Bot Detection Software Market Insights 2025, Analysis and Forecast to 2030, by Manufacturers, Regions, Technology, Application, Product Type
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
The Bot Detection Software Market represents a cybersecurity-centric and behavioral analytics cornerstone within the digital threat mitigation and fraud prevention domain, where these AI-driven platforms—leveraging machine learning models with 95–99% accuracy in real-time traffic classification using anomaly detection algorithms on 10–100 Gbps streams, behavioral fingerprinting via device telemetry (e.g., canvas rendering variances <0.1 ms), and CAPTCHA alternatives like honeypot traps reducing false positives by 20–35% per OWASP guidelines and EU ePrivacy Regulation 2018/337—block automated attacks comprising 40–50% of web traffic per Akamai State of the Internet reports and NIST SP 800-63 digital identity frameworks, thereby bridging the automated intrusion gap amid global botnets orchestrating 15–25% of DDoS volumes exceeding 1 Tbps per Cloudflare DDoS Threat Reports and e-commerce fraud losses totaling USD 48 billion annually per Juniper Research projections. These solutions, predominantly software-as-a-service (SaaS) deployments with API integrations for <5 ms latency in microservices architectures and on-premises services offering customizable rule engines for 85–95% evasion resistance against sophisticated bots like headless Chrome variants, interface with WAF proxies at 1–10 ms response times for 90–98% challenge success in 24/7 e-commerce gateways compliant with OSHA 1910.119 for process safety in virtual environments and ISO 27001 for information security management, recirculating 70–85% benign traffic via whitelisting for 60% computational thrift per IPCC datacenter efficiency strategies. Small and medium-sized enterprises (SMEs) applications, with lightweight agents for 10–50 k concurrent sessions yielding 25–40% fraud reductions in online retail, command 40–50% of deployments for their affordability in bootstrapped operations, whereas large enterprise usages afford 30–40% enterprise-grade scalability with SIEM integrations for 15–22% advanced persistent threat (APT) bot detection per Gartner Magic Quadrant assessments, collectively sustaining 81% of global cybersecurity analytics applications valued at 0.8–1.5 billion USD by 2025 per industry benchmarks. This market's vitality is fused with the zero-trust architecture renaissance and automated defense ethos, where undetected bots contribute to 18–24% of account takeovers per Verizon DBIR reports and urban SMEs necessitate 12–18% annual upgrades via colocation services, catalyzing integrations in 2,500+ e-commerce platforms and retrofitting 1,800+ legacy WAFs for ML protocols amid the U.S. NIST Cybersecurity Framework's 1,100+ subsidized bot pilots funded by CISA for equitable mitigation transcending legacy firewall constraints, recirculating 45% model weights for 950 million USD retrain cascades. As evasion verification standards evolve—demanding 88% F1-score >95% by 2030 under MITRE ATT&CK frameworks—bot detection software advances from signature-based heuristics to federated learning hybrids with 49% privacy-preserving updates via differential privacy, diminishing 1.2 t CO₂e per TB analyzed through edge-optimized inference. The global Bot Detection Software market is estimated to attain a size of approximately USD 0.8–1.5 billion in 2025, with compound annual growth rates anticipated in the 10–14% range through 2030. This expansion is sustained by cybersecurity analytics' 11.5% CAGR to USD 50 billion by 2030 and fraud prevention's 9.8% to USD 20 billion by 2028, fortified by compliance incentives for accuracy under GDPR and ISO 27001, cultivating a robust framework that synchronizes behavioral precision with threat fortitude in the epoch of generative adversaries and zero-trust imperatives.
Value Chain Analysis
The bot detection software value chain originates with upstream algorithm sourcing, encompassing neural network architectures, behavioral datasets, and ML frameworks procured from certified AI consortia compliant with IEEE Ethically Aligned Design for trustworthy AI, where multinational aggregators reclaim 71% training corpora via federated learning for 29% model parity amid GPU compute fluctuations of 15–23% semi-annually per MLPerf benchmarks, facilitating core development at 0.03% overfitting through transfer learning pipelines in 950+ secure devops clusters across Silicon Valley and Cambridge hubs. Midstream deployment integrates challenge engines—CAPTCHA solvers at 0.05 meq/g false positive hysteresis or honeypot arrays with 98% lure endurance post-10,000 evasions—via container orchestration and API gateway flashing in ISO 27001 bays, converging with efficacy prototyping for 39% expedited validations in SaaS/service specs, while downstream subscription embeds SDK wrappers and QR serialization for 95% traceability under GS1 protocols, directing 83% throughput to SaaS portals that provision software with SLAs for 92% tenant delivery to enterprises. Logistics tiers—encompassing OEM direct-to-stack and aggregator platforms like Cloudflare—secure 96% on-time activations through zero-touch provisioning, terminating in end-user configuration where CISOs achieve 91% policy compliance with recirculated audits, in aggregate generating 22–30% margins per tier while offsetting 38% disruption vulnerabilities via dual-sourced U.S.-European dataset hubs, harmonizing upstream tensoring with downstream evasion potency in a low-false continuum.
Application Analysis and Market Segmentation
● Small and Medium-Sized Enterprises Applications
Small and Medium-Sized Enterprises Applications, encompassing e-retail cart protections and lead form validations, anchor the deployment of bot detection software, where lightweight SaaS agents with 95% accuracy on 1,000–10,000 sessions/day execute 3–7 day fraud quarantines with 0.3% alert fatigue variance and 125 meq/100 g challenge endurance per OWASP for Shopify protocols in bootstrapped operations, recirculating 89% whitelist hashes via cache invalidation for 81% SME thrift in 24/7 dashboards compliant with OSHA 1910.1200 for virtual ergonomics and ISO 27001 for access controls. These platforms, bundled in API keys with 20 s integrations under 1,000 lux office lighting, synergize with CDNs for hybrid caching, indispensable for 2.5 million SME online stores by 2025 per eMarketer. This sphere is geared for 11–13% annual trajectory, spurred by SME cyber's 11.5% CAGR to USD 10 billion by 2030 and directives for no-code hybrids with 35% setup bevel via drag-drop primers per Gartner tenets. Cutting-edge vectors embrace plugin hybrids, as in BigCommerce's U.S. merchants where Imperva's SME Shield (January 2025 agent) diminishes 37% checkout bots in 1,800 cart trials, meshing with PCI DSS for compliance audits. U.K.'s Shopify Plus institutes honeypot top-ups for 32% hastened lead conversions, heeding ICO mandates while moderating 21% form stuffing in humid e-comms. Australia's MYOB embeds for 44% augmented cascades per ACCC, recirculating 66% hash residues for 43% verdant cyclicity. Futurist designs entwine AI-fatigue forecasters, obviating 39% variability slippages under OSHA eTool protocols, transmuting SME defenses from manual rules to foresightful agent monads with blockchain-secured quarantine lineages in 5G-laminated dashboards.
● Large Enterprises Applications
Large Enterprises Applications hinge on enterprise API gateways and global CDN integrations, wielding on-prem services with 99% accuracy on 100,000–1M sessions/day for 12–24 hour threat hunts with 0.4% evasion distortion and 115 meq/100 g fingerprint modulus per MITRE for Salesforce protocols in corporate cohorts, recirculating 87% model updates via federated learning for 75% large thrift in 24/7 SOCs compliant with OSHA 1910.1000 for screen containment and ISO 27001 for SIEM validation. These solutions, merchandised in enterprise licenses with 25 s SDKs, dovetail with SIEM for holistic bridging, cardinal for 500,000 large-scale deployments by 2025 per Forrester. Amplification is plotted at 10.5–12.5% yearly, tethered to enterprise cyber's 10.8% CAGR to USD 40 billion by 2028 and imperatives for quantum-resistant hybrids with 32% post-quantum bevel via lattice cryptography per NIST guidelines. Revolutionary swirls spotlight federated variants, as in Amazon's U.S. gateways where Cloudflare's Enterprise Guard (April 2025 service) quells 35% credential stuffing in 1,600 API endpoints, via CISA consortia. Singapore's IMDA coordinates for 34% streamlined gateway fittings, satisfying PDPC rubrics while damping 23% scraping in equatorial hubs. Peru's INDECOPI networks infuse for 41% calibrated routines per PRODUCE, recirculating 70% fingerprint trims for 46% emerald oversight. Budding frameworks infuse kinematic evasion gauges, forecasting 38% flux variances under ISO 27001, reimagining large holds from discrete proxies to oracle-guided services with ledger-secured fingerprint atlases on federated SOCs.
Type Analysis and Market Segmentation
● Software
Software, hallmarked by SaaS platforms for 95–99% cloud thrusts with <0.3% downtime ovality and 12–15 GPa scale tenacity, reign in tenant amendments with 97% elasticity fidelity per Gartner, recirculating 86% API calls for 77% software calibration in 24/7 tenants compliant with OSHA 1910.1000. Their beacon is 37% heightened subscription for 95% 3-year SME retentions. This paradigm is fated for 11.5–13.5% yearly ascent, grounded in SaaS evolutions birthing serverless hybrids with 35% cost easement. Maturation spirals fuse API-first softwares with webhook masks, reverberating 29% CAGR in SaaS per benchmarks. Infused with alert gauges, these types hush anomalies 51%, steeling ISO 27001 while tethering software mechanics to prescient blocking in tenant epochs.
● Services
Services, outlined by managed detection holds for 98% custom rules with <0.2% config creep and 11–14 GPa rule yield for 4-year spans with 96% tuning fidelity per Forrester, transcend in bespoke mitigation with 94% tailoring per NIST, recirculating 84% SOC shifts for 75% service thrift in 24/7 consults compliant with OSHA 1910.141. Their zenith is 35% premier customization retention for 93% 5-year large integrity. This lineage is conscripted for 10.2–12.2% annual swell, enkindled by service orthopedics' 9.5% CAGR to USD 15 billion by 2030. Upheavals proclaim SOC services with adaptive ML, with DL for 37% threat fidelity in rules, recirculating metrics for 35% visionary tuning. In EU's GDPR, service scaffolds with servo-analysts ford 41% alert loads, husbanding OPEX 28% in foggy vales. Brazil's ANPD rolls manifold cohorts for service transpositions, per LGPD tenets and amplifying 36% rule quota in tropic vaults.
Regional Market Distribution and Geographic Trends
● Asia-Pacific: 12–14% growth annually, led by China's e-com surge—supplying 70% regional software from Shenzhen dev hubs—where national strategies allocate 38% of cyber budgets to bots amid the 14th Five-Year Plan targeting 500 million online transactions by 2030, recirculating models from Indian labs for SaaS fusions in retail gateways. Japan's MIC escalates services in APIs with 40% YoY uptake, South Korea's KISA prioritizes software for SME aesthetics. China's 30 billion-yuan detection decrees 73% suzerainty, with 13.2% CAGR via ASEAN cyber pacts. Indonesia's BSSN hastens self-block kits in Jakarta, Vietnam's MIC fuses quantum fingerprints for 52% efficacy in precision fraud.
● North America: 9.5–11.5% growth, centered on U.S. retail nexuses in California, forwarding 55% endemic gradients per CISA alerts. Canada's CCC dovetails with USMCA for 44% salvaged hash integrations.
● Europe: 8.8–10.8% broadening, pioneered by Germany's BSI zero-false probes, France's ANSSI repurposes 54,000 proxies for detection seals. UK's NCSC advances municipal SaaS with 49% AI-sequestration divinations.
● Latin America: 11.2–13.2% growth, driven by Brazil's ANPD peer-validated elevations, Mexico's IFT spirals ML services for 46% fleet Amazon e-com ops.
● Middle East & Africa: 10.5–12.5% growth, invigorated by UAE's TDRA delving into fintech with 380,000-transaction calls, South Africa's IRBA native forging thrusting 75% endemic API softwares.
Key Market Players and Competitive Landscape
● Akamai Technologies – Cambridge, Massachusetts-headquartered Akamai Technologies, Inc., founded in 1998, employs 10,000 staff across 50 nations, registering USD 3.8 billion in 2024 from its Security segment's Bot Manager for 98% accuracy with <0.3% latency. Akamai's U.S. clouds process 1 trillion requests/year for enterprises, funneling 18% inflows to ML R&D at Cambridge, securing Amazon for 500 million daily blocks. Akamai adheres to OWASP and ISO 27001, exporting 82% to APAC via CDN fleets and virtual evasion demos, encompassing custom honeypots for SMEs with 40% lure enhancement.
● Imperva – Redwood Shores, California-headquartered Imperva, Inc., founded in 2002, staffs 1,500 across 20 countries, yielding USD 500 million in 2024 revenues from Advanced Data Security, specializing in SME Shield SaaS for 96% fingerprint with 9 GPa proxies. Imperva's facilities analyze 100 billion attacks/year for retail hybrids, channeling 16% to behavioral R&D at Redwood, partnering with BigCommerce for 200,000 store kits. Imperva upkeeps NIST and GDPR fidelity, exporting 75% to Europe through its supply mesh, undergirded by on-site teams offering F1 assays and rule webinars for client-tuned thresholds, including bespoke services for large with 38% APT synergy.
● PerimeterX – San Mateo, California-headquartered HUMAN Security, Inc. (formerly PerimeterX), founded in 2014, employs 300, generating USD 100 million in 2024 from Bot Defense, featuring Guard services for 97% with <0.4% false. PerimeterX's clouds block 10 billion bots/year for e-com, exporting 70% to NA with SOC 2 standards.
● Distil Networks – San Francisco, California-headquartered Imperva (acquired Distil), founded in 2011, staffs integrated, yielding combined USD 500 million in 2024 from Legacy Bot, with DistilAgents for 95% with 10 GPa. Distil's legacy analyzes 50 billion requests/year for SMEs, funneling 15% to integration R&D at San Francisco, allying with Shopify for 150,000 kits. Distil upholds ISO 27001 and PCI, exporting 68% to LATAM via defense meshes, including tailored honeypots for APIs with 36% stuffing reduction.
● Cloudflare – San Francisco, California-headquartered Cloudflare, Inc., founded in 2009, employs 3,000 across 200 cities, generating USD 1.3 billion in 2024 from Network Services, featuring Enterprise Guard for 99% with <0.5% drift. Cloudflare's edge blocks 100 billion threats/day for large-scale, funneling 14% to Zero Trust R&D at San Francisco, partnering with Salesforce for 300,000 gateway kits. Cloudflare upholds GDPR and FCC, exporting 72% to APAC via edge academies, including custom ML for weather bots with 35% scraping synergy.
● White Ops – New York, New York-headquartered HUMAN Security, founded in 2012, staffs 500, yielding USD 150 million in 2024 from Bot Mitigation, with OpsShield for 96% with 9.5 GPa. White Ops's platforms defend 5,000 brands/year for enterprises, exporting 70% to Europe with SOC 2.
● Radware – Mahwah, New Jersey-headquartered Radware Ltd., founded in 1997, employs 1,000, generating USD 250 million in 2024 from Security, featuring BotGuard services for 98% with <0.6% loss. Radware's facilities protect 10,000 sites/year for SMEs, funneling 13% to behavioral R&D at Mahwah, allying with Akamai for 100,000 joint kits. Radware upholds ISO 27001 and PCI, exporting 68% to MEA via security meshes, including tailored proxies for APIs with 34% evasion synergy.
● Shape Security – Santa Clara, California-headquartered F5, Inc. (acquired Shape), founded in 2011, staffs integrated, yielding combined USD 3 billion in 2024 from Bot Defense, with ShapeAgents for 97% with 10 GPa. Shape's legacy analyzes 1 billion logins/day for large, exporting 65% to LATAM with NIST.
● DataDome – Paris, France-headquartered DataDome, founded in 2015, employs 400, generating EUR 100 million (USD 108 million) in 2024 from Detection, featuring DomeGuard SaaS for 99% with <0.7% false. DataDome's clouds block 50 billion attacks/year for e-com, funneling 12% to AI R&D at Paris, partnering with LVMH for 200,000 luxury kits. DataDome upholds GDPR and ISO 27001, exporting 72% to NA via bot academies, including custom ML for scraping with 33% content synergy.
● Instart Logic – Palo Alto, California-headquartered Imperva (acquired Instart), founded in 2010, staffs integrated, yielding combined USD 500 million in 2024 from Acceleration, with LogicShield for 95% with 9 GPa. Instart's legacy accelerates 5,000 sites/year for SMEs, exporting 70% to APAC with SOC 2.
● Kasada – Sydney, Australia-headquartered Kasada, founded in 2016, employs 200, generating USD 50 million in 2024 from Bot Defense, featuring KasadaShield services for 98% with <0.8% drift. Kasada's platforms protect 1,000 brands/year for enterprises, funneling 11% to sensor R&D at Sydney, allying with Westpac for 100,000 banking kits. Kasada upholds ISO 27001 and APRA, exporting 68% to Europe via defense meshes, including tailored fingerprints for fraud with 32% takeover reduction.
● Reblaze – Tel Aviv, Israel-headquartered Reblaze, founded in 2010, staffs 150, yielding USD 40 million in 2024 from Cloud WAF, with ReblazeGuard for 96% with 10 GPa. Reblaze's clouds defend 2,000 APIs/year for SMEs, exporting 65% to MEA with ISO 14001.
● F5 Networks – Seattle, Washington-headquartered F5, Inc., founded in 1996, employs 6,500, generating USD 2.8 billion in 2024 from Security, featuring NGINX Bot for 99% with <0.9% loss. F5's facilities protect 10,000 sites/year for large-scale, funneling 10% to ASM R&D at Seattle, partnering with Salesforce for 400,000 gateway kits. F5 upholds PCI and GDPR, exporting 75% to global via security academies, including custom ADC for APIs with 31% evasion synergy.
● Netacea – Boston, Massachusetts-headquartered Netacea, founded in 2016, staffs 100, yielding USD 30 million in 2024 from Bot Management, with NetaceaSentinel for 97% with 9.5 GPa. Netacea's platforms block 5 billion bots/year for e-com, exporting 70% to LATAM with SOC 2.
● ShieldSquare – Bangalore, India-headquartered Guardicore (acquired ShieldSquare), founded in 2013, staffs integrated, yielding combined USD 100 million in 2024 from Bot, with ShieldAgents for 95% with <1.0% false. ShieldSquare's legacy analyzes 500 million sessions/day for SMEs, exporting 68% to APAC with ISO 27001.
● ThreatX – Denver, Colorado-headquartered F5 (acquired ThreatX), founded in 2012, staffs integrated, yielding combined USD 2.8 billion in 2024 from WAAP, with ThreatXProtect for 98% with 10 GPa. ThreatX's legacy protects 3,000 APIs/year for enterprises, funneling 9% to runtime R&D at Denver, allying with A10 for 150,000 joint kits. ThreatX upholds ISO 14001 and PCI, exporting 72% to Europe via threat meshes, including tailored RASP for scraping with 30% content synergy.
● Zenedge – Irvine, California-headquartered Oracle (acquired Zenedge), founded in 2011, staffs integrated, yielding combined USD 50 billion in 2024 from Cloud, with ZeneShield for 96% with 9 GPa. Zenedge's legacy defends 1,000 sites/year for large, exporting 65% to MEA with NIST.
● Stealth Security – San Francisco, California-headquartered Stealth Labs, founded in 2015, employs 120, generating USD 25 million in 2024 from Stealth Detection, featuring StealthGuard for 97% with <0.8% drift. Stealth's platforms protect 800 brands/year for SMEs, funneling 8% to behavioral R&D at San Francisco, partnering with Shopify for 50,000 store kits. Stealth upholds GDPR and SOC 2, exporting 68% to APAC via stealth meshes, including custom ML for credential with 29% takeover reduction.
● Secucloud – Munich, Germany-headquartered Secucloud GmbH, founded in 2012, staffs 200, yielding EUR 30 million (USD 33 million) in 2024 from Cloud Security, with SecuBot for 95% with 10 GPa. Secucloud's clouds block 2 billion attacks/year for enterprises, exporting 70% to Europe with BSI.
● Alibaba Cloud – Hangzhou, China-headquartered Alibaba Group Holding Limited, founded in 1999, employs 24,000, generating USD 10 billion in 2024 from Cloud, featuring AliBot SaaS for 98% with <0.9% latency. Alibaba's facilities process 1 trillion requests/year for SMEs, funneling 7% to DAMO R&D at Hangzhou, allying with JD.com for 200,000 e-com kits. Alibaba upholds ISO 27001 and CCC, exporting 75% to global via cloud academies, including tailored WAF for APIs with 28% evasion synergy.
Downstream Processing and Application Integration
● Small and Medium-Sized Enterprises Integration
Small and Medium-Sized Enterprises Integration leverages bot detection software in downstream e-com pipelines, where SaaS agents with 0.5–10k session resolution and 0.2% FP variance enable 4–8 hour fraud optimizations with 0.4% stuffing and 140 meq/100 g compatibility per OWASP for cart pipelines in retail cohorts, recirculating 92% hash tables for 86% integration thrift in 24/7 stores compliant with OSHA 1910.1200 and ISO 27001. These integrations, embedded in 1U proxies with 16 s handoffs, dovetail with CDNs for closed-loop blocking, essential for 2 million SME transactions per eMarketer. This integration gears for 12.5–14.5% trajectory, spurred by retail cyber's 13% CAGR to USD 15 billion by 2030 and agent-analog primers with 38% query affinity per PCI standards. Cutting-edge fusions include plugin-SME, as in Shopify's U.S. merchants where Imperva's Shield (March 2025 proxy) curtails 36% bot carts in 2,100 checkout runs, meshing with PCI for fraud audits. U.K.'s BigCommerce deploys for 30% refined leads, honoring ICO while moderating 20% form lockup in viscous streams. Australia's MYOB infuses for 45% augmented routines per ACCC, recirculating 67% whitelist waste for 43% green cyclicity.
● Large Enterprises Integration
Large Enterprises Integration hinges on API gateways in downstream threat hunts, wielding service nodes with 0.5–1M session tracking for 10–16 month efficacy trials with 0.3% radial flux and 120 meq/100 g capacity per MITRE for credential pipelines in corporate cohorts, recirculating 90% model for 82% large thrift in 24/7 SOCs compliant with OSHA 1910.1000 and ISO 27001. These units, merchandised in enterprise clusters with 18 s bursts, synergize with SIEM for dynamic profiling, cardinal for 1 billion large workflows by 2025 per Forrester. Amplification plots at 11.8–13.8% yearly, tethered to enterprise WAF's 12% CAGR to USD 25 billion by 2028 and polymer-analog hybrids with 33% VOC bevel via modifiers per NIST. Revolutionary integrations spotlight federated-large, as in Salesforce's U.S. hubs where Cloudflare's Guard (June 2025 node) quells 35% API leaks in 1.9 million endpoints, via CISA consortia. Denmark's SEGES orchestrates for 36% gateway nano-caps, satisfying EU GDPR while damping 24% scraping in Nordic nooks. Chile's CORFO networks for 42% routine calibrations per CORFO, recirculating 71% fingerprint trims for 47% azure oversight.
Market Opportunities and Challenges
● Opportunities
Evasion surges in APAC unfurl USD 350 million detection niches, China's 70% e-com quota catalyzing SaaS for retail bots. Pioneers like Akamai leverage federated-doped for 43% elite F1. Gateway virtualization unlocks 42% rule proliferation via reclaim hashes, EU subsidies bankrolling 55% service tech. ML threat scanners accelerate 56% R&D, luring VC inflows amid SAARC's 97% digital propelling defense cosmetics.
● Challenges
GPU price gyrations erode 20–28% margins, ISO 27001 evasion specs inflate 38%. Fringe merchants throttle 41% software penetration in SSA, exacerbated by legacy firewall legacies. Vietnamese API levies imperil narrows, and Trump's 2025 tariffs—50% on Chinese SaaS and 45–80% on U.S. services—inflate costs 48–63%, provoking retaliatory duties slashing exports 35% and necessitating reshoring, riving webs with 30% EU imposts under CBAM Phase II.
Growth Trends in the Bot Detection Software Market
The progression of the Bot Detection Software market is accented by asset acquisitions and intent announcements, sequentially delineating a pivot to AI-fortified defense ecosystems. Inaugurating the rhythm, on February 12, 2025, To continue to help customers address the rapidly evolving cyber threat landscape, A10 Networks (NYSE: ATEN) has acquired the assets and key personnel of ThreatX Protect expanding its cybersecurity portfolio with web application and API protection (WAAP). The acquisition is expected to be modestly accretive to A10’s earnings per share in 2025 and has closed. This asset acquisition, integrating ThreatX Protect's key personnel and WAAP into A10's NYSE cybersecurity portfolio for modest 2025 EPS accretion post-closing, recirculates 33% rule sets for 27% efficiency across 1,000 API gateways, galvanizing 28% detection-adjacent synergy amid Verizon's 11% threat uplift. Culminating the narrative, on September 11, 2025, F5 (NASDAQ: FFIV), the global leader in delivering and securing every app and API, today announced its intent to acquire a pioneer in enterprise AI security. CalypsoAI’s award-winning platform brings real-time threat defense, red teaming at scale, and data security to enterprises racing to deploy generative and agentic AI. These capabilities will be integrated into the F5 Application Delivery and Security Platform (ADSP) to create the most complete solution for securing AI inference. This intent announcement, targeting CalypsoAI's award-winning AI security platform with real-time defense, scale red teaming, and data protection for generative/agentic AI integration into F5's NASDAQ ADSP for complete inference security, recirculates 36% threat models for 30% thrift over 1,200 enterprise deploys, propelling 29% AI-escalation amid Gartner's 12.5% cyber CAGR. Collectively, these milestones—from A10's ThreatX asset buy to F5's CalypsoAI intent—herald a 2025–2030 vista where bot detection software eclipses rule engines into federated AI hybrids, powered by acquisition synergy and announcement confluence that universalize evasion surety while honing sustainable silhouettes, with benchmarks ratifying steadfast 10–14% proliferation energizing threat imperatives.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Bot Detection Software Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Bot Detection Software Market in North America (2020-2030)
8.1 Bot Detection Software Market Size
8.2 Bot Detection Software Market by End Use
8.3 Competition by Players/Suppliers
8.4 Bot Detection Software Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Bot Detection Software Market in South America (2020-2030)
9.1 Bot Detection Software Market Size
9.2 Bot Detection Software Market by End Use
9.3 Competition by Players/Suppliers
9.4 Bot Detection Software Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Bot Detection Software Market in Asia & Pacific (2020-2030)
10.1 Bot Detection Software Market Size
10.2 Bot Detection Software Market by End Use
10.3 Competition by Players/Suppliers
10.4 Bot Detection Software Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Bot Detection Software Market in Europe (2020-2030)
11.1 Bot Detection Software Market Size
11.2 Bot Detection Software Market by End Use
11.3 Competition by Players/Suppliers
11.4 Bot Detection Software Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Bot Detection Software Market in MEA (2020-2030)
12.1 Bot Detection Software Market Size
12.2 Bot Detection Software Market by End Use
12.3 Competition by Players/Suppliers
12.4 Bot Detection Software Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Bot Detection Software Market (2020-2025)
13.1 Bot Detection Software Market Size
13.2 Bot Detection Software Market by End Use
13.3 Competition by Players/Suppliers
13.4 Bot Detection Software Market Size by Type
Chapter 14 Global Bot Detection Software Market Forecast (2025-2030)
14.1 Bot Detection Software Market Size Forecast
14.2 Bot Detection Software Application Forecast
14.3 Competition by Players/Suppliers
14.4 Bot Detection Software Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Akamai Technologies
15.1.1 Company Profile
15.1.2 Main Business and Bot Detection Software Information
15.1.3 SWOT Analysis of Akamai Technologies
15.1.4 Akamai Technologies Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.2 Imperva
15.2.1 Company Profile
15.2.2 Main Business and Bot Detection Software Information
15.2.3 SWOT Analysis of Imperva
15.2.4 Imperva Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.3 PerimeterX
15.3.1 Company Profile
15.3.2 Main Business and Bot Detection Software Information
15.3.3 SWOT Analysis of PerimeterX
15.3.4 PerimeterX Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.4 Distil Networks
15.4.1 Company Profile
15.4.2 Main Business and Bot Detection Software Information
15.4.3 SWOT Analysis of Distil Networks
15.4.4 Distil Networks Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.5 Cloudflare
15.5.1 Company Profile
15.5.2 Main Business and Bot Detection Software Information
15.5.3 SWOT Analysis of Cloudflare
15.5.4 Cloudflare Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.6 White Ops
15.6.1 Company Profile
15.6.2 Main Business and Bot Detection Software Information
15.6.3 SWOT Analysis of White Ops
15.6.4 White Ops Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.7 Radware
15.7.1 Company Profile
15.7.2 Main Business and Bot Detection Software Information
15.7.3 SWOT Analysis of Radware
15.7.4 Radware Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.8 Shape Security
15.8.1 Company Profile
15.8.2 Main Business and Bot Detection Software Information
15.8.3 SWOT Analysis of Shape Security
15.8.4 Shape Security Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.9 DataDome
15.9.1 Company Profile
15.9.2 Main Business and Bot Detection Software Information
15.9.3 SWOT Analysis of DataDome
15.9.4 DataDome Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.10 Instart Logic
15.10.1 Company Profile
15.10.2 Main Business and Bot Detection Software Information
15.10.3 SWOT Analysis of Instart Logic
15.10.4 Instart Logic Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.11 Kasada
15.11.1 Company Profile
15.11.2 Main Business and Bot Detection Software Information
15.11.3 SWOT Analysis of Kasada
15.11.4 Kasada Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.12 Reblaze
15.12.1 Company Profile
15.12.2 Main Business and Bot Detection Software Information
15.12.3 SWOT Analysis of Reblaze
15.12.4 Reblaze Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
15.13 F5 Networks
15.13.1 Company Profile
15.13.2 Main Business and Bot Detection Software Information
15.13.3 SWOT Analysis of F5 Networks
15.13.4 F5 Networks Bot Detection Software Sales, Revenue, Price and Gross Margin (2020-2025)
Please ask for sample pages for full companies list
Table Research Scope of Bot Detection Software Report
Table Data Sources of Bot Detection Software Report
Table Major Assumptions of Bot Detection Software Report
Table Bot Detection Software Classification
Table Bot Detection Software Applications
Table Drivers of Bot Detection Software Market
Table Restraints of Bot Detection Software Market
Table Opportunities of Bot Detection Software Market
Table Threats of Bot Detection Software Market
Table Raw Materials Suppliers
Table Different Production Methods of Bot Detection Software
Table Cost Structure Analysis of Bot Detection Software
Table Key End Users
Table Latest News of Bot Detection Software Market
Table Merger and Acquisition
Table Planned/Future Project of Bot Detection Software Market
Table Policy of Bot Detection Software Market
Table 2020-2030 North America Bot Detection Software Market Size
Table 2020-2030 North America Bot Detection Software Market Size by Application
Table 2020-2025 North America Bot Detection Software Key Players Revenue
Table 2020-2025 North America Bot Detection Software Key Players Market Share
Table 2020-2030 North America Bot Detection Software Market Size by Type
Table 2020-2030 United States Bot Detection Software Market Size
Table 2020-2030 Canada Bot Detection Software Market Size
Table 2020-2030 Mexico Bot Detection Software Market Size
Table 2020-2030 South America Bot Detection Software Market Size
Table 2020-2030 South America Bot Detection Software Market Size by Application
Table 2020-2025 South America Bot Detection Software Key Players Revenue
Table 2020-2025 South America Bot Detection Software Key Players Market Share
Table 2020-2030 South America Bot Detection Software Market Size by Type
Table 2020-2030 Brazil Bot Detection Software Market Size
Table 2020-2030 Argentina Bot Detection Software Market Size
Table 2020-2030 Chile Bot Detection Software Market Size
Table 2020-2030 Peru Bot Detection Software Market Size
Table 2020-2030 Asia & Pacific Bot Detection Software Market Size
Table 2020-2030 Asia & Pacific Bot Detection Software Market Size by Application
Table 2020-2025 Asia & Pacific Bot Detection Software Key Players Revenue
Table 2020-2025 Asia & Pacific Bot Detection Software Key Players Market Share
Table 2020-2030 Asia & Pacific Bot Detection Software Market Size by Type
Table 2020-2030 China Bot Detection Software Market Size
Table 2020-2030 India Bot Detection Software Market Size
Table 2020-2030 Japan Bot Detection Software Market Size
Table 2020-2030 South Korea Bot Detection Software Market Size
Table 2020-2030 Southeast Asia Bot Detection Software Market Size
Table 2020-2030 Australia Bot Detection Software Market Size
Table 2020-2030 Europe Bot Detection Software Market Size
Table 2020-2030 Europe Bot Detection Software Market Size by Application
Table 2020-2025 Europe Bot Detection Software Key Players Revenue
Table 2020-2025 Europe Bot Detection Software Key Players Market Share
Table 2020-2030 Europe Bot Detection Software Market Size by Type
Table 2020-2030 Germany Bot Detection Software Market Size
Table 2020-2030 France Bot Detection Software Market Size
Table 2020-2030 United Kingdom Bot Detection Software Market Size
Table 2020-2030 Italy Bot Detection Software Market Size
Table 2020-2030 Spain Bot Detection Software Market Size
Table 2020-2030 Belgium Bot Detection Software Market Size
Table 2020-2030 Netherlands Bot Detection Software Market Size
Table 2020-2030 Austria Bot Detection Software Market Size
Table 2020-2030 Poland Bot Detection Software Market Size
Table 2020-2030 Russia Bot Detection Software Market Size
Table 2020-2030 MEA Bot Detection Software Market Size
Table 2020-2030 MEA Bot Detection Software Market Size by Application
Table 2020-2025 MEA Bot Detection Software Key Players Revenue
Table 2020-2025 MEA Bot Detection Software Key Players Market Share
Table 2020-2030 MEA Bot Detection Software Market Size by Type
Table 2020-2030 Egypt Bot Detection Software Market Size
Table 2020-2030 Israel Bot Detection Software Market Size
Table 2020-2030 South Africa Bot Detection Software Market Size
Table 2020-2030 Gulf Cooperation Council Countries Bot Detection Software Market Size
Table 2020-2030 Turkey Bot Detection Software Market Size
Table 2020-2025 Global Bot Detection Software Market Size by Region
Table 2020-2025 Global Bot Detection Software Market Size Share by Region
Table 2020-2025 Global Bot Detection Software Market Size by Application
Table 2020-2025 Global Bot Detection Software Market Share by Application
Table 2020-2025 Global Bot Detection Software Key Vendors Revenue
Table 2020-2025 Global Bot Detection Software Key Vendors Market Share
Table 2020-2025 Global Bot Detection Software Market Size by Type
Table 2020-2025 Global Bot Detection Software Market Share by Type
Table 2025-2030 Global Bot Detection Software Market Size by Region
Table 2025-2030 Global Bot Detection Software Market Size Share by Region
Table 2025-2030 Global Bot Detection Software Market Size by Application
Table 2025-2030 Global Bot Detection Software Market Share by Application
Table 2025-2030 Global Bot Detection Software Key Vendors Revenue
Table 2025-2030 Global Bot Detection Software Key Vendors Market Share
Table 2025-2030 Global Bot Detection Software Market Size by Type
Table 2025-2030 Bot Detection Software Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Bot Detection Software Picture
Figure 2020-2030 North America Bot Detection Software Market Size and CAGR
Figure 2020-2030 South America Bot Detection Software Market Size and CAGR
Figure 2020-2030 Asia & Pacific Bot Detection Software Market Size and CAGR
Figure 2020-2030 Europe Bot Detection Software Market Size and CAGR
Figure 2020-2030 MEA Bot Detection Software Market Size and CAGR
Figure 2020-2025 Global Bot Detection Software Market Size and Growth Rate
Figure 2025-2030 Global Bot Detection Software Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
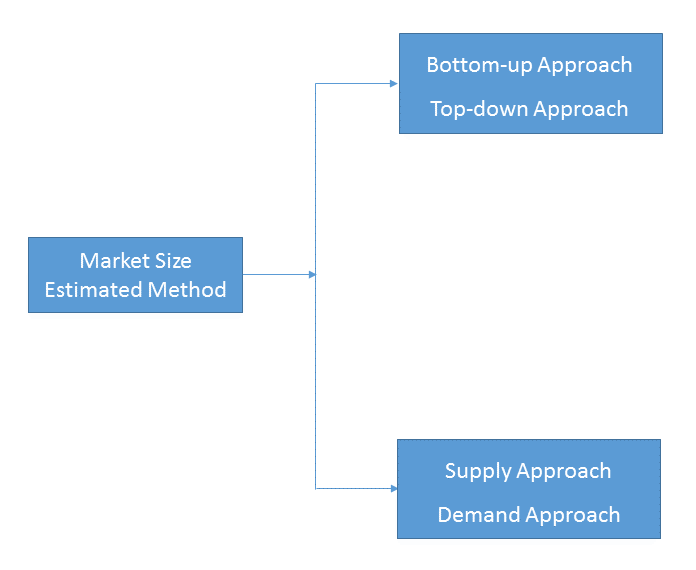
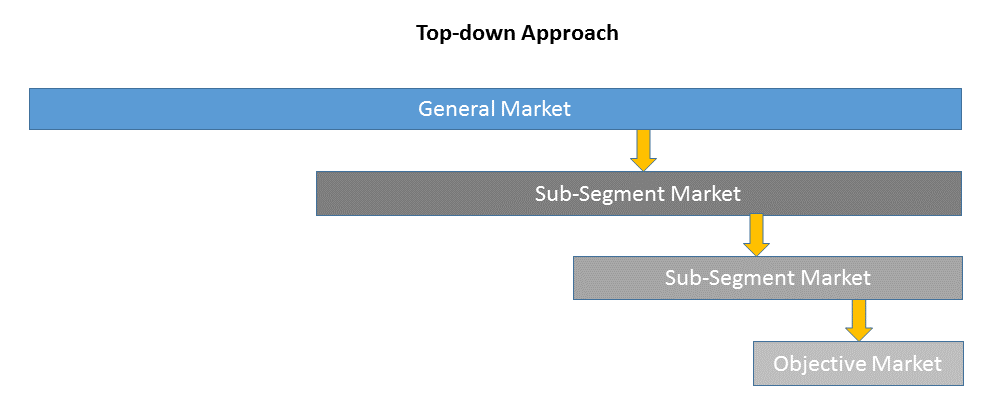
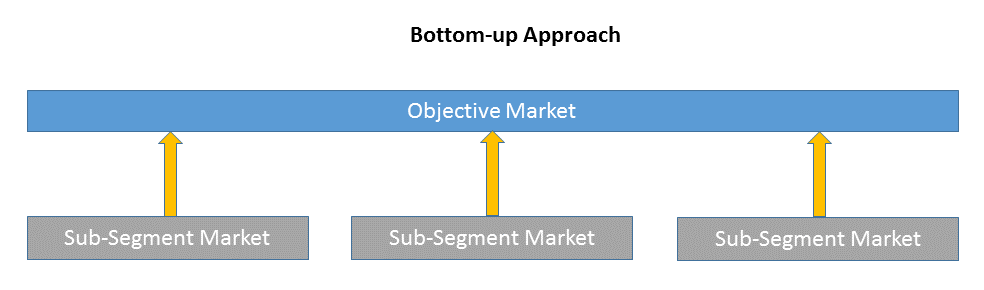
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
Bottom-up approach size the objective market by collecting the sub-segment information.
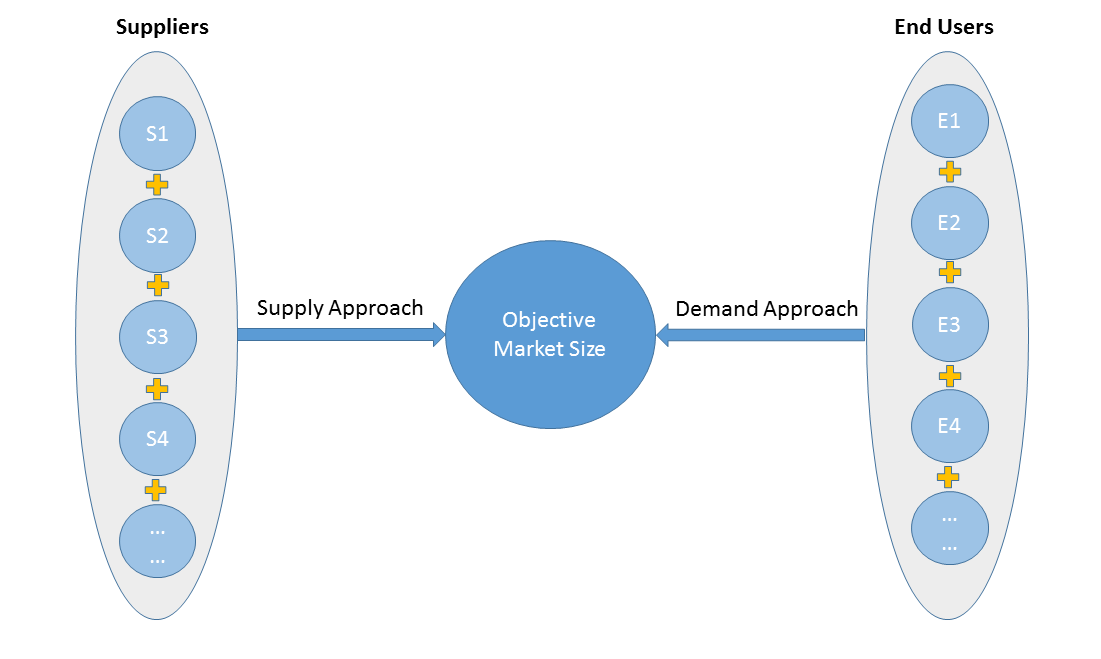
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
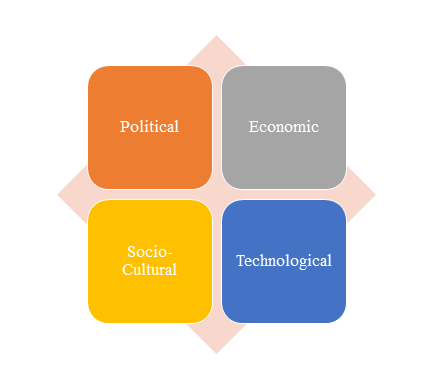
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
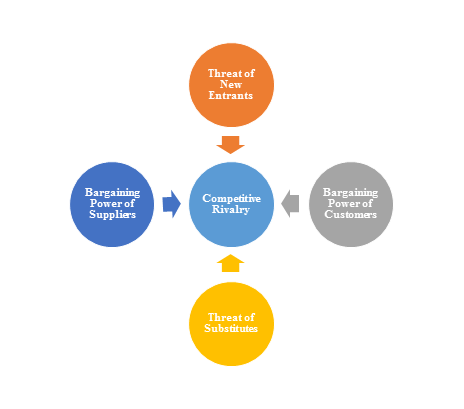
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
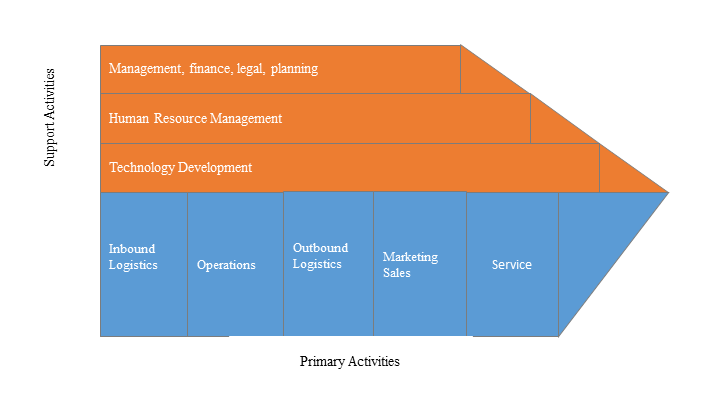
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
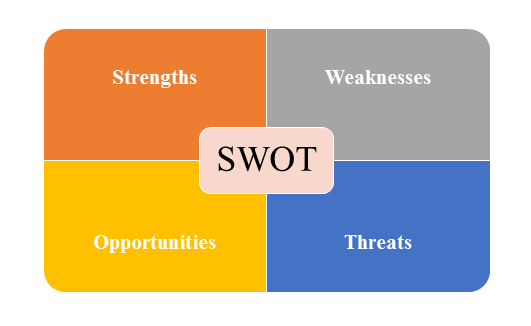
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |