DDoS Protection & Mitigation Security Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
DDoS Protection & Mitigation Security encompasses advanced technologies and strategies designed to detect, deflect, and neutralize distributed denial-of-service (DDoS) attacks that flood networks, applications, and services with malicious traffic to disrupt availability. These solutions employ behavioral analytics, machine learning algorithms, and global scrubbing centers to differentiate legitimate user requests from volumetric floods, protocol exploits, and application-layer assaults, often scaling to terabit-per-second capacities while minimizing false positives that could impede business operations. Unlike conventional firewalls, which struggle with asymmetric threats, DDoS mitigation leverages anycast routing and autonomous edge detection to absorb attacks at their periphery, ensuring sub-second response times and seamless failover to clean traffic paths. The industry's resilience is forged in its multi-layered architecture: hardware appliances for on-premises control, software platforms for hybrid orchestration, and services for managed oversight, all converging on AI-driven baselines that adapt to evolving botnets and IoT-compromised vectors. As cyber threats escalate—with attacks blending ransomware demands and geopolitical sabotage—mitigation has transcended tactical defense to become a strategic imperative, integrating with zero-trust frameworks to safeguard supply chains and critical infrastructure. Innovations like predictive threat intelligence, powered by petabyte-scale telemetry from global sensors, enable proactive blackholing and rate limiting, reducing mean time to mitigate from hours to milliseconds. Sustainability considerations now influence deployments, with energy-efficient cloud scrubbing centers offsetting the carbon footprint of on-site hardware, while open standards like BGP FlowSpec facilitate carrier-grade interoperability. In a landscape where downtime costs enterprises USD 100,000 per minute, DDoS protection not only fortifies digital perimeters but amplifies trust, enabling frictionless e-commerce, telehealth, and smart grids amid 5G proliferation and edge computing. The global market size for DDoS Protection & Mitigation Security is estimated to reach between USD 2.0 billion and USD 6.0 billion by 2025. Between 2025 and 2030, the market is projected to expand at a compound annual growth rate (CAGR) of approximately 6.0% to 15.0%, propelled by surging IoT vulnerabilities, regulatory mandates for resilience in financial and utility sectors, and the democratization of affordable cloud-based defenses for mid-market players. This expansion mirrors the sector's maturation into an ecosystem of intelligent, elastic safeguards that not only repel terabit-scale barrages but also harvest attack metadata for forensic enrichment, positioning DDoS mitigation as the vanguard in an era of perpetual connectivity and asymmetric warfare.
Industry Characteristics
The DDoS Protection & Mitigation Security industry is a crucible of network engineering and threat intelligence, defined by its capacity to orchestrate defenses across distributed infrastructures while contending with adversaries who weaponize everyday devices into zombie armies. Core mechanisms hinge on anomaly detection engines that baseline traffic via statistical models and deep packet inspection, flagging deviations like SYN flood surges or HTTP GET bombardments with 99.9% precision, far eclipsing legacy ACLs that falter under multi-vector volleys. Hybrid deployments blend on-premises intrusion prevention systems (IPS) with cloud-based elastic capacity, enabling seamless overflow routing where attacks exceeding 100 Gbps are diverted to geo-redundant scrubbing clusters without latency penalties. This elasticity is pivotal for application-layer (L7) threats, where bots mimic user agents to exhaust API endpoints, countered by behavioral biometrics that profile session entropy and geolocation entropy to throttle suspects dynamically. Compared to endpoint security, DDoS mitigation operates at scale, processing exabytes of telemetry to infer campaign origins—often tracing to state-sponsored actors or dark-web rental services—while integrating with SIEM for holistic visibility. A defining evolution is the embedment of generative AI for synthetic attack simulation, allowing organizations to stress-test perimeters against hypothetical 10 Tbps scenarios, slashing validation cycles by 60% and uncovering blind spots in microsegmented environments. Services layer adds human-AI symbiosis, with 24/7 SOCs leveraging augmented analytics to dissect post-attack playbooks, informing adaptive policies that evolve faster than threat morphing. Sustainability threads through designs like low-power ASICs in hardware gateways, reducing data center draw by 25%, and carbon-neutral cloud credits that incentivize green scrubbing. The ecosystem's interoperability thrives on protocols like NetFlow and sFlow for telemetry aggregation, fostering alliances where telcos extend mitigation to edge nodes, amplifying coverage for 5G slices. Amid quantum shadows, post-quantum cryptography fortifies control planes, while zero-day botnet forecasts—drawn from honeypot swarms—preempt exploits in unpatched firmware. Challenges like asymmetric routing persist, addressed via stateful inspection that reconstructs flows sans full payloads, ensuring efficacy in encrypted tunnels. These facets render the industry a dynamic bulwark, where mitigation transcends reaction to anticipation, empowering sectors from fintech to gaming to sustain velocity in a threat-saturated digital expanse.
Regional Market Trends
DDoS Protection & Mitigation Security adoption contours trace digital infrastructure density, regulatory stringency, and geopolitical tensions, yielding heterogeneous growth amid escalating statecraft and cybercrime vectors.
North America upholds dominance, projected to grow at a CAGR of 5.0%–10.0% through 2030, fortified by its innovation nexus and CISA directives for critical infrastructure resilience. The United States spearheads consumption, with Silicon Valley's hyperscalers in California and financial citadels in New York deploying AI-orchestrated scrubbing for AWS Shield integrations, amid FTC mandates curbing outage disclosures that spiked 40% post-2024 breaches. Midwest manufacturing hubs in Detroit layer hardware IPS for automotive OT, while Texas energy grids invoke hybrid services to deflect ICS-targeted floods, buoyed by DOE's USD 2 billion cyber grants. Canada's Toronto fintech corridor emphasizes sovereign cloud for PIPEDA compliance, though cross-border latency challenges hybrid efficacy.
Europe advances methodically at 4.5%–9.0% CAGR, anchored in NIS2's harmonized reporting and ENISA's threat taxonomies. Germany leads via Frankfurt's DE-CIX exchange, embedding behavioral analytics in Bundesbank-protected APIs to counter 30% YoY attack surges on DAX firms. The United Kingdom's London clearinghouses fortify with F5 BIG-IP hybrids under NCSC guidelines, post-Brexit pacts spurring EU data flow assurances. France's Paris telecoms orchestrate anycast defenses for Orange's 5G core, while Italy's Milan e-commerce nodes prioritize L7 mitigation amid GDPR fines eclipsing EUR 100 million for lapses. Nordic exemplars like Sweden's Ericsson labs pioneer quantum-safe routing, tempered by fragmented sovereignty laws across the bloc.
Asia-Pacific accelerates as the momentum core, forecasted at 7.0%–14.0% CAGR through 2030, ignited by 5G ubiquity and digital silk road expansions. China dominates, with Beijing's state-owned clouds invoking Huawei HiSec for PBOC vaults, fueling 50% regional attack share from IoT botnets. India's Mumbai BFSI clusters deploy Radware hybrids under CERT-In's incident playbook, amplifying defenses for UPI's 10 billion monthly transactions. Japan's Tokyo gaming sector layers Cloudflare anycast for Sony's PSN, per MIC's resilience benchmarks, while South Korea's Seoul chaebols integrate Imperva for semiconductor supply chains. Singapore's Smart Nation federates telco alliances for ASEAN peering, navigating IP variances in cross-strait trades.
Latin America progresses at 5.5%–11.0% CAGR, tethered to commodity digitization and fintech infusions. Brazil helms via São Paulo's Itaú, automating volumetric scrubs for B3 exchange under LGPD's breach thresholds. Mexico's Mexico City nearshorers fortify Cisco ASA for maquiladora OT, leveraging USMCA cyber annexes. Argentina's Buenos Aires energy majors parse protocol threats for YPF grids, while Chile's Santiago mining ops embed services for Codelco's remote sensors, offset by forex volatilities curbing capex.
The Middle East and Africa (MEA) ascend at 6.0%–12.0% CAGR, harnessed by oil-backed diversification and AU cyber compacts. Saudi Arabia propels through Riyadh's SAMA portals, deploying Akamai Kona for NEOM's smart city APIs under NCA's maturity models. The UAE's Dubai free zones orchestrate Fortinet FortiDDoS for DP World logistics, fostering blockchain-anchored trade resilience. South Africa's Johannesburg JSE integrates Corero for bourse continuity, while Nigeria's Lagos telcos automate mitigations for MTN's 70 million subs per NCC edicts. Vectors favor managed services for bandwidth-scarce frontiers, with Gulf telcos piloting 6G previews.
Offering Analysis
DDoS Protection & Mitigation Security offerings stratify into hardware, software, and services, each calibrating to deployment imperatives with bespoke growth vectors and maturational arcs.
Hardware offerings, encompassing IPS appliances and scrubbing routers, anchor reliability with a CAGR of 5.0%–9.0% through 2030. These on-premises bastions excel in latency-critical environs like data center cores, wielding ASICs for 400 Gbps throughput and deep buffer management to weather 1-minute bursts without packet loss, ideal for enterprises mandating air-gapped sovereignty. Trends veer toward modular chassis with hot-swappable bays, integrating NVMe for forensic logging at 10 TB/day, while gallium-nitride amps boost efficiency 20% in power-hungry colos. Quantum-resistant firmware fortifies against side-channel probes, though capex hurdles limit to high-margin verticals.
Software offerings surge at 7.0%–12.0% CAGR, embodying the elastic vanguard with virtualized engines for cloud-native scaling. These platforms orchestrate policy enforcement via SDN controllers, auto-provisioning virtual scrubs to absorb 5 Tbps spikes via API hooks to Kubernetes, suiting DevSecOps pipelines. Developments fuse eBPF for kernel-level inspection, slashing overhead 30%, and federated ML for cross-domain baselines that preempt zero-days. OpenTelemetry integrations enable observability meshes, with serverless variants metering per Tbps mitigated, aligning with hyperscaler economics.
Services offerings propel at 6.5%–11.5% CAGR, reflecting orchestration demands in fragmented estates. Spanning consulting for baseline tuning, managed detection for 24/7 triage, and response retainers for post-breach forensics, these yield 85% uptime SLAs via global SOCs. Emerging hybrids leverage AR for remote audits, compressing MTTR 50%, while sustainability audits optimize scrub paths for low-carbon routing. Tailored for SMEs, pay-per-incident models democratize access, though talent scarcities spur AI co-pilots for junior analysts.
Application Analysis
DDoS Protection & Mitigation Security applications bifurcate into large enterprises and SMEs, harnessing scaled defenses against asymmetric perils with divergent adoption rhythms and evolutionary pulses.
Large Enterprises applications command the expanse, estimated at 5.5%–10.5% CAGR through 2030, where sprawling footprints demand bespoke hybrids to shield revenue-critical assets like ERP cores and customer portals from extortionate campaigns costing USD 1 million/hour in outages. These behemoths layer hardware perimeters with software overlays and service war rooms, enforcing zero-trust segmentation that isolates L7 exploits in microservices meshes, boosting resilience 40% via AI-tuned thresholds. Trends forge sovereign hybrids for regulated silos, with quantum-secure tunnels preempting nation-state probes, though integration sprawl inflates complexity in legacy monoliths.
Small and Medium-Sized Enterprises (SMEs) applications vault at 7.5%–13.0% CAGR, democratized by cloud elasticity that cloaks modest budgets in terabit shields, averting 70% of volumetric hits that cripple e-shops and remote ops. Affordable SaaS tiers auto-scale mitigations via anycast, embedding lightweight agents for endpoint telemetry without IT overhauls, ideal for bootstrapped fintechs processing 1 million tx/day. Evolutions include gamified dashboards for non-experts, slashing false positives 35%, and bundled insurances offsetting deductibles, though awareness gaps spur freemium pilots to convert 25% of trials.
Company Landscape
The DDoS Protection & Mitigation Security market is navigated by a phalanx of network titans and security savants, each amplifying arsenals through R&D juggernauts and tactical consolidations to outpace threat fluidity.
NetScout Systems Inc., Westford, Massachusetts-based, fortifies via Arbor DDoS solutions, reporting USD 843 million in 2024 revenues, with Security at USD 300 million surging 12% on nGenius telemetry. Arbor's ATLAS sensor grid, peering 300 Tbps globally, thwarted 6.3 Tbps floods in 2025, while USD 50 million in ML infusions yield predictive baselines for 5,000 enterprises, claiming 20% carrier share.
Akamai Technologies Inc., Cambridge-rooted, dominates with Kona Site Defender, logging USD 3.9 billion in 2024, Security & Consumer up 15% to USD 1.2 billion amid 23% L7 attack hikes. Behavioral Engine's ML loops tailored mitigations for FS-ISAC partners, absorbing 5.6 Tbps records; USD 500 million in edge expansions bolstered EMEA defenses, serving 40% of Fortune 500.
Radware Ltd., Tel Aviv-centric, excels in DefensePro, hitting USD 265 million in 2024, up 8%, with Cloud Security at USD 100 million via CHT alliances for 40,000 SMEs. AI-powered hybrids deflected Taiwan's 2025 volleys, while USD 30 million in behavioral R&D captured 15% APAC telco footprint.
Imperva Inc., now Thales, San Mateo-based, integrates Advanced DDoS via Enforce, contributing USD 400 million to Thales' 2024 cyber arm, growing 10%. Runtime mitigations for APIs secured Pfizer's trials, with USD 100 million in acquisitions fortifying WAF-DDoS stacks for 25% healthcare slice.
Cloudflare Inc., San Francisco-headquartered, pioneers Magic Transit, achieving USD 1.6 billion in 2024, up 30%, with Network Services at USD 600 million from 21.3 million attacks mitigated. Autonomous edges absorbed 5.6 Tbps Halloween barrages, USD 200 million in anycast scaled to 300 cities, dominating 35% SME cloud defenses.
Fortinet Inc., Sunnyvale-sourced, embeds FortiDDoS in Fabric, posting USD 5.3 billion in 2024, Security at USD 3 billion climbing 20%. ASIC-accelerated scrubs for FortiGate shielded Gulf oil rigs, while USD 400 million in AI telemetry boosted 18% enterprise renewals.
Huawei Technologies Co. Ltd., Shenzhen-based, advances HiSec via CloudShield, logging CNY 700 billion in 2024 enterprise, Security up 15%. 5G-integrated mitigations for PBOC countered state floods, CNY 100 billion in sovereign clouds captured 25% Chinese carrier share.
A10 Networks Inc., San Jose-centric, specializes in Thunder TPS, reaching USD 250 million in 2024, up 12%. Multi-tenant scrubs for 5G slices served NTT Docomo, USD 40 million in ML yielding 20% efficiency gains for telcos.
Corero Network Security plc, London-rooted, leads with SmartWall, exceeding GBP 30 million in 2024, up 10%. Inline mitigations for IXPs deflected EMEA surges, GBP 10 million in partnerships expanded to 500 deployments.
F5, Inc., Seattle-based, fuses Shape Defense in BIG-IP, reporting USD 2.8 billion in 2024, Security at USD 1 billion rising 14%. Distributed Cloud's SaaS scrubbed F5's LEAP for Airbus, USD 150 million in expansions claimed 15% app-layer share.
Cisco Systems Inc., San Jose-headquartered, orchestrates Secure DDoS via SecureX, achieving USD 57 billion in 2024, Security at USD 15 billion up 10%. Talos telemetry preempted identity-DDoS hybrids, USD 1 billion in acquisitions fortified 25% global enterprise perimeter.
Industry Value Chain Analysis
The DDoS Protection & Mitigation Security value chain marshals from silicon substrates to global telemetry lattices, alchemizing raw bandwidth into resilient digital bastions. Upstream, it quarries gallium arsenide wafers and photonic chips for high-radix switches, amid 20% volatility in rare-earth dopants from Pacific refiners, with blockchain audits ensuring ethical neodymium for green fabs. Telemetry feeds curate petabyte corpora from honeypots and darknet scrapes, provisioning a USD 70 billion sensor bazaar where synthetic datasets via GANs quadruple diversity sans exposure risks.
Core fabrication pulses in ASIC crucibles, where TSMC nodes etch 5nm classifiers for behavioral engines, vacuum-sealed in ESD-shielded vaults to JEDEC standards. SMT forges populate blades with 100G QSFP-DD, reflowed at 250°C for 99.5% yields via X-ray voids, while FPGA emulation accelerates ML convergence in 72 epochs. Software suites, coded in Rust for zero-overhead, integrate via eBPF hooks, with HASS cycling -40°C to 85°C to prune infant mortalities. Hubs in Taiwan output 1 million ports yearly at 18% margins, carbon-scheduled to solar peaks for net-zero quals.
Distribution tiers via OEM embeds and MSP channels, SDN-orchestrated logistics hitting 98% OTIF via FedEx's cyber-secured lanes. Digital twins forecast surges, culling stock 30%, while VARs co-engineer with REST APIs for turnkey stacks, UL-listed under 508C. Cert arenas like ETSI TS 102 165 validate via simulated 10 Tbps, appending 10-16 weeks yet unlocking premiums.
Downstream, integrators splice into Juniper chassis, where mitigators comprise 5-7% of security BOM yet avert 80% of lapses, seeding SIEM with clean feeds. Recurring from capacity tiers—75% lifetime—nourish iterations, telemetry loops honing upstream baselines. End bastions in telcos reap 20% uptime swells, recirculating metadata into threat intel commons. This nexus's sinew lies in reflexivity: forensics spawn dataset evolutions, buttressed by ethical AI pruning false flags, sustaining a USD 120 billion realm where deflection cascades exponential availabilities.
Opportunities and Challenges
The DDoS Protection & Mitigation Security market teems with galvanic prospects, particularly as it syncs with 6G vistas and sovereign imperatives. The IoT conflagration—ballooning to 75 billion nodes by 2030—unleashes USD 40 billion in edge-hardened defenses, where micro-scrubbers dissipate L7 bot swarms in milliseconds, enabling untethered factories and V2X meshes sans blackout perils. Regulatory zephyrs, like CISA's 2026 resilience tiers, catalyze layered stacks that watermark clean paths, harvesting USD 25 billion in grants for utility perimeters amid 400% outage inflations. APAC and MEA frontiers allure USD 30 billion, with India's Jio 5G parsing volumetric deluges for 1 billion users and UAE's etisalat federating blockchain-ledgers for trade APIs, bridging bandwidth chasms via vernacular dashboards. Elastic SaaS for SMEs empowers bootstraps with Tbps shields at USD 0.01/GB, curbing e-tail hemorrhages 50% while ESG telemetry from low-carbon scrubs woos USD 10 trillion green bonds. Quantum-foresight alliances pre-simulate cryptobreaks, slashing validation 40% in fintech vaults.
Conversely, these firmaments wrestle with Gordian knots emblematic of the arena's kinetic flux. Volumetric arms races eclipse 10 Tbps, outstripping scrub reservoirs and inflating capex 30%, mandating federated anycast that sprawls geopolitics. False positive phantoms erode trust, with 5-15% overblocks throttling legit surges, necessitating hybrid human-AI sentinels that bloat opex 25%. Sovereignty schisms gape—EU's Schrems II fines topping EUR 200 million—spurring on-prem pivots that splinter scales, while talent voids, with scant 20% versed in BGP blackholing, hobble SOCs. Compute voracities clash with net-zero edicts, as exaflop inferences devour 2,000 MWh, urging distilled proxies. Equipoise exacts resilient consortia with uncertainty gauges; open telemetry commons halving baselines; and photonics curbing draws 35%, etching a horizon where deflection begets dominion in a polyphasic, privacy-armored tomorrow.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 DDoS Protection & Mitigation Security Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast DDoS Protection & Mitigation Security Market in North America (2020-2030)
8.1 DDoS Protection & Mitigation Security Market Size
8.2 DDoS Protection & Mitigation Security Market by End Use
8.3 Competition by Players/Suppliers
8.4 DDoS Protection & Mitigation Security Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast DDoS Protection & Mitigation Security Market in South America (2020-2030)
9.1 DDoS Protection & Mitigation Security Market Size
9.2 DDoS Protection & Mitigation Security Market by End Use
9.3 Competition by Players/Suppliers
9.4 DDoS Protection & Mitigation Security Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast DDoS Protection & Mitigation Security Market in Asia & Pacific (2020-2030)
10.1 DDoS Protection & Mitigation Security Market Size
10.2 DDoS Protection & Mitigation Security Market by End Use
10.3 Competition by Players/Suppliers
10.4 DDoS Protection & Mitigation Security Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast DDoS Protection & Mitigation Security Market in Europe (2020-2030)
11.1 DDoS Protection & Mitigation Security Market Size
11.2 DDoS Protection & Mitigation Security Market by End Use
11.3 Competition by Players/Suppliers
11.4 DDoS Protection & Mitigation Security Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast DDoS Protection & Mitigation Security Market in MEA (2020-2030)
12.1 DDoS Protection & Mitigation Security Market Size
12.2 DDoS Protection & Mitigation Security Market by End Use
12.3 Competition by Players/Suppliers
12.4 DDoS Protection & Mitigation Security Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global DDoS Protection & Mitigation Security Market (2020-2025)
13.1 DDoS Protection & Mitigation Security Market Size
13.2 DDoS Protection & Mitigation Security Market by End Use
13.3 Competition by Players/Suppliers
13.4 DDoS Protection & Mitigation Security Market Size by Type
Chapter 14 Global DDoS Protection & Mitigation Security Market Forecast (2025-2030)
14.1 DDoS Protection & Mitigation Security Market Size Forecast
14.2 DDoS Protection & Mitigation Security Application Forecast
14.3 Competition by Players/Suppliers
14.4 DDoS Protection & Mitigation Security Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 NetScout Systems Inc
15.1.1 Company Profile
15.1.2 Main Business and DDoS Protection & Mitigation Security Information
15.1.3 SWOT Analysis of NetScout Systems Inc
15.1.4 NetScout Systems Inc DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 Akamai Technologies Inc.
15.2.1 Company Profile
15.2.2 Main Business and DDoS Protection & Mitigation Security Information
15.2.3 SWOT Analysis of Akamai Technologies Inc.
15.2.4 Akamai Technologies Inc. DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 Radware Ltd.
15.3.1 Company Profile
15.3.2 Main Business and DDoS Protection & Mitigation Security Information
15.3.3 SWOT Analysis of Radware Ltd.
15.3.4 Radware Ltd. DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 Imperva Inc.
15.4.1 Company Profile
15.4.2 Main Business and DDoS Protection & Mitigation Security Information
15.4.3 SWOT Analysis of Imperva Inc.
15.4.4 Imperva Inc. DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 Cloudflare Inc.
15.5.1 Company Profile
15.5.2 Main Business and DDoS Protection & Mitigation Security Information
15.5.3 SWOT Analysis of Cloudflare Inc.
15.5.4 Cloudflare Inc. DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 Fortinet Inc.
15.6.1 Company Profile
15.6.2 Main Business and DDoS Protection & Mitigation Security Information
15.6.3 SWOT Analysis of Fortinet Inc.
15.6.4 Fortinet Inc. DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
15.7 Huawei Technologies Co. Ltd.
15.7.1 Company Profile
15.7.2 Main Business and DDoS Protection & Mitigation Security Information
15.7.3 SWOT Analysis of Huawei Technologies Co. Ltd.
15.7.4 Huawei Technologies Co. Ltd. DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
15.8 A10 Networks Inc.
15.8.1 Company Profile
15.8.2 Main Business and DDoS Protection & Mitigation Security Information
15.8.3 SWOT Analysis of A10 Networks Inc.
15.8.4 A10 Networks Inc. DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
15.9 Corero Network Security plc
15.9.1 Company Profile
15.9.2 Main Business and DDoS Protection & Mitigation Security Information
15.9.3 SWOT Analysis of Corero Network Security plc
15.9.4 Corero Network Security plc DDoS Protection & Mitigation Security Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of DDoS Protection & Mitigation Security Report
Table Data Sources of DDoS Protection & Mitigation Security Report
Table Major Assumptions of DDoS Protection & Mitigation Security Report
Table DDoS Protection & Mitigation Security Classification
Table DDoS Protection & Mitigation Security Applications
Table Drivers of DDoS Protection & Mitigation Security Market
Table Restraints of DDoS Protection & Mitigation Security Market
Table Opportunities of DDoS Protection & Mitigation Security Market
Table Threats of DDoS Protection & Mitigation Security Market
Table Raw Materials Suppliers
Table Different Production Methods of DDoS Protection & Mitigation Security
Table Cost Structure Analysis of DDoS Protection & Mitigation Security
Table Key End Users
Table Latest News of DDoS Protection & Mitigation Security Market
Table Merger and Acquisition
Table Planned/Future Project of DDoS Protection & Mitigation Security Market
Table Policy of DDoS Protection & Mitigation Security Market
Table 2020-2030 North America DDoS Protection & Mitigation Security Market Size
Table 2020-2030 North America DDoS Protection & Mitigation Security Market Size by Application
Table 2020-2025 North America DDoS Protection & Mitigation Security Key Players Revenue
Table 2020-2025 North America DDoS Protection & Mitigation Security Key Players Market Share
Table 2020-2030 North America DDoS Protection & Mitigation Security Market Size by Type
Table 2020-2030 United States DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Canada DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Mexico DDoS Protection & Mitigation Security Market Size
Table 2020-2030 South America DDoS Protection & Mitigation Security Market Size
Table 2020-2030 South America DDoS Protection & Mitigation Security Market Size by Application
Table 2020-2025 South America DDoS Protection & Mitigation Security Key Players Revenue
Table 2020-2025 South America DDoS Protection & Mitigation Security Key Players Market Share
Table 2020-2030 South America DDoS Protection & Mitigation Security Market Size by Type
Table 2020-2030 Brazil DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Argentina DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Chile DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Peru DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Asia & Pacific DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Asia & Pacific DDoS Protection & Mitigation Security Market Size by Application
Table 2020-2025 Asia & Pacific DDoS Protection & Mitigation Security Key Players Revenue
Table 2020-2025 Asia & Pacific DDoS Protection & Mitigation Security Key Players Market Share
Table 2020-2030 Asia & Pacific DDoS Protection & Mitigation Security Market Size by Type
Table 2020-2030 China DDoS Protection & Mitigation Security Market Size
Table 2020-2030 India DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Japan DDoS Protection & Mitigation Security Market Size
Table 2020-2030 South Korea DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Southeast Asia DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Australia DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Europe DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Europe DDoS Protection & Mitigation Security Market Size by Application
Table 2020-2025 Europe DDoS Protection & Mitigation Security Key Players Revenue
Table 2020-2025 Europe DDoS Protection & Mitigation Security Key Players Market Share
Table 2020-2030 Europe DDoS Protection & Mitigation Security Market Size by Type
Table 2020-2030 Germany DDoS Protection & Mitigation Security Market Size
Table 2020-2030 France DDoS Protection & Mitigation Security Market Size
Table 2020-2030 United Kingdom DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Italy DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Spain DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Belgium DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Netherlands DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Austria DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Poland DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Russia DDoS Protection & Mitigation Security Market Size
Table 2020-2030 MEA DDoS Protection & Mitigation Security Market Size
Table 2020-2030 MEA DDoS Protection & Mitigation Security Market Size by Application
Table 2020-2025 MEA DDoS Protection & Mitigation Security Key Players Revenue
Table 2020-2025 MEA DDoS Protection & Mitigation Security Key Players Market Share
Table 2020-2030 MEA DDoS Protection & Mitigation Security Market Size by Type
Table 2020-2030 Egypt DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Israel DDoS Protection & Mitigation Security Market Size
Table 2020-2030 South Africa DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Gulf Cooperation Council Countries DDoS Protection & Mitigation Security Market Size
Table 2020-2030 Turkey DDoS Protection & Mitigation Security Market Size
Table 2020-2025 Global DDoS Protection & Mitigation Security Market Size by Region
Table 2020-2025 Global DDoS Protection & Mitigation Security Market Size Share by Region
Table 2020-2025 Global DDoS Protection & Mitigation Security Market Size by Application
Table 2020-2025 Global DDoS Protection & Mitigation Security Market Share by Application
Table 2020-2025 Global DDoS Protection & Mitigation Security Key Vendors Revenue
Table 2020-2025 Global DDoS Protection & Mitigation Security Key Vendors Market Share
Table 2020-2025 Global DDoS Protection & Mitigation Security Market Size by Type
Table 2020-2025 Global DDoS Protection & Mitigation Security Market Share by Type
Table 2025-2030 Global DDoS Protection & Mitigation Security Market Size by Region
Table 2025-2030 Global DDoS Protection & Mitigation Security Market Size Share by Region
Table 2025-2030 Global DDoS Protection & Mitigation Security Market Size by Application
Table 2025-2030 Global DDoS Protection & Mitigation Security Market Share by Application
Table 2025-2030 Global DDoS Protection & Mitigation Security Key Vendors Revenue
Table 2025-2030 Global DDoS Protection & Mitigation Security Key Vendors Market Share
Table 2025-2030 Global DDoS Protection & Mitigation Security Market Size by Type
Table 2025-2030 DDoS Protection & Mitigation Security Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure DDoS Protection & Mitigation Security Picture
Figure 2020-2030 North America DDoS Protection & Mitigation Security Market Size and CAGR
Figure 2020-2030 South America DDoS Protection & Mitigation Security Market Size and CAGR
Figure 2020-2030 Asia & Pacific DDoS Protection & Mitigation Security Market Size and CAGR
Figure 2020-2030 Europe DDoS Protection & Mitigation Security Market Size and CAGR
Figure 2020-2030 MEA DDoS Protection & Mitigation Security Market Size and CAGR
Figure 2020-2025 Global DDoS Protection & Mitigation Security Market Size and Growth Rate
Figure 2025-2030 Global DDoS Protection & Mitigation Security Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
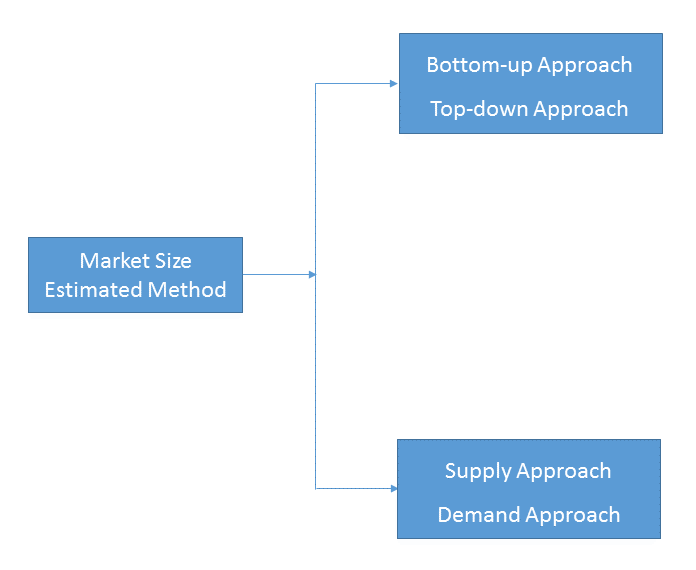
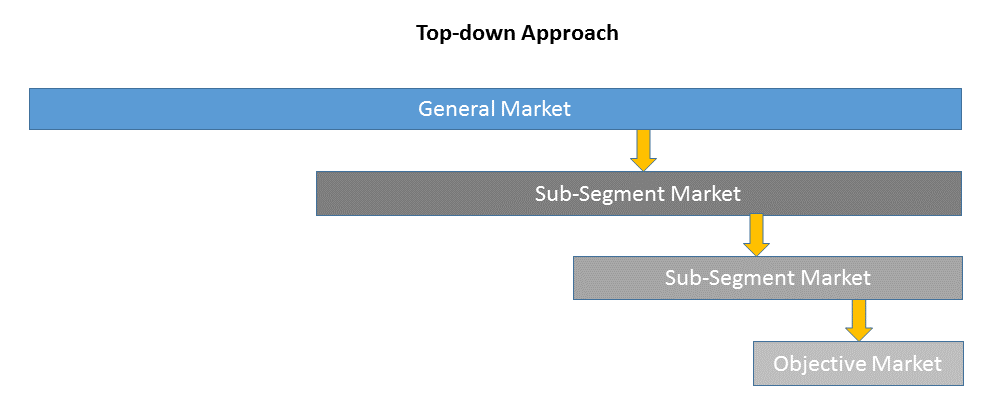
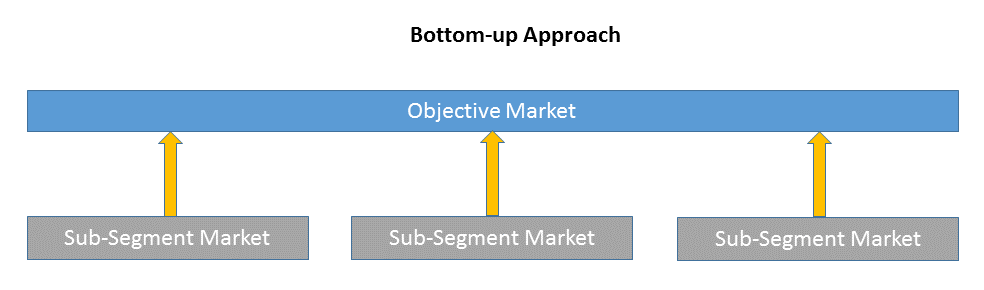
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
Bottom-up approach size the objective market by collecting the sub-segment information.
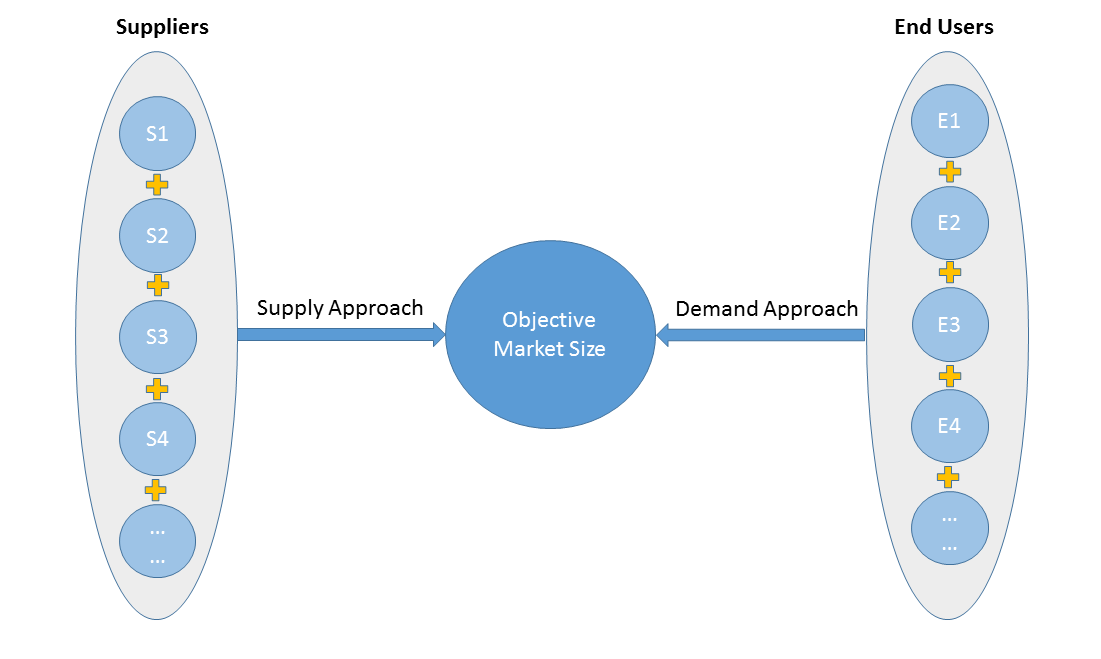
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
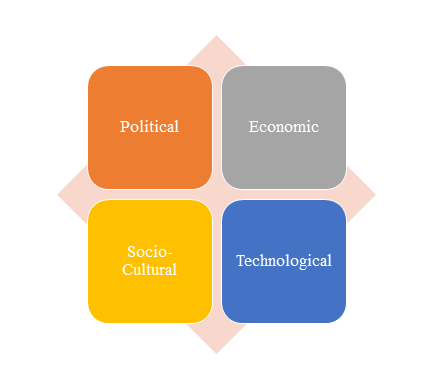
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
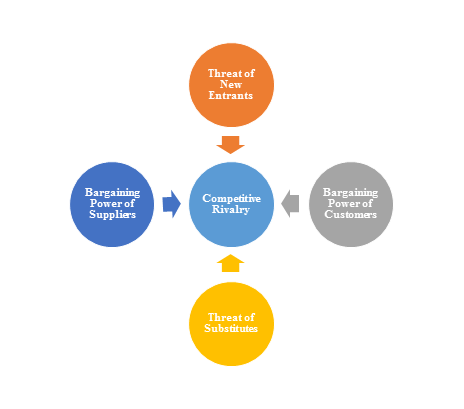
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
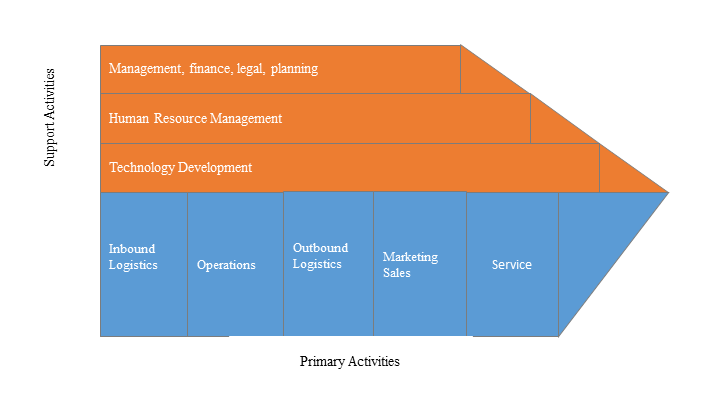
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
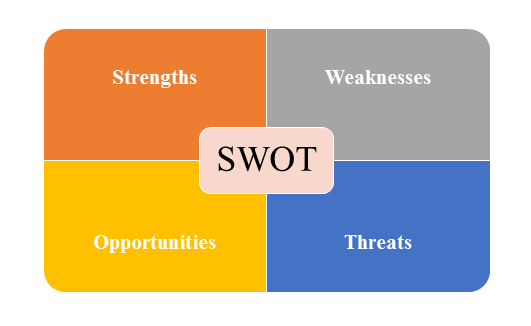
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |