder adoption.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Post-quantum Cryptography Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Post-quantum Cryptography Market in North America (2020-2030)
8.1 Post-quantum Cryptography Market Size
8.2 Post-quantum Cryptography Market by End Use
8.3 Competition by Players/Suppliers
8.4 Post-quantum Cryptography Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Post-quantum Cryptography Market in South America (2020-2030)
9.1 Post-quantum Cryptography Market Size
9.2 Post-quantum Cryptography Market by End Use
9.3 Competition by Players/Suppliers
9.4 Post-quantum Cryptography Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Post-quantum Cryptography Market in Asia & Pacific (2020-2030)
10.1 Post-quantum Cryptography Market Size
10.2 Post-quantum Cryptography Market by End Use
10.3 Competition by Players/Suppliers
10.4 Post-quantum Cryptography Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Post-quantum Cryptography Market in Europe (2020-2030)
11.1 Post-quantum Cryptography Market Size
11.2 Post-quantum Cryptography Market by End Use
11.3 Competition by Players/Suppliers
11.4 Post-quantum Cryptography Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Post-quantum Cryptography Market in MEA (2020-2030)
12.1 Post-quantum Cryptography Market Size
12.2 Post-quantum Cryptography Market by End Use
12.3 Competition by Players/Suppliers
12.4 Post-quantum Cryptography Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Post-quantum Cryptography Market (2020-2025)
13.1 Post-quantum Cryptography Market Size
13.2 Post-quantum Cryptography Market by End Use
13.3 Competition by Players/Suppliers
13.4 Post-quantum Cryptography Market Size by Type
Chapter 14 Global Post-quantum Cryptography Market Forecast (2025-2030)
14.1 Post-quantum Cryptography Market Size Forecast
14.2 Post-quantum Cryptography Application Forecast
14.3 Competition by Players/Suppliers
14.4 Post-quantum Cryptography Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 IBM
15.1.1 Company Profile
15.1.2 Main Business and Post-quantum Cryptography Information
15.1.3 SWOT Analysis of IBM
15.1.4 IBM Post-quantum Cryptography Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 PQShield
15.2.1 Company Profile
15.2.2 Main Business and Post-quantum Cryptography Information
15.2.3 SWOT Analysis of PQShield
15.2.4 PQShield Post-quantum Cryptography Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 ISARA Corporation
15.3.1 Company Profile
15.3.2 Main Business and Post-quantum Cryptography Information
15.3.3 SWOT Analysis of ISARA Corporation
15.3.4 ISARA Corporation Post-quantum Cryptography Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 Veridify Security
15.4.1 Company Profile
15.4.2 Main Business and Post-quantum Cryptography Information
15.4.3 SWOT Analysis of Veridify Security
15.4.4 Veridify Security Post-quantum Cryptography Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 QuSecure
15.5.1 Company Profile
15.5.2 Main Business and Post-quantum Cryptography Information
15.5.3 SWOT Analysis of QuSecure
15.5.4 QuSecure Post-quantum Cryptography Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 QuintessenceLabs
15.6.1 Company Profile
15.6.2 Main Business and Post-quantum Cryptography Information
15.6.3 SWOT Analysis of QuintessenceLabs
15.6.4 QuintessenceLabs Post-quantum Cryptography Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of Post-quantum Cryptography Report
Table Data Sources of Post-quantum Cryptography Report
Table Major Assumptions of Post-quantum Cryptography Report
Table Post-quantum Cryptography Classification
Table Post-quantum Cryptography Applications
Table Drivers of Post-quantum Cryptography Market
Table Restraints of Post-quantum Cryptography Market
Table Opportunities of Post-quantum Cryptography Market
Table Threats of Post-quantum Cryptography Market
Table Raw Materials Suppliers
Table Different Production Methods of Post-quantum Cryptography
Table Cost Structure Analysis of Post-quantum Cryptography
Table Key End Users
Table Latest News of Post-quantum Cryptography Market
Table Merger and Acquisition
Table Planned/Future Project of Post-quantum Cryptography Market
Table Policy of Post-quantum Cryptography Market
Table 2020-2030 North America Post-quantum Cryptography Market Size
Table 2020-2030 North America Post-quantum Cryptography Market Size by Application
Table 2020-2025 North America Post-quantum Cryptography Key Players Revenue
Table 2020-2025 North America Post-quantum Cryptography Key Players Market Share
Table 2020-2030 North America Post-quantum Cryptography Market Size by Type
Table 2020-2030 United States Post-quantum Cryptography Market Size
Table 2020-2030 Canada Post-quantum Cryptography Market Size
Table 2020-2030 Mexico Post-quantum Cryptography Market Size
Table 2020-2030 South America Post-quantum Cryptography Market Size
Table 2020-2030 South America Post-quantum Cryptography Market Size by Application
Table 2020-2025 South America Post-quantum Cryptography Key Players Revenue
Table 2020-2025 South America Post-quantum Cryptography Key Players Market Share
Table 2020-2030 South America Post-quantum Cryptography Market Size by Type
Table 2020-2030 Brazil Post-quantum Cryptography Market Size
Table 2020-2030 Argentina Post-quantum Cryptography Market Size
Table 2020-2030 Chile Post-quantum Cryptography Market Size
Table 2020-2030 Peru Post-quantum Cryptography Market Size
Table 2020-2030 Asia & Pacific Post-quantum Cryptography Market Size
Table 2020-2030 Asia & Pacific Post-quantum Cryptography Market Size by Application
Table 2020-2025 Asia & Pacific Post-quantum Cryptography Key Players Revenue
Table 2020-2025 Asia & Pacific Post-quantum Cryptography Key Players Market Share
Table 2020-2030 Asia & Pacific Post-quantum Cryptography Market Size by Type
Table 2020-2030 China Post-quantum Cryptography Market Size
Table 2020-2030 India Post-quantum Cryptography Market Size
Table 2020-2030 Japan Post-quantum Cryptography Market Size
Table 2020-2030 South Korea Post-quantum Cryptography Market Size
Table 2020-2030 Southeast Asia Post-quantum Cryptography Market Size
Table 2020-2030 Australia Post-quantum Cryptography Market Size
Table 2020-2030 Europe Post-quantum Cryptography Market Size
Table 2020-2030 Europe Post-quantum Cryptography Market Size by Application
Table 2020-2025 Europe Post-quantum Cryptography Key Players Revenue
Table 2020-2025 Europe Post-quantum Cryptography Key Players Market Share
Table 2020-2030 Europe Post-quantum Cryptography Market Size by Type
Table 2020-2030 Germany Post-quantum Cryptography Market Size
Table 2020-2030 France Post-quantum Cryptography Market Size
Table 2020-2030 United Kingdom Post-quantum Cryptography Market Size
Table 2020-2030 Italy Post-quantum Cryptography Market Size
Table 2020-2030 Spain Post-quantum Cryptography Market Size
Table 2020-2030 Belgium Post-quantum Cryptography Market Size
Table 2020-2030 Netherlands Post-quantum Cryptography Market Size
Table 2020-2030 Austria Post-quantum Cryptography Market Size
Table 2020-2030 Poland Post-quantum Cryptography Market Size
Table 2020-2030 Russia Post-quantum Cryptography Market Size
Table 2020-2030 MEA Post-quantum Cryptography Market Size
Table 2020-2030 MEA Post-quantum Cryptography Market Size by Application
Table 2020-2025 MEA Post-quantum Cryptography Key Players Revenue
Table 2020-2025 MEA Post-quantum Cryptography Key Players Market Share
Table 2020-2030 MEA Post-quantum Cryptography Market Size by Type
Table 2020-2030 Egypt Post-quantum Cryptography Market Size
Table 2020-2030 Israel Post-quantum Cryptography Market Size
Table 2020-2030 South Africa Post-quantum Cryptography Market Size
Table 2020-2030 Gulf Cooperation Council Countries Post-quantum Cryptography Market Size
Table 2020-2030 Turkey Post-quantum Cryptography Market Size
Table 2020-2025 Global Post-quantum Cryptography Market Size by Region
Table 2020-2025 Global Post-quantum Cryptography Market Size Share by Region
Table 2020-2025 Global Post-quantum Cryptography Market Size by Application
Table 2020-2025 Global Post-quantum Cryptography Market Share by Application
Table 2020-2025 Global Post-quantum Cryptography Key Vendors Revenue
Table 2020-2025 Global Post-quantum Cryptography Key Vendors Market Share
Table 2020-2025 Global Post-quantum Cryptography Market Size by Type
Table 2020-2025 Global Post-quantum Cryptography Market Share by Type
Table 2025-2030 Global Post-quantum Cryptography Market Size by Region
Table 2025-2030 Global Post-quantum Cryptography Market Size Share by Region
Table 2025-2030 Global Post-quantum Cryptography Market Size by Application
Table 2025-2030 Global Post-quantum Cryptography Market Share by Application
Table 2025-2030 Global Post-quantum Cryptography Key Vendors Revenue
Table 2025-2030 Global Post-quantum Cryptography Key Vendors Market Share
Table 2025-2030 Global Post-quantum Cryptography Market Size by Type
Table 2025-2030 Post-quantum Cryptography Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Post-quantum Cryptography Picture
Figure 2020-2030 North America Post-quantum Cryptography Market Size and CAGR
Figure 2020-2030 South America Post-quantum Cryptography Market Size and CAGR
Figure 2020-2030 Asia & Pacific Post-quantum Cryptography Market Size and CAGR
Figure 2020-2030 Europe Post-quantum Cryptography Market Size and CAGR
Figure 2020-2030 MEA Post-quantum Cryptography Market Size and CAGR
Figure 2020-2025 Global Post-quantum Cryptography Market Size and Growth Rate
Figure 2025-2030 Global Post-quantum Cryptography Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
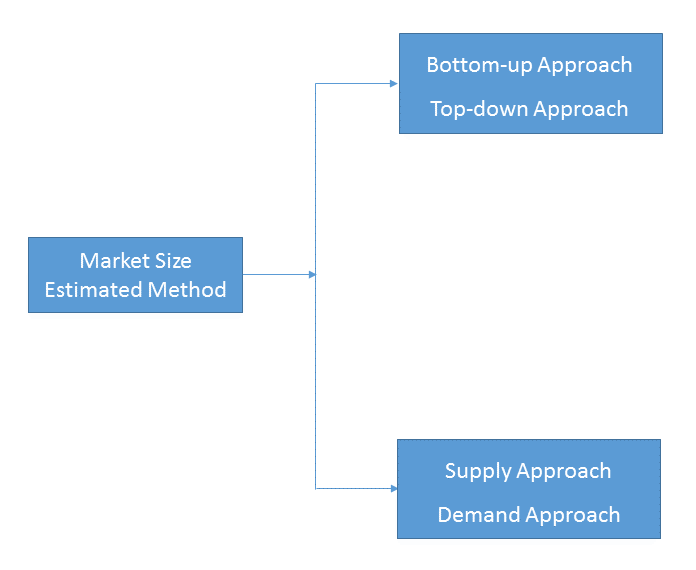
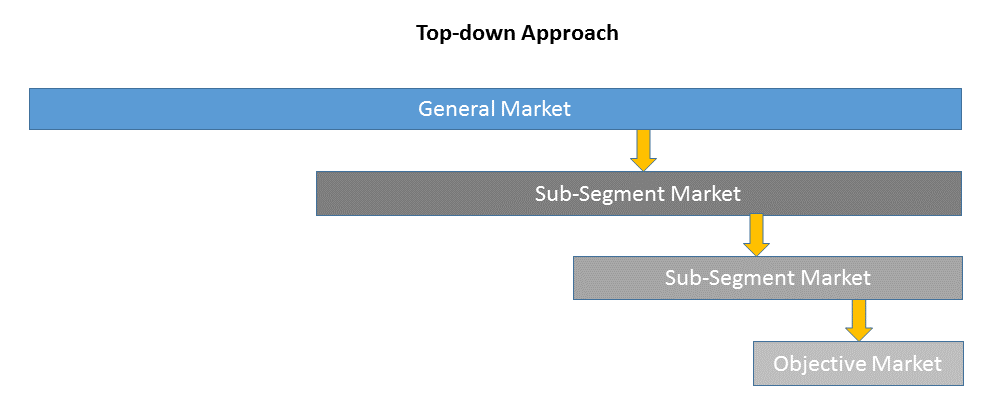
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
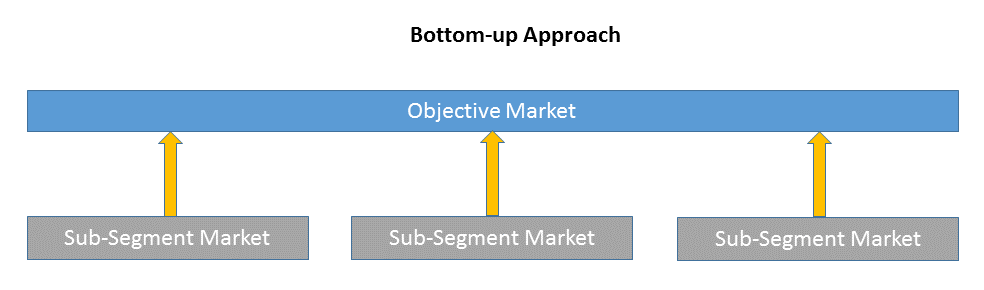
Bottom-up approach size the objective market by collecting the sub-segment information.
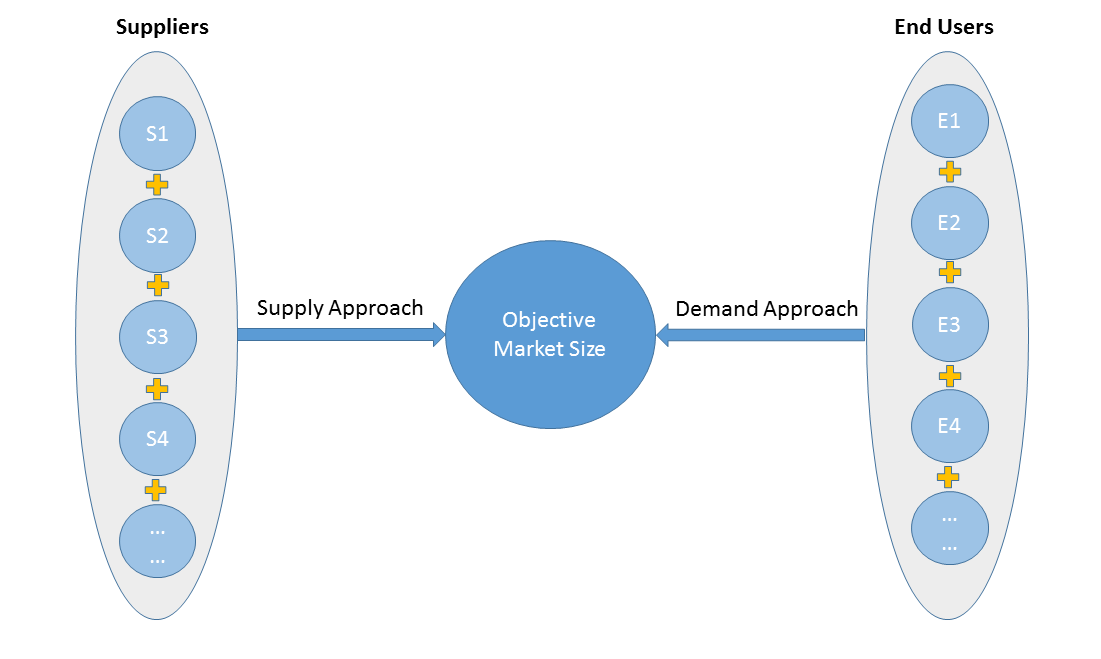
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
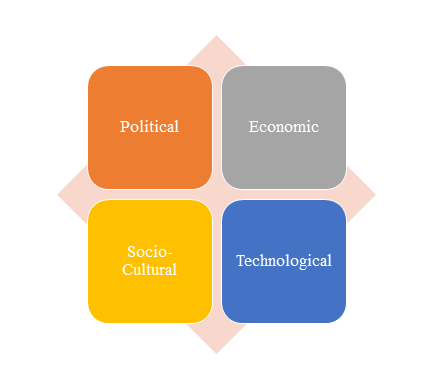
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
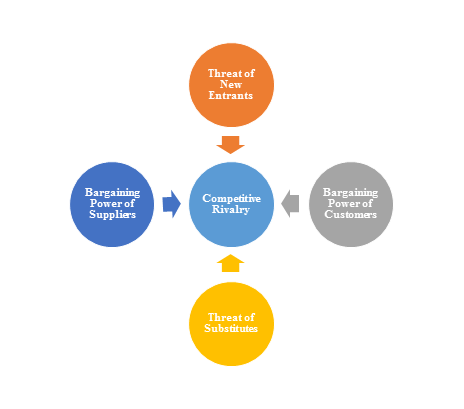
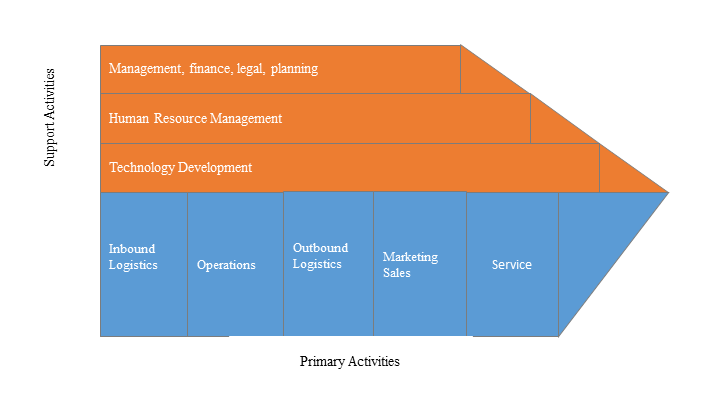
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
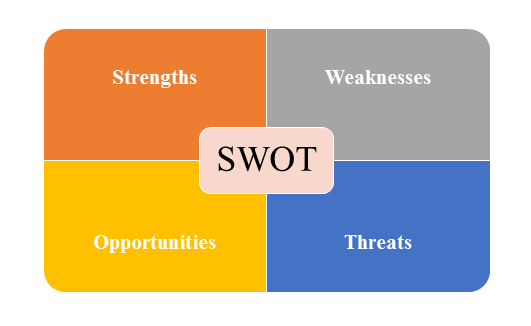
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |