Managed Detection and Response Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
Managed Detection and Response (MDR) refers to outsourced security services that provide 24/7 threat monitoring, proactive threat hunting, deep investigation of security alerts, and rapid, guided response capabilities. Unlike traditional managed security services (MSS) which primarily focus on basic monitoring and alerting, MDR is defined by its active, human-led approach to security operations. It fundamentally addresses the persistent cybersecurity challenges of talent scarcity and alert fatigue, offering organizations a turnkey solution for advanced threat defense.
The industry is defined by three critical characteristics: 24/7 Human-Led Expertise, Platform Agnosticism, and Outcomes-Based Security. Firstly, the core value of MDR lies in its 24/7 Human-Led Expertise; it pairs sophisticated technology (Endpoint Detection and Response, Network Monitoring, etc.) with elite security analysts who triage alerts, hunt for subtle threats, and validate incidents, moving beyond simple automation. Secondly, many leading MDR providers strive for Platform Agnosticism, meaning their services can integrate with a customer’s existing security infrastructure (e.g., firewall, EDR tools, cloud logs), maximizing return on existing security investments. Finally, the market is shifting toward Outcomes-Based Security, where performance is measured not by the volume of alerts generated, but by the speed of threat containment and successful remediation, providing measurable risk reduction.
The global market size for Managed Detection and Response services, including subscription fees for continuous monitoring, threat hunting, and incident response retainers, is estimated to fall within the range of USD 3.0 billion and USD 8.0 billion by 2025. This valuation reflects the rapid enterprise realization that in-house security operations centers (SOCs) are often prohibitively expensive and difficult to staff 24/7. Driven by the unrelenting sophistication of ransomware and supply chain attacks, the dramatic shift to remote work and cloud infrastructure, and the massive global shortage of cybersecurity talent, the market is projected to expand at an exceptional Compound Annual Growth Rate (CAGR) of approximately 15.0% to 30.0% through 2030, marking it as one of the fastest-growing segments within the cybersecurity industry.
Segment Analysis: By Security Type and Application
The market is segmented based on the security telemetry source being monitored (Security Type) and the primary end-user business sector (Application).
By Security Type
Managed Endpoint Detection and Response (MEDR)
MEDR is the largest and most foundational segment, projected for the highest growth, estimated at a CAGR in the range of 18.0%–33.0%. MEDR focuses on continuous monitoring and analysis of data originating from endpoints (laptops, servers, mobile devices) using underlying Endpoint Detection and Response (EDR) technology. Its primary function is to detect malicious activity, lateral movement, and unauthorized access attempts right at the user level, which remains the most common initial point of compromise. Providers like CrowdStrike Holdings, Cybereason Inc., and Deep Instinct have strong capabilities in this area, often pairing their proprietary EDR solutions with managed services.
Managed Network Detection and Response (MNDR)
MNDR focuses on analyzing network traffic metadata (North-South and East-West) to detect suspicious patterns, command-and-control (C2) communications, and policy violations that might be missed by endpoint tools. MNDR provides valuable context on attacker activities post-compromise. While sometimes considered a more specialized segment than MEDR, it is projected for robust growth, estimated at a CAGR in the range of 14.0%–29.0%, as organizations seek deeper visibility into internal network segments and East-West lateral movement.
Cloud Detection and Response (CDR)
This is the fastest-evolving segment, projected for the highest growth, estimated at a CAGR in the range of 20.0%–35.0%. CDR focuses on monitoring and analyzing data from cloud environments, including IaaS logs (AWS, Azure, GCP), SaaS platforms (Microsoft 365, Salesforce), and container activity. As enterprise data and workloads rapidly migrate to the cloud, the need for 24/7 specialized monitoring of often-complex cloud identity and access management (IAM) and configuration flaws is becoming mandatory. This area is seeing high integration efforts from companies like Mandiant (Google) and Palo Alto Networks.
Others
This segment includes specialized services focused on specific areas like Industrial Control Systems (ICS/OT), Identity Threat Detection and Response (ITDR), or Managed Application Security. As the attack surface expands into operational technology and identity layers, these niche services are projected for steady growth, estimated at a CAGR in the range of 12.0%–27.0%.
By Application (End-Use Industry)
BFSI (Banking, Financial Services, and Insurance)
BFSI is the largest revenue segment and is projected for strong growth, estimated at a CAGR in the range of 16.0%–31.0%. This sector faces the highest regulatory scrutiny (e.g., critical infrastructure designation) and is the most frequent target of sophisticated, financially motivated cybercrime. MDR is essential for maintaining continuous compliance, protecting high-value assets, and ensuring the continuity of transactional services.
IT & Telecom
This sector is the primary target for supply chain attacks and intellectual property theft, making MDR a core operational requirement. Telecommunications infrastructure must maintain constant uptime and security. The segment is projected for robust growth, estimated at a CAGR in the range of 15.0%–30.0%, driven by the need to secure complex 5G networks and proprietary source code.
Healthcare
The Healthcare sector is a rapidly growing target due to the high value of patient data (ePHI) and the critical nature of its operations. Ransomware attacks against hospitals and clinical networks are highly disruptive. MDR adoption is accelerating as organizations seek to comply with privacy laws (e.g., HIPAA) and ensure patient safety. This segment is projected for high growth, estimated at a CAGR in the range of 17.0%–32.0%.
Manufacturing
MDR adoption in Manufacturing is being driven by the convergence of IT and Operational Technology (OT/ICS). Securing proprietary designs, managing complex supply chains, and preventing disruption to production lines are key priorities. This segment is projected for significant growth, estimated at a CAGR in the range of 14.0%–29.0%.
Government & Defense
This sector requires the highest levels of security against nation-state actors and espionage. MDR services provide dedicated, high-clearance teams for threat hunting and incident response, often supplementing highly complex in-house SOCs. This segment is projected for steady growth, estimated at a CAGR in the range of 13.0%–28.0%.
Retail and Others
The Retail sector, especially e-commerce, requires MDR to protect payment systems (PCI DSS compliance) and manage vast amounts of customer data. The "Others" category includes sectors like education, utilities, and energy, all experiencing increased digitalization and subsequent demand for managed defense. These segments are projected for moderate to strong growth, estimated at a CAGR in the range of 13.0%–28.0%.
Regional Market Trends
Regional adoption is highly correlated with the maturity of the cybersecurity landscape, regulatory mandates, and local labor costs for security professionals.
North America (NA)
North America is the largest and most mature market, projected to achieve a strong growth rate, estimated at a CAGR in the range of 16.0%–31.0%. The US is the global epicenter of technology vendors and venture capital, fostering aggressive innovation in MDR tools. High labor costs for in-house security analysts make the outsourced MDR model financially compelling. The presence of major players like Rapid7 Inc., Secureworks Corp., CrowdStrike Holdings, and Mandiant (Google) ensures continued rapid adoption.
Asia-Pacific (APAC)
APAC is the fastest-growing region, projected to achieve a robust growth rate, estimated at a CAGR in the range of 18.0%–33.0%. Growth is driven by accelerating digital transformation, increasing geopolitical tensions leading to state-sponsored attacks, and the adoption of modern regulatory frameworks (e.g., in Singapore, Australia, and India). Organizations in APAC often leapfrog traditional MSSPs directly to modern MDR solutions due to the high concentration of IT services and financial institutions.
Europe
Europe is a highly active market, projected to experience a solid growth rate, estimated at a CAGR in the range of 15.0%–30.0%. Adoption is strongly influenced by the GDPR and other stringent data privacy regulations, which mandate demonstrable compliance and rapid breach response capabilities. The market is competitive, featuring strong regional players like Sophos Ltd. and a mix of global vendors.
Latin America (LatAm)
The LatAm market is accelerating its adoption of MDR, projected to grow at a CAGR in the range of 14.0%–29.0%. Growth is tied to the rapid expansion of FinTech and e-commerce, which are frequently targeted by ransomware groups. MDR offers a cost-effective alternative to building highly specialized regional SOCs.
Middle East and Africa (MEA)
MEA is a high-potential, investment-driven market, projected to achieve a CAGR in the range of 13.0%–28.0%. Growth is localized around financial hubs (UAE, Saudi Arabia) and driven by massive government investments in digitalization and cybersecurity infrastructure to protect critical national assets, creating demand for premium, highly certified MDR services.
Company Landscape: Platform Giants, Pure-Plays, and Network Specialists
The MDR market is fragmented, combining large security platform providers that offer MDR as a service, and pure-play specialists that excel in specific operational models.
Security Platform Giants and Network Specialists: Companies like Palo Alto Networks, Trend Micro Inc., and Sophos Ltd. leverage their existing, widely deployed proprietary security platforms (firewalls, EDR) to offer MDR services. This model provides highly integrated, high-fidelity data feeds and control over the entire security stack. IBM Corporation and Trustwave Holdings offer extensive global managed security services, with MDR forming the premium, high-value component of their portfolios.
EDR/XDR and Pure-Play MDR: CrowdStrike Holdings, Mandiant (Google), and Cybereason Inc. are strong in the MEDR/XDR space, offering their own EDR telemetry paired with expert security analysis. Rapid7 Inc. is a leader that combines its vulnerability management and security analytics heritage with a strong MDR offering.
Specialized and Cloud-Native MDR: Arctic Wolf Networks, eSentire Inc., Red Canary Inc., and Expel Inc. often represent the pure-play, platform-agnostic MDR specialists. Their focus is solely on the human-led detection and response function, often integrating with a wide variety of third-party tools (Microsoft, CrowdStrike, etc.) to deliver an integrated service layer, making them highly attractive to organizations with heterogeneous security environments. Deep Instinct specializes in prevention and leverages deep learning to enhance the early detection capabilities that feed into MDR processes.
Industry Value Chain Analysis
The MDR value chain transforms vast, noisy security data into decisive, rapid action, requiring seamless integration of technology and human expertise.
1. Telemetry Sourcing and Ingestion (Upstream):
The chain begins with sourcing and integrating security telemetry from endpoints (MEDR), networks (MNDR), cloud environments (CDR), and other security tools. Value is created by the MDR provider's ability to efficiently normalize and ingest massive volumes of data from diverse, customer-owned platforms (platform agnosticism) or proprietary agents.
2. Threat Detection and Hunting (Core Technology):
Value is created by the technology layer that processes the ingested data. This involves automated detection (using rules, signatures, and AI/ML algorithms) and, crucially, proactive Threat Hunting—where human analysts use data science and threat intelligence to search for subtle, unflagged adversarial techniques that bypass automated systems.
3. Validation, Triage, and Containment (Human Expertise):
This is the highest-value stage. Human security analysts investigate and validate potential threats, eliminating false positives and confirming true positives. Once validated, the MDR service rapidly initiates containment actions (e.g., isolating an endpoint, blocking a malicious IP), providing the immediate response capability that defines the service.
4. Remediation and Strategic Reporting (Downstream):
The final stage involves providing the client with detailed reports, forensics, and step-by-step guidance for full system remediation and recovery. Value is delivered through actionable strategic advice on improving security posture, hardening defenses, and minimizing future risk, effectively closing the security loop.
Opportunities and Challenges
The MDR market is positioned to capitalize on systemic security gaps but must overcome challenges related to data volume and skills integration.
Opportunities
Convergence to eXtended Detection and Response (XDR): The single biggest opportunity is the shift from siloed MDR (MEDR, MNDR, CDR) to unified XDR platforms. By integrating data from all security sources (endpoint, network, cloud, email, identity), providers can offer a more holistic and context-rich view of an entire attack chain, enhancing detection accuracy and speed of response.
Small and Medium Enterprise (SME) Market Penetration: While historically focused on large enterprises, the MDR model is perfectly suited for resource-constrained SMEs that cannot afford dedicated, 24/7 SOC staff. Offering tiered, cost-effective MDR services to the SME sector represents a vast, untapped market for growth.
AI-Powered Response Automation (AR): As threats accelerate, the integration of AI to automate response actions (e.g., automatic blocking, suspension of user accounts) without human intervention offers a path to near-instantaneous containment, dramatically improving mean time to respond (MTTR).
Threat Intelligence Sharing and Global Visibility: MDR providers, by observing attacks across hundreds or thousands of clients, generate unique, high-fidelity threat intelligence. Monetizing and leveraging this collective intelligence to provide preemptive defense across their entire client base is a key competitive differentiator and growth driver.
Challenges
Data Overload and Integration Complexity: The exponential volume of telemetry generated by modern cloud and distributed environments can overwhelm even automated systems, increasing complexity and cost for MDR providers. Integrating MDR platforms with a client's disparate existing security tools (firewalls, identity) often creates complex, high-friction deployment projects.
Maintaining High-Quality Analyst Talent: The core value of MDR is human expertise, but the global shortage of skilled cybersecurity analysts is acute. MDR providers face the continuous challenge of recruiting, training, and retaining elite, 24/7 staff necessary to deliver on the promise of human-led threat hunting and rapid response.
Service Standardization vs. Customization: While scalability requires standardized service delivery, highly complex enterprises often demand deep customization and integration with unique business processes. Balancing the need for efficient standardization (to maintain profit margins) with the requirement for flexible customization is a persistent market challenge.
Regulatory and Geographical Compliance: Delivering MDR across diverse geographies means complying with varying regulations regarding data residency, data access, and incident reporting (e.g., GDPR, local critical infrastructure laws). This forces providers to maintain dedicated regional SOCs and data processing capabilities, adding significant operational overhead.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Managed Detection and Response Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Managed Detection and Response Market in North America (2020-2030)
8.1 Managed Detection and Response Market Size
8.2 Managed Detection and Response Market by End Use
8.3 Competition by Players/Suppliers
8.4 Managed Detection and Response Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Managed Detection and Response Market in South America (2020-2030)
9.1 Managed Detection and Response Market Size
9.2 Managed Detection and Response Market by End Use
9.3 Competition by Players/Suppliers
9.4 Managed Detection and Response Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Managed Detection and Response Market in Asia & Pacific (2020-2030)
10.1 Managed Detection and Response Market Size
10.2 Managed Detection and Response Market by End Use
10.3 Competition by Players/Suppliers
10.4 Managed Detection and Response Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Managed Detection and Response Market in Europe (2020-2030)
11.1 Managed Detection and Response Market Size
11.2 Managed Detection and Response Market by End Use
11.3 Competition by Players/Suppliers
11.4 Managed Detection and Response Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Managed Detection and Response Market in MEA (2020-2030)
12.1 Managed Detection and Response Market Size
12.2 Managed Detection and Response Market by End Use
12.3 Competition by Players/Suppliers
12.4 Managed Detection and Response Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Managed Detection and Response Market (2020-2025)
13.1 Managed Detection and Response Market Size
13.2 Managed Detection and Response Market by End Use
13.3 Competition by Players/Suppliers
13.4 Managed Detection and Response Market Size by Type
Chapter 14 Global Managed Detection and Response Market Forecast (2025-2030)
14.1 Managed Detection and Response Market Size Forecast
14.2 Managed Detection and Response Application Forecast
14.3 Competition by Players/Suppliers
14.4 Managed Detection and Response Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Palo Alto Networks
15.1.1 Company Profile
15.1.2 Main Business and Managed Detection and Response Information
15.1.3 SWOT Analysis of Palo Alto Networks
15.1.4 Palo Alto Networks Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 Rapid7 Inc.
15.2.1 Company Profile
15.2.2 Main Business and Managed Detection and Response Information
15.2.3 SWOT Analysis of Rapid7 Inc.
15.2.4 Rapid7 Inc. Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 Secureworks Corp.
15.3.1 Company Profile
15.3.2 Main Business and Managed Detection and Response Information
15.3.3 SWOT Analysis of Secureworks Corp.
15.3.4 Secureworks Corp. Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 IBM Corporation
15.4.1 Company Profile
15.4.2 Main Business and Managed Detection and Response Information
15.4.3 SWOT Analysis of IBM Corporation
15.4.4 IBM Corporation Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 Mandiant (Google)
15.5.1 Company Profile
15.5.2 Main Business and Managed Detection and Response Information
15.5.3 SWOT Analysis of Mandiant (Google)
15.5.4 Mandiant (Google) Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 CrowdStrike Holdings
15.6.1 Company Profile
15.6.2 Main Business and Managed Detection and Response Information
15.6.3 SWOT Analysis of CrowdStrike Holdings
15.6.4 CrowdStrike Holdings Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.7 Trend Micro Inc.
15.7.1 Company Profile
15.7.2 Main Business and Managed Detection and Response Information
15.7.3 SWOT Analysis of Trend Micro Inc.
15.7.4 Trend Micro Inc. Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.8 Sophos Ltd.
15.8.1 Company Profile
15.8.2 Main Business and Managed Detection and Response Information
15.8.3 SWOT Analysis of Sophos Ltd.
15.8.4 Sophos Ltd. Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.9 Cybereason Inc.
15.9.1 Company Profile
15.9.2 Main Business and Managed Detection and Response Information
15.9.3 SWOT Analysis of Cybereason Inc.
15.9.4 Cybereason Inc. Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
15.10 Deep Instinct
15.10.1 Company Profile
15.10.2 Main Business and Managed Detection and Response Information
15.10.3 SWOT Analysis of Deep Instinct
15.10.4 Deep Instinct Managed Detection and Response Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of Managed Detection and Response Report
Table Data Sources of Managed Detection and Response Report
Table Major Assumptions of Managed Detection and Response Report
Table Managed Detection and Response Classification
Table Managed Detection and Response Applications
Table Drivers of Managed Detection and Response Market
Table Restraints of Managed Detection and Response Market
Table Opportunities of Managed Detection and Response Market
Table Threats of Managed Detection and Response Market
Table Raw Materials Suppliers
Table Different Production Methods of Managed Detection and Response
Table Cost Structure Analysis of Managed Detection and Response
Table Key End Users
Table Latest News of Managed Detection and Response Market
Table Merger and Acquisition
Table Planned/Future Project of Managed Detection and Response Market
Table Policy of Managed Detection and Response Market
Table 2020-2030 North America Managed Detection and Response Market Size
Table 2020-2030 North America Managed Detection and Response Market Size by Application
Table 2020-2025 North America Managed Detection and Response Key Players Revenue
Table 2020-2025 North America Managed Detection and Response Key Players Market Share
Table 2020-2030 North America Managed Detection and Response Market Size by Type
Table 2020-2030 United States Managed Detection and Response Market Size
Table 2020-2030 Canada Managed Detection and Response Market Size
Table 2020-2030 Mexico Managed Detection and Response Market Size
Table 2020-2030 South America Managed Detection and Response Market Size
Table 2020-2030 South America Managed Detection and Response Market Size by Application
Table 2020-2025 South America Managed Detection and Response Key Players Revenue
Table 2020-2025 South America Managed Detection and Response Key Players Market Share
Table 2020-2030 South America Managed Detection and Response Market Size by Type
Table 2020-2030 Brazil Managed Detection and Response Market Size
Table 2020-2030 Argentina Managed Detection and Response Market Size
Table 2020-2030 Chile Managed Detection and Response Market Size
Table 2020-2030 Peru Managed Detection and Response Market Size
Table 2020-2030 Asia & Pacific Managed Detection and Response Market Size
Table 2020-2030 Asia & Pacific Managed Detection and Response Market Size by Application
Table 2020-2025 Asia & Pacific Managed Detection and Response Key Players Revenue
Table 2020-2025 Asia & Pacific Managed Detection and Response Key Players Market Share
Table 2020-2030 Asia & Pacific Managed Detection and Response Market Size by Type
Table 2020-2030 China Managed Detection and Response Market Size
Table 2020-2030 India Managed Detection and Response Market Size
Table 2020-2030 Japan Managed Detection and Response Market Size
Table 2020-2030 South Korea Managed Detection and Response Market Size
Table 2020-2030 Southeast Asia Managed Detection and Response Market Size
Table 2020-2030 Australia Managed Detection and Response Market Size
Table 2020-2030 Europe Managed Detection and Response Market Size
Table 2020-2030 Europe Managed Detection and Response Market Size by Application
Table 2020-2025 Europe Managed Detection and Response Key Players Revenue
Table 2020-2025 Europe Managed Detection and Response Key Players Market Share
Table 2020-2030 Europe Managed Detection and Response Market Size by Type
Table 2020-2030 Germany Managed Detection and Response Market Size
Table 2020-2030 France Managed Detection and Response Market Size
Table 2020-2030 United Kingdom Managed Detection and Response Market Size
Table 2020-2030 Italy Managed Detection and Response Market Size
Table 2020-2030 Spain Managed Detection and Response Market Size
Table 2020-2030 Belgium Managed Detection and Response Market Size
Table 2020-2030 Netherlands Managed Detection and Response Market Size
Table 2020-2030 Austria Managed Detection and Response Market Size
Table 2020-2030 Poland Managed Detection and Response Market Size
Table 2020-2030 Russia Managed Detection and Response Market Size
Table 2020-2030 MEA Managed Detection and Response Market Size
Table 2020-2030 MEA Managed Detection and Response Market Size by Application
Table 2020-2025 MEA Managed Detection and Response Key Players Revenue
Table 2020-2025 MEA Managed Detection and Response Key Players Market Share
Table 2020-2030 MEA Managed Detection and Response Market Size by Type
Table 2020-2030 Egypt Managed Detection and Response Market Size
Table 2020-2030 Israel Managed Detection and Response Market Size
Table 2020-2030 South Africa Managed Detection and Response Market Size
Table 2020-2030 Gulf Cooperation Council Countries Managed Detection and Response Market Size
Table 2020-2030 Turkey Managed Detection and Response Market Size
Table 2020-2025 Global Managed Detection and Response Market Size by Region
Table 2020-2025 Global Managed Detection and Response Market Size Share by Region
Table 2020-2025 Global Managed Detection and Response Market Size by Application
Table 2020-2025 Global Managed Detection and Response Market Share by Application
Table 2020-2025 Global Managed Detection and Response Key Vendors Revenue
Table 2020-2025 Global Managed Detection and Response Key Vendors Market Share
Table 2020-2025 Global Managed Detection and Response Market Size by Type
Table 2020-2025 Global Managed Detection and Response Market Share by Type
Table 2025-2030 Global Managed Detection and Response Market Size by Region
Table 2025-2030 Global Managed Detection and Response Market Size Share by Region
Table 2025-2030 Global Managed Detection and Response Market Size by Application
Table 2025-2030 Global Managed Detection and Response Market Share by Application
Table 2025-2030 Global Managed Detection and Response Key Vendors Revenue
Table 2025-2030 Global Managed Detection and Response Key Vendors Market Share
Table 2025-2030 Global Managed Detection and Response Market Size by Type
Table 2025-2030 Managed Detection and Response Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Managed Detection and Response Picture
Figure 2020-2030 North America Managed Detection and Response Market Size and CAGR
Figure 2020-2030 South America Managed Detection and Response Market Size and CAGR
Figure 2020-2030 Asia & Pacific Managed Detection and Response Market Size and CAGR
Figure 2020-2030 Europe Managed Detection and Response Market Size and CAGR
Figure 2020-2030 MEA Managed Detection and Response Market Size and CAGR
Figure 2020-2025 Global Managed Detection and Response Market Size and Growth Rate
Figure 2025-2030 Global Managed Detection and Response Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
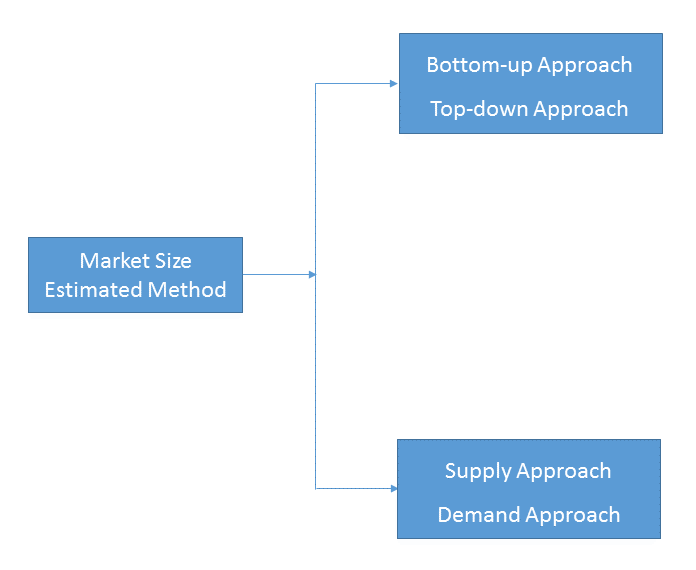
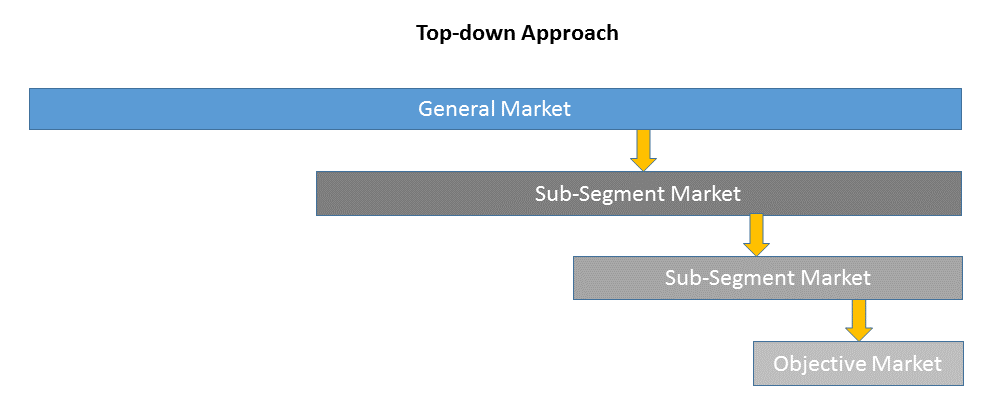
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
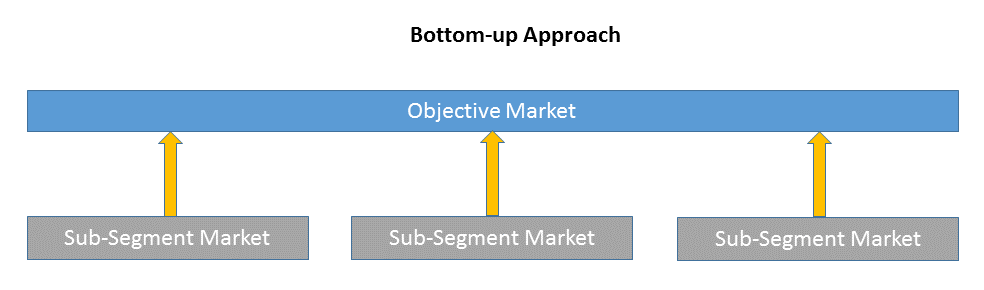
Bottom-up approach size the objective market by collecting the sub-segment information.
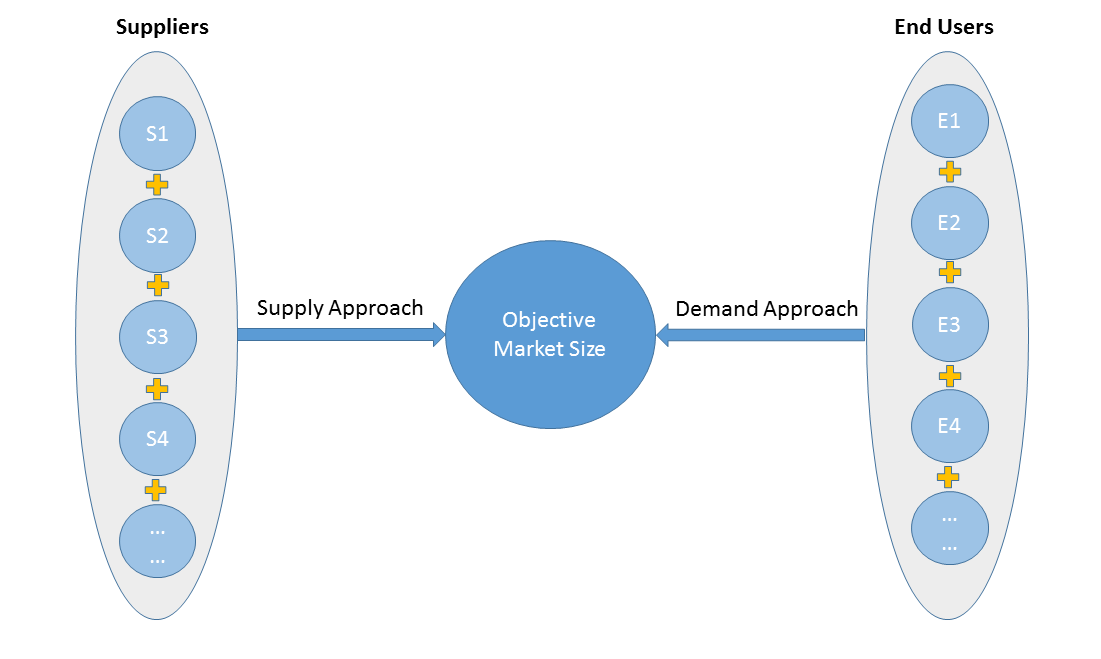
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
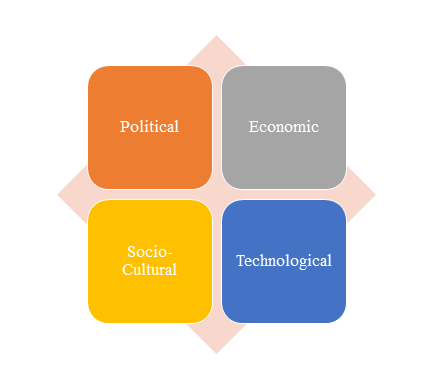
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
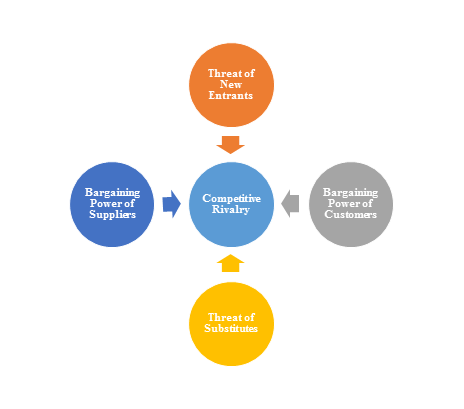
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
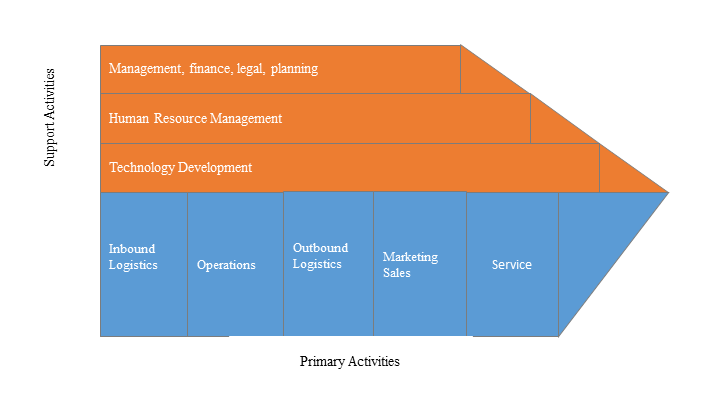
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
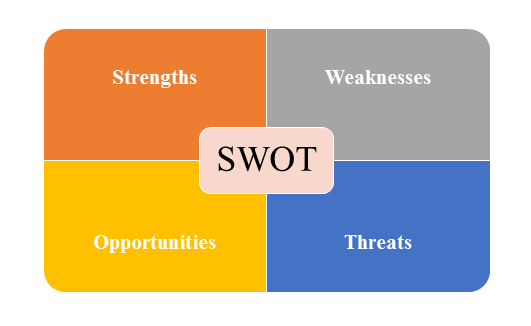
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |