Security & Vulnerability Management (SVM) Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
Security & Vulnerability Management (SVM) encompasses integrated platforms and services that continuously discover, assess, prioritize, and remediate vulnerabilities across IT infrastructure, applications, cloud environments, and IoT ecosystems. These solutions combine automated asset discovery, risk-based vulnerability scoring, patch management, and compliance reporting to reduce exposure windows and prevent exploitation. The industry is characterized by its reliance on AI-driven threat intelligence, machine learning for false positive reduction, and real-time correlation of vulnerability data with active exploits, achieving up to 90% accuracy in prioritization. SVM platforms integrate with DevSecOps pipelines, SIEM systems, and cloud-native security tools to enable proactive risk management at scale. Unlike traditional scanning tools, modern SVM solutions provide contextual risk scoring, automated remediation workflows, and executive-level risk dashboards, reducing mean time to remediate (MTTR) by 60%. The sector is driven by the exponential growth of cyber threats, with over 2,200 confirmed data breaches annually, and the expansion of attack surfaces due to cloud migration, remote work, and IoT proliferation. The global Security & Vulnerability Management market is estimated to reach between USD 10.0 billion and USD 20.0 billion by 2025. From 2025 to 2030, the market is projected to grow at a compound annual growth rate (CAGR) of approximately 4.0% to 14.0%, fueled by regulatory mandates, zero-trust adoption, and the integration of AI in threat detection. This growth highlights SVM’s critical role in enabling resilient, compliant, and adaptive cybersecurity defenses in an increasingly complex threat landscape.
Industry Characteristics
Security & Vulnerability Management solutions are defined by their ability to maintain a dynamic inventory of assets—spanning on-premises servers, cloud workloads, containers, and IoT devices—and correlate vulnerabilities with exploitability, business criticality, and threat intelligence. These platforms leverage AI to reduce noise by 85%, prioritizing remediation based on CVSS scores, EPSS (Exploit Prediction Scoring System), and active exploitation data. Key features include agentless and agent-based scanning, automated patch deployment, and integration with IT service management (ITSM) tools for closed-loop remediation. The industry supports compliance with frameworks like NIST, ISO 27001, and PCI DSS through continuous monitoring and audit-ready reporting. SVM platforms are cloud-native by design, with microservices architectures enabling scalability across hybrid environments. Unlike point solutions, SVM delivers end-to-end risk lifecycle management—from discovery to verification of fix—with role-based workflows for SecOps, DevOps, and executive stakeholders. The sector is innovation-driven, with advancements in behavioral analytics, automated penetration testing, and integration with SOAR (Security Orchestration, Automation, and Response) platforms. Sustainability trends focus on energy-efficient scanning and cloud-optimized processing, reducing carbon footprints in large-scale deployments. The market fosters strategic alliances between SVM vendors, cloud providers, and MSSPs (Managed Security Service Providers), ensuring comprehensive coverage and rapid response. The rise of zero-trust architectures, API security, and supply chain risk management further accelerates demand for advanced SVM capabilities.
Regional Market Trends
SVM adoption aligns with cybersecurity maturity, regulatory stringency, and digital transformation, with regional growth shaped by enterprise density and threat exposure.
North America: This region is a major market, with growth projected at 4.0%–13.0% CAGR through 2030. The United States leads, driven by financial services in New York and tech firms in Silicon Valley adopting SVM for cloud and application security. Canada’s public sector in Ottawa leverages SVM for critical infrastructure protection. Federal regulations like CMMC and SEC cybersecurity disclosure rules, combined with high ransomware incidence, fuel demand. Trends include AI-driven risk prioritization and integration with XDR platforms.
Europe: Europe’s market is expected to grow at 4.5%–14.0% CAGR. The UK leads with SVM adoption in BFSI and government in London, while Germany’s manufacturing sector in Munich uses SVM for OT/IoT security. The Netherlands emerges as a hub for cloud-native SVM in Amsterdam. GDPR, NIS2 Directive, and DORA drive mandatory vulnerability management programs, though fragmented national regulations complicate compliance. Trends include supply chain risk assessment and automated compliance reporting.
Asia-Pacific (APAC): APAC is the fastest-growing region, with a 5.0%–15.0% CAGR. China dominates with SVM for state-owned enterprises and tech giants in Beijing and Shanghai, supported by national cybersecurity laws. India’s IT and fintech sectors in Bengaluru adopt SVM for cloud workloads, while Japan’s critical infrastructure in Tokyo prioritizes SVM for resilience. South Korea’s 5G leadership drives IoT-focused SVM. Government mandates, like China’s MLPS 2.0 and India’s DPDP Act, accelerate adoption, though data sovereignty requirements challenge global vendors. Trends include DevSecOps integration and API security.
Latin America: This market grows at 3.5%–12.0% CAGR. Brazil’s financial and retail sectors in São Paulo adopt SVM for PCI compliance, while Mexico’s manufacturing in Monterrey uses it for supply chain security. Economic volatility and skills gaps limit enterprise investment, but managed SVM services gain traction. Trends include ransomware defense and cloud migration security.
Middle East and Africa (MEA): MEA sees 4.0%–13.0% CAGR. The UAE and Saudi Arabia lead through Vision 2030, with SVM for critical infrastructure in Dubai and Riyadh. Israel’s cybersecurity ecosystem in Tel Aviv drives innovation in SVM for defense and finance. Limited local expertise slows adoption, but regulatory frameworks like UAE’s NESA and Saudi’s NCA mandate vulnerability management. Trends include OT security for energy and smart cities.
Application Analysis
SVM serves organizations of varying sizes, each with distinct risk profiles and operational needs.
Large Enterprises: The dominant segment, with 4.5%–14.5% CAGR, includes global corporations in BFSI, healthcare, and manufacturing. SVM enables centralized risk visibility across distributed assets, reducing critical vulnerabilities by 70%. Adoption in the U.S., Germany, and Japan focuses on zero-trust and supply chain security, with trends toward automated remediation and executive risk dashboards. Integration complexity with legacy systems remains a challenge.
SMEs: Growing at 3.5%–12.5% CAGR, SMEs adopt cloud-based SVM for cost-effective, managed security. Platforms offer pre-configured policies and MSSP integration, with strong uptake in India, Brazil, and the UK. Trends include SaaS-delivered SVM with built-in compliance templates, though limited security expertise hinders effective utilization.
Component Analysis
SVM is delivered through software platforms and professional services, addressing different deployment and management preferences.
Software: The larger segment, with 4.5%–14.0% CAGR, includes cloud-native and on-premises SVM platforms. AI-powered scanners and risk engines dominate, with adoption in North America and APAC. Trends include container and API scanning, though false positive management requires ongoing refinement.
Services: Growing at 3.5%–13.0% CAGR, services encompass managed vulnerability management, penetration testing, and compliance consulting. MSSPs deliver SVM-as-a-service, with strong demand in Europe and MEA. Trends include 24/7 threat hunting and remediation orchestration, though talent shortages impact service quality.
Company Landscape
The SVM market features established cybersecurity leaders and specialized vulnerability management providers.
Qualys: U.S.-based leader, Qualys offers cloud-native SVM with asset discovery and risk prioritization. Its global sensor network serves Fortune 500 clients, dominant in North America and Europe.
Tenable: U.S. provider of comprehensive SVM, Tenable.io and Tenable.ep integrate predictive prioritization. Strong in government and critical infrastructure, with growth in APAC.
Rapid7: U.S.-based, Rapid7’s InsightVM delivers risk-based vulnerability management with DevSecOps integration. Its adoption grows in SMEs via managed services in Latin America.
IBM: Offers X-Force Red Vulnerability Management, integrating AI and threat intelligence. Serves large enterprises in BFSI and healthcare globally.
Microsoft: Defender Vulnerability Management, part of Microsoft 365 Defender, serves cloud-first enterprises. Strong integration with Azure drives adoption in APAC.
Cisco: Cisco Vulnerability Management (formerly Kenna Security) provides risk-based prioritization. Integrated with SecureX, it serves telecom and enterprise clients.
ServiceNow: Integrates SVM into its IT service management platform, enabling closed-loop remediation. Dominant in large enterprises in North America and Europe.
BeyondTrust: Focuses on privileged access and vulnerability management, serving regulated industries in the U.S. and UK.
Greenbone: Germany-based open-source SVM provider, Greenbone serves cost-conscious enterprises and government in Europe and MEA.
ManageEngine: India-based, offers affordable SVM for SMEs, with strong adoption in APAC and Latin America.
These vendors innovate through AI, cloud integration, and partnerships with MSSPs and cloud hyperscalers.
Industry Value Chain Analysis
The SVM value chain spans threat intelligence to remediation verification, emphasizing automation and integration.
Raw Materials: Inputs include threat feeds, CVSS data, cloud APIs, and AI models, sourced from MITRE, FIRST, and cloud providers. Supply chain risks include feed latency and model bias.
Development: SVM platforms are built using Python, Go, and Kubernetes, with ML for risk scoring. Continuous scanning engines reduce detection lag by 50%, but R&D costs are high.
Distribution: SVM is delivered via SaaS, licenses, or managed services. Vendors like Qualys offer global cloud regions, though data residency laws complicate delivery.
Downstream Applications: Enterprises integrate SVM into SecOps, DevSecOps, and compliance workflows. Feedback from remediation outcomes refines algorithms, with MSSPs ensuring 24/7 coverage. Subscription and outcome-based pricing drive revenue.
The chain’s cloud-native design enables scalability, with vertical integration by firms like Tenable ensuring accuracy.
Opportunities and Challenges
The SVM market offers significant opportunities. The rise of cloud workloads, with 95% of enterprises using cloud by 2030, expands the attack surface. Zero-trust adoption, mandated in U.S. federal agencies, drives continuous verification. Supply chain attacks, up 300% since 2020, fuel third-party risk management. Emerging markets in APAC and MEA offer growth via digital transformation, while AI automation reduces MTTR by 60%.
Challenges include vulnerability overload, with enterprises scanning 10,000+ vulnerabilities monthly, requiring advanced prioritization. False positives, still at 40% in some platforms, erode trust. Skills shortages—needing 3.5 million cybersecurity professionals globally—limit effective deployment. Regulatory fragmentation—NIST, GDPR, China’s Cybersecurity Law—complicates compliance. Legacy system scanning remains incomplete, and open-source component risks grow unchecked. Innovation in AI-driven remediation and integration with XDR will shape market resilience.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Security & Vulnerability Management (SVM) Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Security & Vulnerability Management (SVM) Market in North America (2020-2030)
8.1 Security & Vulnerability Management (SVM) Market Size
8.2 Security & Vulnerability Management (SVM) Market by End Use
8.3 Competition by Players/Suppliers
8.4 Security & Vulnerability Management (SVM) Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Security & Vulnerability Management (SVM) Market in South America (2020-2030)
9.1 Security & Vulnerability Management (SVM) Market Size
9.2 Security & Vulnerability Management (SVM) Market by End Use
9.3 Competition by Players/Suppliers
9.4 Security & Vulnerability Management (SVM) Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Security & Vulnerability Management (SVM) Market in Asia & Pacific (2020-2030)
10.1 Security & Vulnerability Management (SVM) Market Size
10.2 Security & Vulnerability Management (SVM) Market by End Use
10.3 Competition by Players/Suppliers
10.4 Security & Vulnerability Management (SVM) Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Security & Vulnerability Management (SVM) Market in Europe (2020-2030)
11.1 Security & Vulnerability Management (SVM) Market Size
11.2 Security & Vulnerability Management (SVM) Market by End Use
11.3 Competition by Players/Suppliers
11.4 Security & Vulnerability Management (SVM) Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Security & Vulnerability Management (SVM) Market in MEA (2020-2030)
12.1 Security & Vulnerability Management (SVM) Market Size
12.2 Security & Vulnerability Management (SVM) Market by End Use
12.3 Competition by Players/Suppliers
12.4 Security & Vulnerability Management (SVM) Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Security & Vulnerability Management (SVM) Market (2020-2025)
13.1 Security & Vulnerability Management (SVM) Market Size
13.2 Security & Vulnerability Management (SVM) Market by End Use
13.3 Competition by Players/Suppliers
13.4 Security & Vulnerability Management (SVM) Market Size by Type
Chapter 14 Global Security & Vulnerability Management (SVM) Market Forecast (2025-2030)
14.1 Security & Vulnerability Management (SVM) Market Size Forecast
14.2 Security & Vulnerability Management (SVM) Application Forecast
14.3 Competition by Players/Suppliers
14.4 Security & Vulnerability Management (SVM) Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Qualys
15.1.1 Company Profile
15.1.2 Main Business and Security & Vulnerability Management (SVM) Information
15.1.3 SWOT Analysis of Qualys
15.1.4 Qualys Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 Tenable
15.2.1 Company Profile
15.2.2 Main Business and Security & Vulnerability Management (SVM) Information
15.2.3 SWOT Analysis of Tenable
15.2.4 Tenable Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 Rapid7
15.3.1 Company Profile
15.3.2 Main Business and Security & Vulnerability Management (SVM) Information
15.3.3 SWOT Analysis of Rapid7
15.3.4 Rapid7 Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 IBM
15.4.1 Company Profile
15.4.2 Main Business and Security & Vulnerability Management (SVM) Information
15.4.3 SWOT Analysis of IBM
15.4.4 IBM Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 Microsoft
15.5.1 Company Profile
15.5.2 Main Business and Security & Vulnerability Management (SVM) Information
15.5.3 SWOT Analysis of Microsoft
15.5.4 Microsoft Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 Cisco
15.6.1 Company Profile
15.6.2 Main Business and Security & Vulnerability Management (SVM) Information
15.6.3 SWOT Analysis of Cisco
15.6.4 Cisco Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.7 ServiceNow
15.7.1 Company Profile
15.7.2 Main Business and Security & Vulnerability Management (SVM) Information
15.7.3 SWOT Analysis of ServiceNow
15.7.4 ServiceNow Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.8 BeyondTrust
15.8.1 Company Profile
15.8.2 Main Business and Security & Vulnerability Management (SVM) Information
15.8.3 SWOT Analysis of BeyondTrust
15.8.4 BeyondTrust Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.9 Greenbone
15.9.1 Company Profile
15.9.2 Main Business and Security & Vulnerability Management (SVM) Information
15.9.3 SWOT Analysis of Greenbone
15.9.4 Greenbone Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
15.10 ManageEngine
15.10.1 Company Profile
15.10.2 Main Business and Security & Vulnerability Management (SVM) Information
15.10.3 SWOT Analysis of ManageEngine
15.10.4 ManageEngine Security & Vulnerability Management (SVM) Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of Security & Vulnerability Management (SVM) Report
Table Data Sources of Security & Vulnerability Management (SVM) Report
Table Major Assumptions of Security & Vulnerability Management (SVM) Report
Table Security & Vulnerability Management (SVM) Classification
Table Security & Vulnerability Management (SVM) Applications
Table Drivers of Security & Vulnerability Management (SVM) Market
Table Restraints of Security & Vulnerability Management (SVM) Market
Table Opportunities of Security & Vulnerability Management (SVM) Market
Table Threats of Security & Vulnerability Management (SVM) Market
Table Raw Materials Suppliers
Table Different Production Methods of Security & Vulnerability Management (SVM)
Table Cost Structure Analysis of Security & Vulnerability Management (SVM)
Table Key End Users
Table Latest News of Security & Vulnerability Management (SVM) Market
Table Merger and Acquisition
Table Planned/Future Project of Security & Vulnerability Management (SVM) Market
Table Policy of Security & Vulnerability Management (SVM) Market
Table 2020-2030 North America Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 North America Security & Vulnerability Management (SVM) Market Size by Application
Table 2020-2025 North America Security & Vulnerability Management (SVM) Key Players Revenue
Table 2020-2025 North America Security & Vulnerability Management (SVM) Key Players Market Share
Table 2020-2030 North America Security & Vulnerability Management (SVM) Market Size by Type
Table 2020-2030 United States Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Canada Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Mexico Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 South America Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 South America Security & Vulnerability Management (SVM) Market Size by Application
Table 2020-2025 South America Security & Vulnerability Management (SVM) Key Players Revenue
Table 2020-2025 South America Security & Vulnerability Management (SVM) Key Players Market Share
Table 2020-2030 South America Security & Vulnerability Management (SVM) Market Size by Type
Table 2020-2030 Brazil Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Argentina Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Chile Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Peru Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Asia & Pacific Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Asia & Pacific Security & Vulnerability Management (SVM) Market Size by Application
Table 2020-2025 Asia & Pacific Security & Vulnerability Management (SVM) Key Players Revenue
Table 2020-2025 Asia & Pacific Security & Vulnerability Management (SVM) Key Players Market Share
Table 2020-2030 Asia & Pacific Security & Vulnerability Management (SVM) Market Size by Type
Table 2020-2030 China Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 India Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Japan Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 South Korea Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Southeast Asia Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Australia Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Europe Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Europe Security & Vulnerability Management (SVM) Market Size by Application
Table 2020-2025 Europe Security & Vulnerability Management (SVM) Key Players Revenue
Table 2020-2025 Europe Security & Vulnerability Management (SVM) Key Players Market Share
Table 2020-2030 Europe Security & Vulnerability Management (SVM) Market Size by Type
Table 2020-2030 Germany Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 France Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 United Kingdom Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Italy Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Spain Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Belgium Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Netherlands Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Austria Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Poland Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Russia Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 MEA Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 MEA Security & Vulnerability Management (SVM) Market Size by Application
Table 2020-2025 MEA Security & Vulnerability Management (SVM) Key Players Revenue
Table 2020-2025 MEA Security & Vulnerability Management (SVM) Key Players Market Share
Table 2020-2030 MEA Security & Vulnerability Management (SVM) Market Size by Type
Table 2020-2030 Egypt Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Israel Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 South Africa Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Gulf Cooperation Council Countries Security & Vulnerability Management (SVM) Market Size
Table 2020-2030 Turkey Security & Vulnerability Management (SVM) Market Size
Table 2020-2025 Global Security & Vulnerability Management (SVM) Market Size by Region
Table 2020-2025 Global Security & Vulnerability Management (SVM) Market Size Share by Region
Table 2020-2025 Global Security & Vulnerability Management (SVM) Market Size by Application
Table 2020-2025 Global Security & Vulnerability Management (SVM) Market Share by Application
Table 2020-2025 Global Security & Vulnerability Management (SVM) Key Vendors Revenue
Table 2020-2025 Global Security & Vulnerability Management (SVM) Key Vendors Market Share
Table 2020-2025 Global Security & Vulnerability Management (SVM) Market Size by Type
Table 2020-2025 Global Security & Vulnerability Management (SVM) Market Share by Type
Table 2025-2030 Global Security & Vulnerability Management (SVM) Market Size by Region
Table 2025-2030 Global Security & Vulnerability Management (SVM) Market Size Share by Region
Table 2025-2030 Global Security & Vulnerability Management (SVM) Market Size by Application
Table 2025-2030 Global Security & Vulnerability Management (SVM) Market Share by Application
Table 2025-2030 Global Security & Vulnerability Management (SVM) Key Vendors Revenue
Table 2025-2030 Global Security & Vulnerability Management (SVM) Key Vendors Market Share
Table 2025-2030 Global Security & Vulnerability Management (SVM) Market Size by Type
Table 2025-2030 Security & Vulnerability Management (SVM) Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Security & Vulnerability Management (SVM) Picture
Figure 2020-2030 North America Security & Vulnerability Management (SVM) Market Size and CAGR
Figure 2020-2030 South America Security & Vulnerability Management (SVM) Market Size and CAGR
Figure 2020-2030 Asia & Pacific Security & Vulnerability Management (SVM) Market Size and CAGR
Figure 2020-2030 Europe Security & Vulnerability Management (SVM) Market Size and CAGR
Figure 2020-2030 MEA Security & Vulnerability Management (SVM) Market Size and CAGR
Figure 2020-2025 Global Security & Vulnerability Management (SVM) Market Size and Growth Rate
Figure 2025-2030 Global Security & Vulnerability Management (SVM) Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
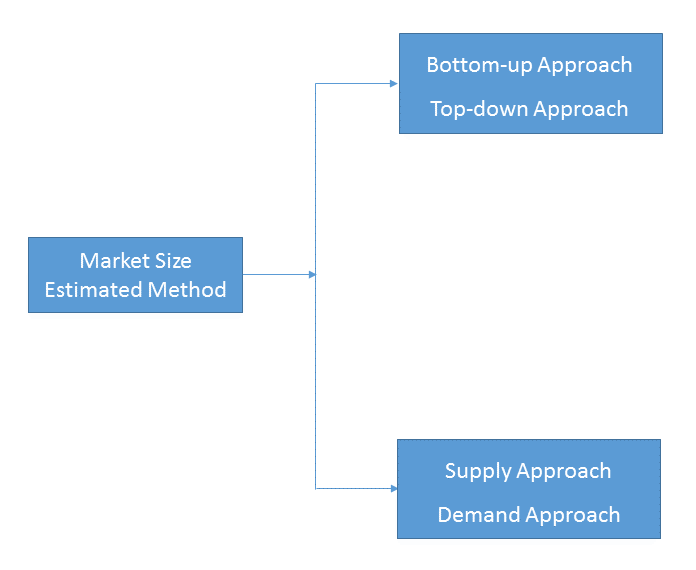
1)Top-down & Bottom-up Approach
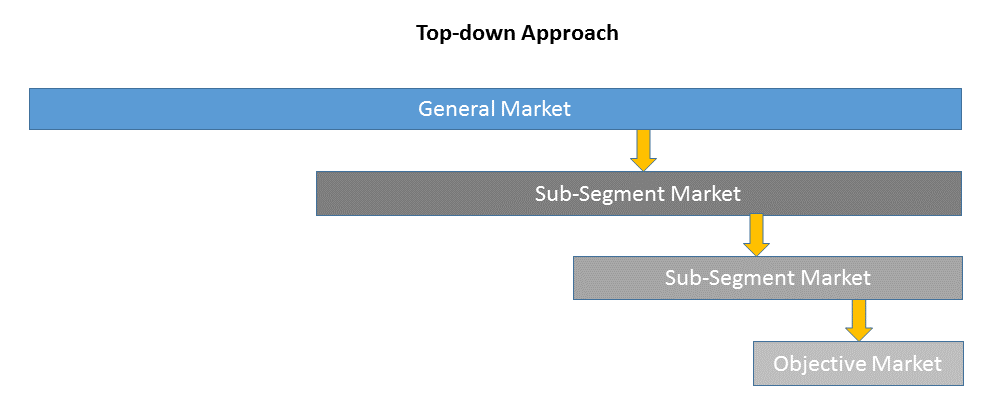
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
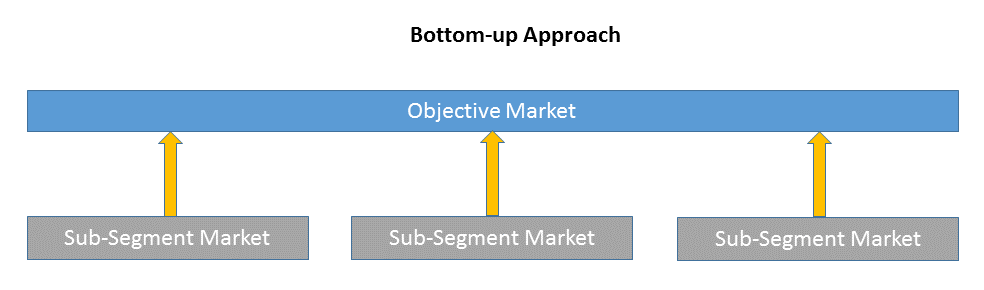
Bottom-up approach size the objective market by collecting the sub-segment information.
2)Supply & Demand Approach
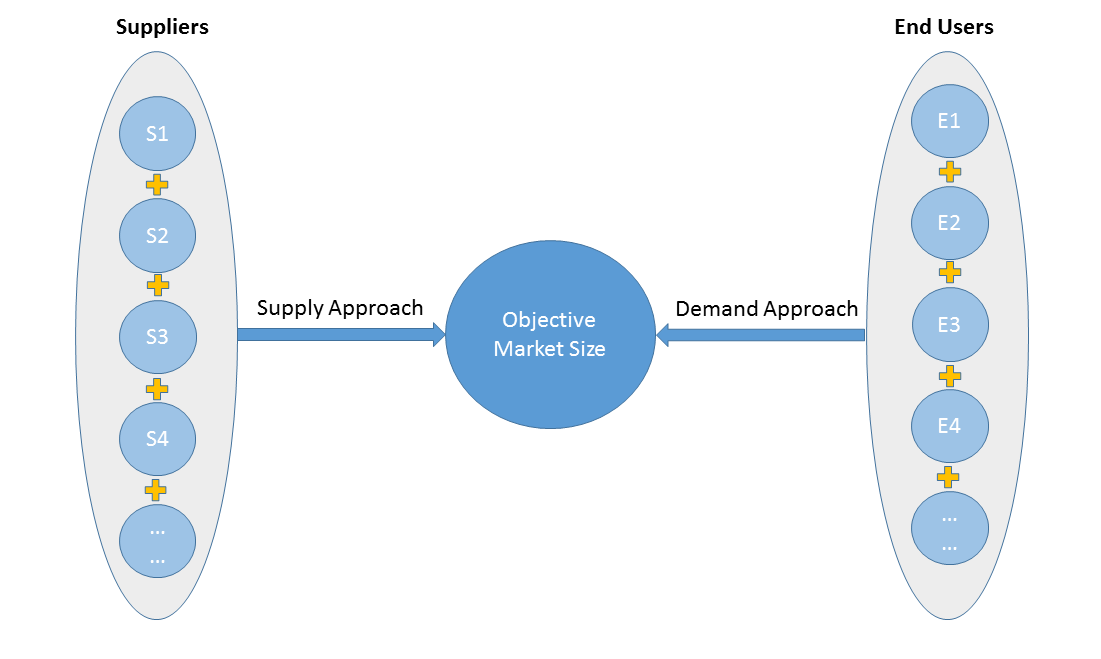
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
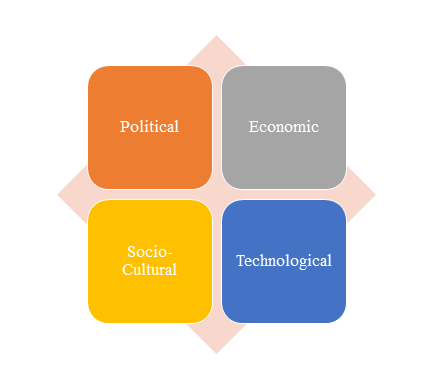
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
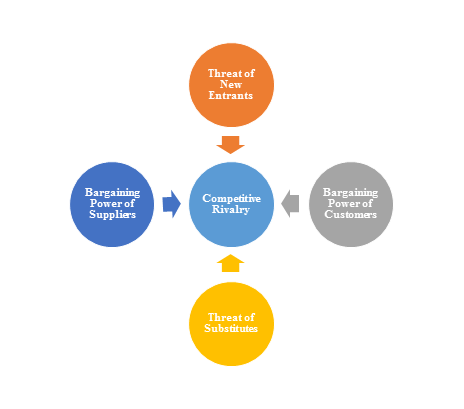
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
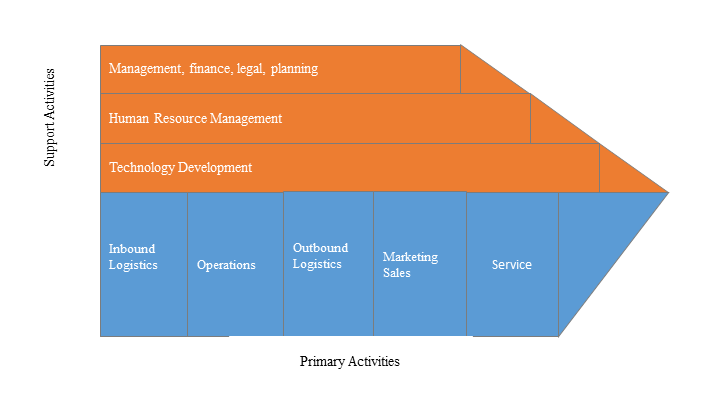
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
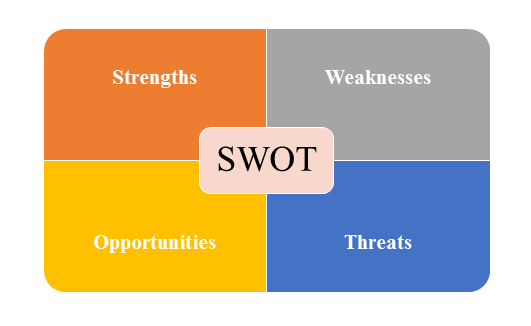
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |