Passive Authentication Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
The Passive Authentication market is a sophisticated layer of the cybersecurity and identity verification ecosystem, leveraging behavioral biometrics, device fingerprinting, and environmental signals to continuously validate user identity without disrupting the user experience. Unlike active methods requiring explicit actions like passwords or biometrics, passive authentication operates silently in the background, analyzing keystroke dynamics, mouse movements, gait patterns, network fingerprints, and contextual factors to establish a unique behavioral baseline and detect anomalies in real time. These solutions integrate with existing authentication frameworks, enhancing multi-factor authentication (MFA) with frictionless, risk-adaptive layers that adapt to evolving threats without user fatigue. Characterized by their machine learning models for continuous learning, zero-trust principles, and compliance with standards such as PSD2, eIDAS, and FIDO2, passive authentication platforms prevent account takeovers, insider threats, and synthetic identity fraud by scoring session risk and triggering silent interventions. Their strategic value lies in reducing false positives by up to 90%, enabling seamless onboarding, and transforming security from a barrier into an invisible guardian. The market thrives on the surge in digital transactions, the rise of contactless banking, and the imperative for adaptive, user-centric defenses amid sophisticated cyber campaigns. The global Passive Authentication market is estimated to reach a valuation of approximately USD 1.0–2.0 billion in 2025, with compound annual growth rates projected in the range of 10.0%–20.0% through 2030. Growth is propelled by the proliferation of mobile and IoT endpoints, regulatory mandates for stronger customer authentication, and the integration of behavioral signals into zero-trust architectures.
Application Analysis and Market Segmentation
BFSI Applications
In banking, financial services, and insurance (BFSI), passive authentication secures online banking, mobile apps, and payment gateways by monitoring user behavior during transactions, flagging deviations like unusual swipe patterns or session anomalies. These solutions integrate with core banking systems and fraud management platforms to enable risk-based authentication. This segment is expected to grow at 11%–21% annually, driven by PSD2 Strong Customer Authentication (SCA) requirements and the rise of embedded finance. Trends include AI models trained on global transaction datasets for cross-border fraud detection, seamless integration with biometric overlays for layered defense, and real-time behavioral scoring that adjusts dynamically to user habits over time. As open banking expands, platforms are evolving to support federated behavioral profiles across partner ecosystems, ensuring continuity in user verification without re-authentication.
Government Applications
Government agencies deploy passive authentication for secure citizen portals, e-governance services, and identity management in public sector apps, analyzing device and behavioral signals to prevent unauthorized access to sensitive data. Compliance with standards like NIST 800-63 and eIDAS is paramount. Projected to grow at 10%–18% annually, growth is fueled by digital government initiatives and rising cyber threats to public infrastructure. Key developments encompass continuous monitoring for insider threats in administrative systems, integration with national ID frameworks for seamless verification, and anomaly detection tailored to demographic behavioral norms. Trends focus on privacy-preserving federated learning across agencies, enabling shared threat intelligence without data centralization, and the adoption of passive signals for voter registration and benefit claims to enhance accessibility while mitigating fraud.
IT & Telecommunications Applications
In IT and telecom, passive authentication protects network access, VPN sessions, and customer support portals by tracking user interactions and device telemetry to detect lateral movement or unauthorized logins. This segment anticipates 9%–17% growth annually, supported by the expansion of 5G and edge computing security needs. Innovations include behavioral baselines adapted to network latency variations, integration with SIEM for automated incident response, and trends toward zero-touch onboarding for IoT devices using passive environmental fingerprints. As telecoms embrace API economies, platforms are incorporating machine learning to distinguish legitimate API calls from synthetic traffic, ensuring robust defense without impacting user throughput.
Retail and Consumer Goods Applications
Retail and consumer goods use passive authentication to secure e-commerce checkouts, loyalty programs, and in-app purchases by analyzing shopping cart behaviors and device interactions. Growth at 11%–20% annually reflects the boom in mobile commerce and personalized retail. Trends encompass contextual risk scoring based on purchase history and location, seamless integration with payment processors for frictionless 3D Secure exemptions, and AI models that learn from seasonal shopping patterns. As omnichannel experiences proliferate, solutions are evolving to blend passive signals with computer vision for in-store fraud detection, creating unified protection across physical and digital touchpoints.
Healthcare Applications
Healthcare applications employ passive authentication for patient portals, telehealth sessions, and EHR access, verifying users through typing rhythms and device habits to safeguard PHI under HIPAA. This segment is projected to grow at 10%–18% annually, driven by digital health acceleration and telemedicine mandates. Developments include continuous re-authentication during virtual consultations, integration with wearable data for behavioral continuity, and trends toward federated models across health networks. As value-based care emphasizes data security, platforms are incorporating explainable AI for audit trails, ensuring defensibility in regulatory reviews.
Media and Entertainment Applications
In media and entertainment, passive authentication secures streaming subscriptions, content DRM, and fan engagement apps by monitoring viewing patterns and device fingerprints. Expected to grow at 9%–16% annually, supported by OTT personalization and live event ticketing. Trends include anomaly detection for account sharing, integration with blockchain for NFT ownership verification, and AI-adapted baselines for multi-device households. As interactive media rises, solutions are enabling passive consent for targeted ads without interrupting immersion.
Others Applications
Encompassing education, energy, and transportation, this diverse segment grows at 8%–15% with secure learning platforms and fleet management authentication.
Cloud Deployment Mode
Cloud-based passive authentication offers scalability, real-time updates, and seamless integration with SaaS ecosystems. This mode is anticipated to grow at 11%–21% annually, dominant due to zero-trust and microservices architectures. Trends include serverless behavioral scoring and multi-cloud federation.
On-premises Deployment Mode
On-premises deployment provides air-gapped security for classified environments. Growth at 7%–13% annually, sustained by defense and legacy systems. Trends encompass containerized microservices on private clouds.
Regional Market Distribution and Geographic Trends
Asia-Pacific: 11%–21% growth annually, led by India's UPI-driven digital payments and China's social credit biometrics. Japan focuses on enterprise-grade behavioral analytics.
North America: 10%–18% growth, with U.S. fintech and Canadian banking leading. Trends emphasize PSD2-inspired SCA frameworks.
Europe: 9%–16% growth, driven by eIDAS 2.0 in Germany and UK open banking. The region prioritizes GDPR-compliant anonymization.
Latin America: 10%–18% growth, with Brazil's Pix ecosystem and Mexico's nearshore finance.
Middle East & Africa: 9%–17% growth, led by UAE's smart city payments and South Africa's mobile money. Arabic behavioral models emerge.
Key Market Players and Competitive Landscape
BioCatch – Pioneer in behavioral biometrics with $100M+ ARR, powering global banks with session-level fraud prevention.
BehavioSec (LexisNexis) – Acquired for $150M, integrates typing biometrics into identity suite.
NuData (Mastercard) – Device intelligence leader, preventing $1B+ in fraud annually.
ThreatMetrix (LexisNexis) – Digital identity with behavioral signals, serving e-commerce giants.
SecureAuth – Adaptive MFA with biometrics, strong in healthcare.
TypingDNA – Keystroke dynamics specialist with 99.8% accuracy.
UnifyID (Prove) – Behavioral AI for continuous auth.
Zighra – Canadian firm with gesture recognition.
Aware – Biometric SDK with passive elements.
Industry Value Chain Analysis
The Passive Authentication value chain is seamless-centric, spanning baseline to response, with value concentrated in frictionless security.
Raw Materials and Upstream Supply
Device telemetry, network signals, AI training data. Cloud providers supply scalable inference.
Production and Processing
Behavioral modeling, anomaly scoring, continuous adaptation. Quality assurance ensures <1% false positives.
Distribution and Logistics
API embeddings, SDKs, and SIEM integrations. Global logistics prioritize low-latency edge processing.
Downstream Processing and Application Integration
BFSI: Core banking silent re-auth.
Healthcare: EHR session continuity.
Integration enables risk-adaptive MFA.
End-User Industries
Finance and retail extract peak ROI via 80% fraud reduction.
Market Opportunities and Challenges
Opportunities
The PSD2 and eIDAS expansions create regulatory tailwinds for seamless auth. AI advancements enable behavioral fusion with biometrics. SME mobile banking surge opens volume markets. IoT endpoint proliferation demands passive device trust. Partnerships with Mastercard and LexisNexis accelerate ecosystem adoption.
Challenges
Behavioral drift from user habit changes demands adaptive retraining. Privacy regulations require anonymized signal processing. Legacy systems resist API integration. Over-reliance on patterns risks sophisticated mimicry. Ensuring cultural neutrality in global models is essential.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Passive Authentication Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Passive Authentication Market in North America (2020-2030)
8.1 Passive Authentication Market Size
8.2 Passive Authentication Market by End Use
8.3 Competition by Players/Suppliers
8.4 Passive Authentication Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Passive Authentication Market in South America (2020-2030)
9.1 Passive Authentication Market Size
9.2 Passive Authentication Market by End Use
9.3 Competition by Players/Suppliers
9.4 Passive Authentication Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Passive Authentication Market in Asia & Pacific (2020-2030)
10.1 Passive Authentication Market Size
10.2 Passive Authentication Market by End Use
10.3 Competition by Players/Suppliers
10.4 Passive Authentication Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Passive Authentication Market in Europe (2020-2030)
11.1 Passive Authentication Market Size
11.2 Passive Authentication Market by End Use
11.3 Competition by Players/Suppliers
11.4 Passive Authentication Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Passive Authentication Market in MEA (2020-2030)
12.1 Passive Authentication Market Size
12.2 Passive Authentication Market by End Use
12.3 Competition by Players/Suppliers
12.4 Passive Authentication Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Passive Authentication Market (2020-2025)
13.1 Passive Authentication Market Size
13.2 Passive Authentication Market by End Use
13.3 Competition by Players/Suppliers
13.4 Passive Authentication Market Size by Type
Chapter 14 Global Passive Authentication Market Forecast (2025-2030)
14.1 Passive Authentication Market Size Forecast
14.2 Passive Authentication Application Forecast
14.3 Competition by Players/Suppliers
14.4 Passive Authentication Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 BioCatch
15.1.1 Company Profile
15.1.2 Main Business and Passive Authentication Information
15.1.3 SWOT Analysis of BioCatch
15.1.4 BioCatch Passive Authentication Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 BehavioSec (LexisNexis)
15.2.1 Company Profile
15.2.2 Main Business and Passive Authentication Information
15.2.3 SWOT Analysis of BehavioSec (LexisNexis)
15.2.4 BehavioSec (LexisNexis) Passive Authentication Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 NuData (Mastercard)
15.3.1 Company Profile
15.3.2 Main Business and Passive Authentication Information
15.3.3 SWOT Analysis of NuData (Mastercard)
15.3.4 NuData (Mastercard) Passive Authentication Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 ThreatMetrix (LexisNexis)
15.4.1 Company Profile
15.4.2 Main Business and Passive Authentication Information
15.4.3 SWOT Analysis of ThreatMetrix (LexisNexis)
15.4.4 ThreatMetrix (LexisNexis) Passive Authentication Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 SecureAuth
15.5.1 Company Profile
15.5.2 Main Business and Passive Authentication Information
15.5.3 SWOT Analysis of SecureAuth
15.5.4 SecureAuth Passive Authentication Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 TypingDNA
15.6.1 Company Profile
15.6.2 Main Business and Passive Authentication Information
15.6.3 SWOT Analysis of TypingDNA
15.6.4 TypingDNA Passive Authentication Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of Passive Authentication Report
Table Data Sources of Passive Authentication Report
Table Major Assumptions of Passive Authentication Report
Table Passive Authentication Classification
Table Passive Authentication Applications
Table Drivers of Passive Authentication Market
Table Restraints of Passive Authentication Market
Table Opportunities of Passive Authentication Market
Table Threats of Passive Authentication Market
Table Raw Materials Suppliers
Table Different Production Methods of Passive Authentication
Table Cost Structure Analysis of Passive Authentication
Table Key End Users
Table Latest News of Passive Authentication Market
Table Merger and Acquisition
Table Planned/Future Project of Passive Authentication Market
Table Policy of Passive Authentication Market
Table 2020-2030 North America Passive Authentication Market Size
Table 2020-2030 North America Passive Authentication Market Size by Application
Table 2020-2025 North America Passive Authentication Key Players Revenue
Table 2020-2025 North America Passive Authentication Key Players Market Share
Table 2020-2030 North America Passive Authentication Market Size by Type
Table 2020-2030 United States Passive Authentication Market Size
Table 2020-2030 Canada Passive Authentication Market Size
Table 2020-2030 Mexico Passive Authentication Market Size
Table 2020-2030 South America Passive Authentication Market Size
Table 2020-2030 South America Passive Authentication Market Size by Application
Table 2020-2025 South America Passive Authentication Key Players Revenue
Table 2020-2025 South America Passive Authentication Key Players Market Share
Table 2020-2030 South America Passive Authentication Market Size by Type
Table 2020-2030 Brazil Passive Authentication Market Size
Table 2020-2030 Argentina Passive Authentication Market Size
Table 2020-2030 Chile Passive Authentication Market Size
Table 2020-2030 Peru Passive Authentication Market Size
Table 2020-2030 Asia & Pacific Passive Authentication Market Size
Table 2020-2030 Asia & Pacific Passive Authentication Market Size by Application
Table 2020-2025 Asia & Pacific Passive Authentication Key Players Revenue
Table 2020-2025 Asia & Pacific Passive Authentication Key Players Market Share
Table 2020-2030 Asia & Pacific Passive Authentication Market Size by Type
Table 2020-2030 China Passive Authentication Market Size
Table 2020-2030 India Passive Authentication Market Size
Table 2020-2030 Japan Passive Authentication Market Size
Table 2020-2030 South Korea Passive Authentication Market Size
Table 2020-2030 Southeast Asia Passive Authentication Market Size
Table 2020-2030 Australia Passive Authentication Market Size
Table 2020-2030 Europe Passive Authentication Market Size
Table 2020-2030 Europe Passive Authentication Market Size by Application
Table 2020-2025 Europe Passive Authentication Key Players Revenue
Table 2020-2025 Europe Passive Authentication Key Players Market Share
Table 2020-2030 Europe Passive Authentication Market Size by Type
Table 2020-2030 Germany Passive Authentication Market Size
Table 2020-2030 France Passive Authentication Market Size
Table 2020-2030 United Kingdom Passive Authentication Market Size
Table 2020-2030 Italy Passive Authentication Market Size
Table 2020-2030 Spain Passive Authentication Market Size
Table 2020-2030 Belgium Passive Authentication Market Size
Table 2020-2030 Netherlands Passive Authentication Market Size
Table 2020-2030 Austria Passive Authentication Market Size
Table 2020-2030 Poland Passive Authentication Market Size
Table 2020-2030 Russia Passive Authentication Market Size
Table 2020-2030 MEA Passive Authentication Market Size
Table 2020-2030 MEA Passive Authentication Market Size by Application
Table 2020-2025 MEA Passive Authentication Key Players Revenue
Table 2020-2025 MEA Passive Authentication Key Players Market Share
Table 2020-2030 MEA Passive Authentication Market Size by Type
Table 2020-2030 Egypt Passive Authentication Market Size
Table 2020-2030 Israel Passive Authentication Market Size
Table 2020-2030 South Africa Passive Authentication Market Size
Table 2020-2030 Gulf Cooperation Council Countries Passive Authentication Market Size
Table 2020-2030 Turkey Passive Authentication Market Size
Table 2020-2025 Global Passive Authentication Market Size by Region
Table 2020-2025 Global Passive Authentication Market Size Share by Region
Table 2020-2025 Global Passive Authentication Market Size by Application
Table 2020-2025 Global Passive Authentication Market Share by Application
Table 2020-2025 Global Passive Authentication Key Vendors Revenue
Table 2020-2025 Global Passive Authentication Key Vendors Market Share
Table 2020-2025 Global Passive Authentication Market Size by Type
Table 2020-2025 Global Passive Authentication Market Share by Type
Table 2025-2030 Global Passive Authentication Market Size by Region
Table 2025-2030 Global Passive Authentication Market Size Share by Region
Table 2025-2030 Global Passive Authentication Market Size by Application
Table 2025-2030 Global Passive Authentication Market Share by Application
Table 2025-2030 Global Passive Authentication Key Vendors Revenue
Table 2025-2030 Global Passive Authentication Key Vendors Market Share
Table 2025-2030 Global Passive Authentication Market Size by Type
Table 2025-2030 Passive Authentication Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Passive Authentication Picture
Figure 2020-2030 North America Passive Authentication Market Size and CAGR
Figure 2020-2030 South America Passive Authentication Market Size and CAGR
Figure 2020-2030 Asia & Pacific Passive Authentication Market Size and CAGR
Figure 2020-2030 Europe Passive Authentication Market Size and CAGR
Figure 2020-2030 MEA Passive Authentication Market Size and CAGR
Figure 2020-2025 Global Passive Authentication Market Size and Growth Rate
Figure 2025-2030 Global Passive Authentication Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
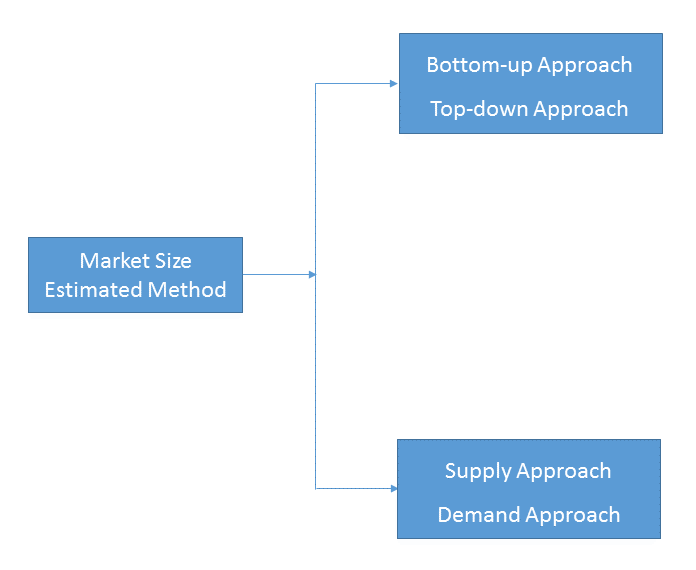
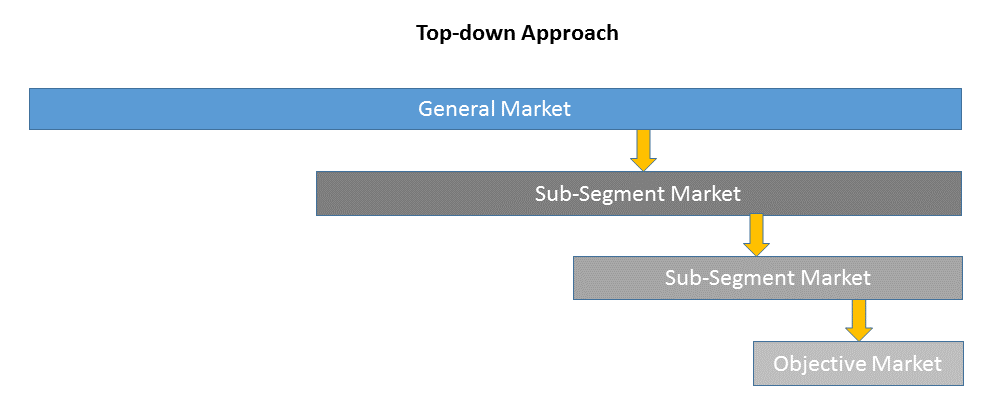
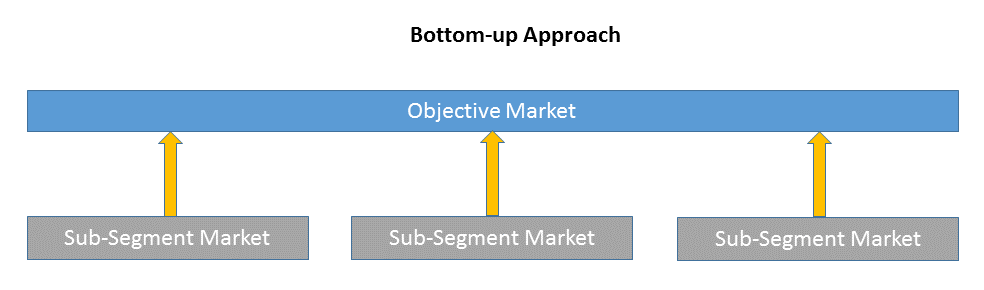
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
Bottom-up approach size the objective market by collecting the sub-segment information.
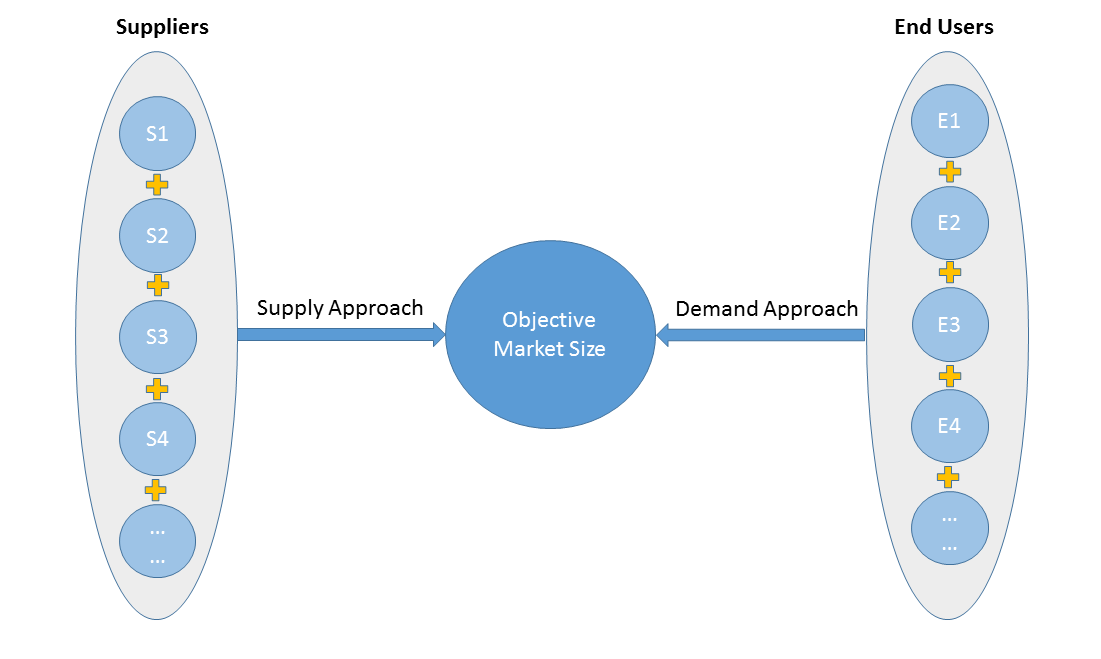
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
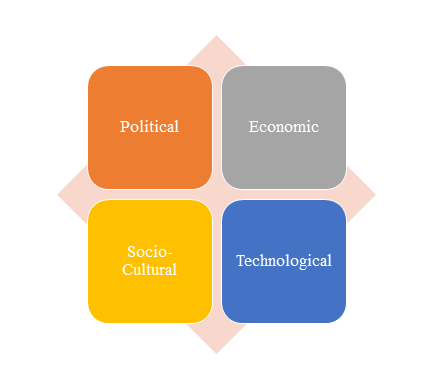
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
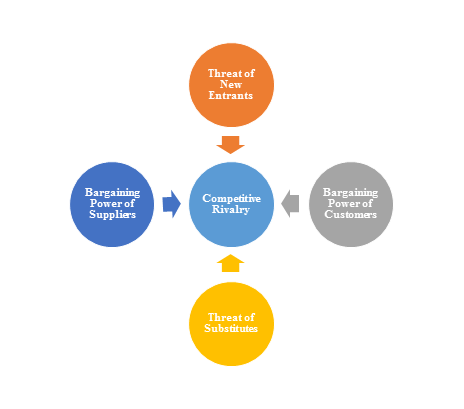
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
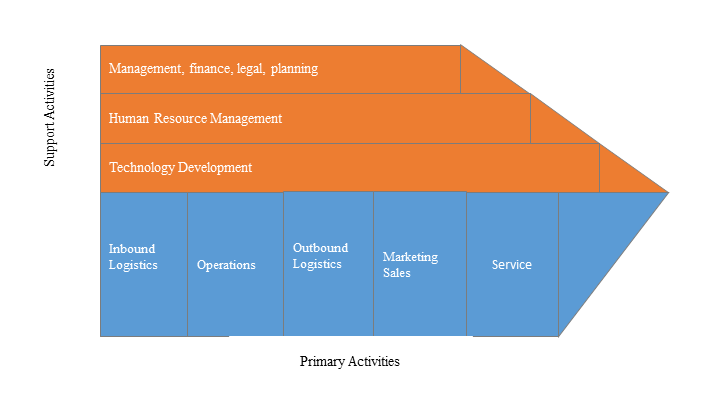
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
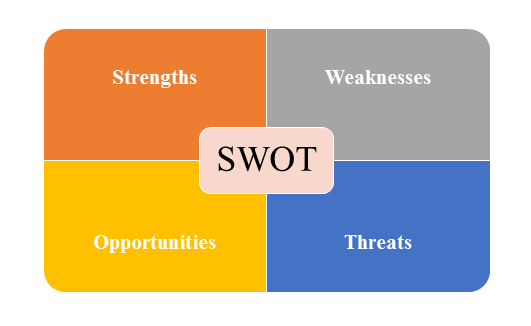
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |