Access Control as a Service (ACaaS) Market Insights 2026, Analysis and Forecast to 2031
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
1. Industry Overview
Access Control as a Service (ACaaS) represents a paradigm shift in the physical security industry, marking the transition from traditional, on-premise hardware-centric models to agile, cloud-based software solutions. Fundamentally, ACaaS is a method of providing identity management and physical access control where the software hosting and database management are removed from the client's site and handled by a third-party vendor via the cloud. This model allows businesses to manage global security operations from a single, centralized interface, leveraging the power of the Internet of Things (IoT) to offer real-time control and visibility.
In a traditional setup, an organization purchases servers, installs software locally, and maintains the IT infrastructure required to run the access control system. This "perpetual license" model often results in aging software, security vulnerabilities due to unpatched servers, and limited remote accessibility. Conversely, ACaaS operates on a subscription-based model (SaaS). The "brains" of the system reside in the cloud, while the local hardware (readers, controllers, locks) communicates securely with these cloud servers.
● Strategic Enabler for Modern Business
Within the broader scope of security management, ACaaS is increasingly viewed not merely as a utility for locking and unlocking doors, but as a strategic enabler. It integrates physical security with digital operations, offering:
● Real-time Control: Administrators can grant or revoke access credentials instantly from any location using a mobile device or web browser.
● Automated Compliance: The system automatically logs all entry and exit events, creating immutable audit trails essential for regulatory compliance in sectors like healthcare and finance.
● Cyber-liability Management: By offloading server maintenance to specialized providers, organizations reduce the risk of internal network vulnerabilities. Leading ACaaS providers utilize enterprise-grade encryption and regular security patches, often exceeding the cybersecurity capabilities of a typical end-user organization.
● Cost Efficiency: The shift from Capital Expenditure (CapEx) to Operational Expenditure (OpEx) allows organizations to avoid heavy upfront investments in servers and IT infrastructure, paying instead for what they use on a recurring basis.
The core product ecosystem of ACaaS includes cloud-hosted platforms, mobile credentials (using smartphones as keys), wireless locks, and increasingly, integration with biometrics and video surveillance (VSaaS), creating a unified physical security posture.
2. Market Size and Growth Trajectory
The global Access Control as a Service market is currently in a phase of accelerated expansion, outpacing traditional legacy access control markets.
● Market Valuation and Forecast
Based on comprehensive market analysis, the global market size for ACaaS is estimated to reach between 1.4 billion and 2.4 billion USD by 2026. The market is projected to maintain a robust growth trajectory through the end of the decade. For the period extending to 2031, the industry is expected to witness a Compound Annual Growth Rate (CAGR) ranging from 10% to 18%.
● Key Growth Drivers
Several macroeconomic and technological factors are fueling this double-digit growth:
● Urbanization and Smart Cities: Rapid urbanization is driving the construction of intelligent commercial and residential complexes that require centralized security management.
● Subscription Economy: The broader B2B shift towards subscription models is making high-end security technology accessible to Small and Medium Enterprises (SMEs) that previously could not afford enterprise-grade systems.
● Remote Work and Hybrid Models: The post-pandemic reality of hybrid work requires flexible security systems that can handle fluctuating occupancy and remote administration, a core competency of ACaaS.
● Technological Convergence: The integration of mobile access (Bluetooth Low Energy/NFC), biometrics, and AI-driven analytics is prompting organizations to upgrade legacy magnetic stripe card systems to modern cloud-based alternatives.
3. Regional Market Analysis
The adoption of ACaaS varies globally, influenced by the maturity of cloud infrastructure, internet penetration, and regulatory frameworks regarding data privacy.
● North America
North America stands as the largest and most mature market for ACaaS.
* Market Dominance: This region commands a significant portion of the global market share, driven by a high acceptance of cloud technologies and a strong demand for retrofitting legacy systems in established infrastructure.
* Sector Demand: There is robust demand across property management, retail, education, healthcare, and utilities. The "PropTech" (Property Technology) boom in the United States has particularly accelerated ACaaS adoption in the multifamily residential market, where tenants demand mobile-first living experiences.
* Regulatory Environment: The presence of strict compliance requirements in healthcare (HIPAA) and finance drives the need for the automated reporting features inherent in ACaaS platforms.
● Europe
Europe represents a significant and growing market, though with distinct characteristics driven by privacy regulations.
* GDPR and Privacy: The General Data Protection Regulation (GDPR) has forced ACaaS providers to be extremely transparent about data hosting and processing. This has led to the rise of European-based cloud providers and hybrid solutions that ensure data sovereignty.
* Smart Buildings: Western Europe, particularly the UK, Germany, and the Nordics, is seeing high adoption rates linked to energy efficiency and smart building initiatives, where access control integrates with lighting and HVAC systems.
● Asia Pacific
The Asia Pacific region is anticipated to experience the highest growth rate during the forecast period.
* Infrastructure Boom: Rapid construction of commercial hubs and residential high-rises in emerging economies creates a "greenfield" opportunity where developers install cloud-native systems from the start, skipping the legacy on-premise phase.
* Mobile First: The region's high mobile penetration rates make mobile-based access control (using smartphones instead of cards) particularly popular.
4. Market Segmentation: Application and Type
● By Application
* Commercial and Retail:
For retail chains, ACaaS is transformative. It allows a headquarters security team to manage employee access across hundreds of store locations simultaneously. It simplifies the onboarding and offboarding of staff in a high-turnover industry, instantly revoking access when an employee leaves to prevent theft.
* Education (K-12 and Higher Ed):
Schools and universities are prioritizing "lockdown" capabilities. ACaaS allows administrators to trigger campus-wide lockdowns remotely via mobile apps in case of emergencies. Furthermore, it manages complex access privileges for students, faculty, and temporary visitors across sprawling campuses.
* Healthcare:
Hospitals utilize ACaaS to secure sensitive areas like pharmacies, nurseries, and server rooms. The technology facilitates the management of complex shift patterns and integrates with HR systems to ensure only active, credentialed staff can access restricted zones.
* Utilities and Critical Infrastructure:
Utility companies often have unmanned remote sites (substations, water treatment plants). ACaaS allows for the remote granting of temporary credentials to maintenance contractors, eliminating the need for physical key exchanges and ensuring a digital log of who entered the facility and when.
* Residential (Multifamily):
In the residential sector, ACaaS is a key selling point for luxury apartments. It enables keyless entry for residents, temporary codes for dog walkers or cleaners, and seamless access for package delivery services, enhancing both security and convenience.
● By Type
* SaaS-based (Software as a Service):
This is the dominant delivery model. The software is licensed on a subscription basis and is centrally hosted. It offers the highest level of flexibility and automatic updates, ensuring the client always utilizes the latest features and security patches without manual intervention.
* Cloud-based (Pure vs. Hybrid):
* Pure Cloud: The controller communicates directly with the cloud. If the internet fails, the local controller retains a cache of credentials to allow entry, but changes cannot be made until connectivity is restored.
* Hybrid Cloud: Combines on-premise appliances with cloud management. This is often preferred by enterprises with critical uptime requirements or limited bandwidth, ensuring full local functionality even during network outages while still offering remote management.
* Web-based / Mobile-based:
This refers to the user interface. Modern ACaaS is characterized by browser-agnostic web portals and native mobile applications for both administrators (to manage the system) and end-users (to unlock doors).
5. Key Market Players and Competitive Landscape
The ACaaS market is competitive, featuring a mix of traditional security giants pivoting to the cloud and agile, cloud-native startups disrupting the status quo.
● Genetec Inc.:
Recognized as the global largest ACaaS service enterprise, Genetec is a pioneer in unified physical security. Their flagship platform, Security Center, creates a cohesive ecosystem that blends access control (Synergis) with video surveillance and license plate recognition. Genetec's strength lies in its enterprise-grade architecture, catering to governments, airports, and large multinational corporations. Their cloud offering, Genetec Stratocast and Synergis Cloud Link, allows for a hybrid approach that bridges legacy hardware with modern cloud capabilities.
● ASSA ABLOY:
A global leader in access solutions, ASSA ABLOY has aggressively expanded its digital and cloud portfolio. Through acquisitions (such as HID Global) and internal development, they offer a vast array of wireless locks and digital credentials that integrate seamlessly with ACaaS platforms. Their focus is on the convergence of hardware excellence with digital services, enabling mobile keys and "Seos" credential technology.
● Kisi Inc.:
Kisi is a prominent "cloud-native" player, designed from the ground up for the modern workplace. Popular in the tech sector and co-working spaces, Kisi emphasizes user experience (UX), offering sleek hardware and a highly rated mobile app. Their platform features an open API, allowing deep integration with software like Slack, Google Workspace, and CRM systems, making security a part of the IT stack.
● Spintly:
Spintly is disrupting the market with a wireless, mesh-network approach. By shifting the intelligence from the controller to the edge (the reader and the mobile phone), Spintly significantly reduces the cabling infrastructure required for installation. This makes them highly attractive for retrofitting existing buildings where rewiring is cost-prohibitive.
● EasySecure:
Focusing on integration, EasySecure specializes in connecting access control with Time & Attendance, Workforce Management, and HR software. Their platform is highly valued in industries where access control is directly tied to payroll and working hours, such as logistics and construction.
6. Value Chain and Supply Chain Structure
The ACaaS value chain is evolving from a linear hardware supply model to a circular, service-oriented ecosystem.
● Hardware & Component Manufacturers (Upstream):
This tier includes manufacturers of readers, controllers, electromagnetic locks, and semiconductors. Companies here are increasingly embedding IoT capabilities and edge computing power into their devices to support cloud communication.
● Cloud Platform Providers & Software Developers:
This is the core of the ACaaS value chain. Companies like Genetec and Kisi develop the software architecture that manages identities, rules, and schedules. They rely on major public cloud infrastructure providers (like AWS, Azure, Google Cloud) to host their data centers, ensuring high availability and redundancy.
● Integration & API Ecosystem:
A crucial layer in ACaaS is the integration capability. The value chain now includes third-party software developers who build connectors between the ACaaS platform and other business tools (e.g., connecting Microsoft Azure Active Directory with the access control system to automate employee onboarding).
● Channel Partners (System Integrators and MSPs):
Unlike DIY smart home products, commercial ACaaS typically requires professional installation. System Integrators (SIs) and Managed Service Providers (MSPs) act as the bridge, installing the physical wiring and hardware, configuring the network, and often managing the subscription billing for the end client. The trend is shifting where SIs are becoming "Value-Added Resellers" of recurring revenue services rather than just one-off hardware installers.
● End Users (Downstream):
The organizations utilizing the service. The value proposition for them has shifted from "asset ownership" to "outcome assurance"—guaranteed security uptime and compliance without the burden of maintenance.
7. Market Opportunities and Challenges
● Opportunities
* Mobile Credentials & Digital Wallets:
The phasing out of plastic RFID cards presents a massive opportunity. Storing access credentials in Apple Wallet or Google Pay offers higher security (protected by the phone's biometrics) and greater convenience. ACaaS providers leading this transition stand to gain significant market share.
* Integration with Logical Security (Zero Trust):
There is a growing convergence between physical and cybersecurity. ACaaS systems are beginning to integrate with Identity and Access Management (IAM) systems. For instance, if an employee badges into the building in New York, but their credentials are used to log into the network from London five minutes later, the system can flag this anomaly. This "Cyber-Physical" security approach is a high-growth frontier.
* Data Analytics and Space Utilization:
ACaaS generates vast amounts of data regarding movement patterns. Providers can monetize this data by offering analytics dashboards that help Facility Managers optimize real estate usage (e.g., identifying underused meeting rooms or analyzing peak occupancy times to adjust HVAC schedules).
● Challenges
* Cybersecurity Risks:
As access control moves to the cloud, it becomes a target for cyberattacks. The fear of a "hackable door" remains a barrier to adoption. Providers must invest heavily in penetration testing, encryption, and multi-factor authentication to maintain trust. A significant breach in a major ACaaS provider could damage the reputation of the entire industry.
* Dependency on Internet Connectivity:
While most modern systems have local caching to allow entry during an outage, the loss of real-time visibility and remote management features during network downtime is a concern for critical infrastructure clients.
* Legacy Infrastructure Compatibility:
Millions of doors worldwide are secured by legacy systems using standard Wiegand wiring protocols. ACaaS providers face the challenge of creating hardware bridges that can "take over" these legacy readers without requiring a full "rip and replace," which is often too expensive for customers.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Access Control as a Service (ACaaS) Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Access Control as a Service (ACaaS) Market in North America (2021-2031)
8.1 Access Control as a Service (ACaaS) Market Size
8.2 Access Control as a Service (ACaaS) Market by End Use
8.3 Competition by Players/Suppliers
8.4 Access Control as a Service (ACaaS) Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Access Control as a Service (ACaaS) Market in South America (2021-2031)
9.1 Access Control as a Service (ACaaS) Market Size
9.2 Access Control as a Service (ACaaS) Market by End Use
9.3 Competition by Players/Suppliers
9.4 Access Control as a Service (ACaaS) Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Access Control as a Service (ACaaS) Market in Asia & Pacific (2021-2031)
10.1 Access Control as a Service (ACaaS) Market Size
10.2 Access Control as a Service (ACaaS) Market by End Use
10.3 Competition by Players/Suppliers
10.4 Access Control as a Service (ACaaS) Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Access Control as a Service (ACaaS) Market in Europe (2021-2031)
11.1 Access Control as a Service (ACaaS) Market Size
11.2 Access Control as a Service (ACaaS) Market by End Use
11.3 Competition by Players/Suppliers
11.4 Access Control as a Service (ACaaS) Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Access Control as a Service (ACaaS) Market in MEA (2021-2031)
12.1 Access Control as a Service (ACaaS) Market Size
12.2 Access Control as a Service (ACaaS) Market by End Use
12.3 Competition by Players/Suppliers
12.4 Access Control as a Service (ACaaS) Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Access Control as a Service (ACaaS) Market (2021-2026)
13.1 Access Control as a Service (ACaaS) Market Size
13.2 Access Control as a Service (ACaaS) Market by End Use
13.3 Competition by Players/Suppliers
13.4 Access Control as a Service (ACaaS) Market Size by Type
Chapter 14 Global Access Control as a Service (ACaaS) Market Forecast (2026-2031)
14.1 Access Control as a Service (ACaaS) Market Size Forecast
14.2 Access Control as a Service (ACaaS) Application Forecast
14.3 Competition by Players/Suppliers
14.4 Access Control as a Service (ACaaS) Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Genetec Inc.
15.1.1 Company Profile
15.1.2 Main Business and Access Control as a Service (ACaaS) Information
15.1.3 SWOT Analysis of Genetec Inc.
15.1.4 Genetec Inc. Access Control as a Service (ACaaS) Sales, Revenue, Price and Gross Margin (2021-2026)
15.2 ASSA Abloy
15.2.1 Company Profile
15.2.2 Main Business and Access Control as a Service (ACaaS) Information
15.2.3 SWOT Analysis of ASSA Abloy
15.2.4 ASSA Abloy Access Control as a Service (ACaaS) Sales, Revenue, Price and Gross Margin (2021-2026)
15.3 Kisi Inc.
15.3.1 Company Profile
15.3.2 Main Business and Access Control as a Service (ACaaS) Information
15.3.3 SWOT Analysis of Kisi Inc.
15.3.4 Kisi Inc. Access Control as a Service (ACaaS) Sales, Revenue, Price and Gross Margin (2021-2026)
15.4 Spintly
15.4.1 Company Profile
15.4.2 Main Business and Access Control as a Service (ACaaS) Information
15.4.3 SWOT Analysis of Spintly
15.4.4 Spintly Access Control as a Service (ACaaS) Sales, Revenue, Price and Gross Margin (2021-2026)
Please ask for sample pages for full companies list
Table Research Scope of Access Control as a Service (ACaaS) Report
Table Data Sources of Access Control as a Service (ACaaS) Report
Table Major Assumptions of Access Control as a Service (ACaaS) Report
Table Access Control as a Service (ACaaS) Classification
Table Access Control as a Service (ACaaS) Applications
Table Drivers of Access Control as a Service (ACaaS) Market
Table Restraints of Access Control as a Service (ACaaS) Market
Table Opportunities of Access Control as a Service (ACaaS) Market
Table Threats of Access Control as a Service (ACaaS) Market
Table Raw Materials Suppliers
Table Different Production Methods of Access Control as a Service (ACaaS)
Table Cost Structure Analysis of Access Control as a Service (ACaaS)
Table Key End Users
Table Latest News of Access Control as a Service (ACaaS) Market
Table Merger and Acquisition
Table Planned/Future Project of Access Control as a Service (ACaaS) Market
Table Policy of Access Control as a Service (ACaaS) Market
Table 2021-2031 North America Access Control as a Service (ACaaS) Market Size
Table 2021-2031 North America Access Control as a Service (ACaaS) Market Size by Application
Table 2021-2026 North America Access Control as a Service (ACaaS) Key Players Revenue
Table 2021-2026 North America Access Control as a Service (ACaaS) Key Players Market Share
Table 2021-2031 North America Access Control as a Service (ACaaS) Market Size by Type
Table 2021-2031 United States Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Canada Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Mexico Access Control as a Service (ACaaS) Market Size
Table 2021-2031 South America Access Control as a Service (ACaaS) Market Size
Table 2021-2031 South America Access Control as a Service (ACaaS) Market Size by Application
Table 2021-2026 South America Access Control as a Service (ACaaS) Key Players Revenue
Table 2021-2026 South America Access Control as a Service (ACaaS) Key Players Market Share
Table 2021-2031 South America Access Control as a Service (ACaaS) Market Size by Type
Table 2021-2031 Brazil Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Argentina Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Chile Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Peru Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Asia & Pacific Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Asia & Pacific Access Control as a Service (ACaaS) Market Size by Application
Table 2021-2026 Asia & Pacific Access Control as a Service (ACaaS) Key Players Revenue
Table 2021-2026 Asia & Pacific Access Control as a Service (ACaaS) Key Players Market Share
Table 2021-2031 Asia & Pacific Access Control as a Service (ACaaS) Market Size by Type
Table 2021-2031 China Access Control as a Service (ACaaS) Market Size
Table 2021-2031 India Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Japan Access Control as a Service (ACaaS) Market Size
Table 2021-2031 South Korea Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Southeast Asia Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Australia Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Europe Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Europe Access Control as a Service (ACaaS) Market Size by Application
Table 2021-2026 Europe Access Control as a Service (ACaaS) Key Players Revenue
Table 2021-2026 Europe Access Control as a Service (ACaaS) Key Players Market Share
Table 2021-2031 Europe Access Control as a Service (ACaaS) Market Size by Type
Table 2021-2031 Germany Access Control as a Service (ACaaS) Market Size
Table 2021-2031 France Access Control as a Service (ACaaS) Market Size
Table 2021-2031 United Kingdom Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Italy Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Spain Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Belgium Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Netherlands Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Austria Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Poland Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Russia Access Control as a Service (ACaaS) Market Size
Table 2021-2031 MEA Access Control as a Service (ACaaS) Market Size
Table 2021-2031 MEA Access Control as a Service (ACaaS) Market Size by Application
Table 2021-2026 MEA Access Control as a Service (ACaaS) Key Players Revenue
Table 2021-2026 MEA Access Control as a Service (ACaaS) Key Players Market Share
Table 2021-2031 MEA Access Control as a Service (ACaaS) Market Size by Type
Table 2021-2031 Egypt Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Israel Access Control as a Service (ACaaS) Market Size
Table 2021-2031 South Africa Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Gulf Cooperation Council Countries Access Control as a Service (ACaaS) Market Size
Table 2021-2031 Turkey Access Control as a Service (ACaaS) Market Size
Table 2021-2026 Global Access Control as a Service (ACaaS) Market Size by Region
Table 2021-2026 Global Access Control as a Service (ACaaS) Market Size Share by Region
Table 2021-2026 Global Access Control as a Service (ACaaS) Market Size by Application
Table 2021-2026 Global Access Control as a Service (ACaaS) Market Share by Application
Table 2021-2026 Global Access Control as a Service (ACaaS) Key Vendors Revenue
Table 2021-2026 Global Access Control as a Service (ACaaS) Key Vendors Market Share
Table 2021-2026 Global Access Control as a Service (ACaaS) Market Size by Type
Table 2021-2026 Global Access Control as a Service (ACaaS) Market Share by Type
Table 2026-2031 Global Access Control as a Service (ACaaS) Market Size by Region
Table 2026-2031 Global Access Control as a Service (ACaaS) Market Size Share by Region
Table 2026-2031 Global Access Control as a Service (ACaaS) Market Size by Application
Table 2026-2031 Global Access Control as a Service (ACaaS) Market Share by Application
Table 2026-2031 Global Access Control as a Service (ACaaS) Key Vendors Revenue
Table 2026-2031 Global Access Control as a Service (ACaaS) Key Vendors Market Share
Table 2026-2031 Global Access Control as a Service (ACaaS) Market Size by Type
Table 2026-2031 Access Control as a Service (ACaaS) Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Access Control as a Service (ACaaS) Picture
Figure 2021-2031 North America Access Control as a Service (ACaaS) Market Size and CAGR
Figure 2021-2031 South America Access Control as a Service (ACaaS) Market Size and CAGR
Figure 2021-2031 Asia & Pacific Access Control as a Service (ACaaS) Market Size and CAGR
Figure 2021-2031 Europe Access Control as a Service (ACaaS) Market Size and CAGR
Figure 2021-2031 MEA Access Control as a Service (ACaaS) Market Size and CAGR
Figure 2021-2026 Global Access Control as a Service (ACaaS) Market Size and Growth Rate
Figure 2026-2031 Global Access Control as a Service (ACaaS) Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
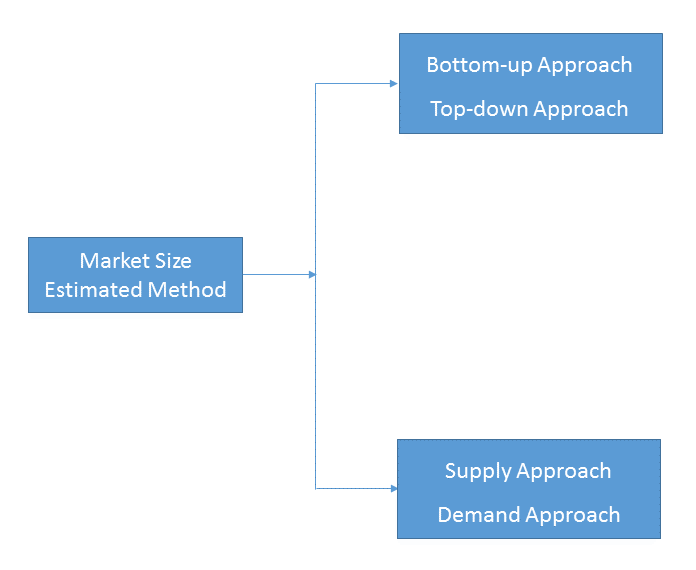
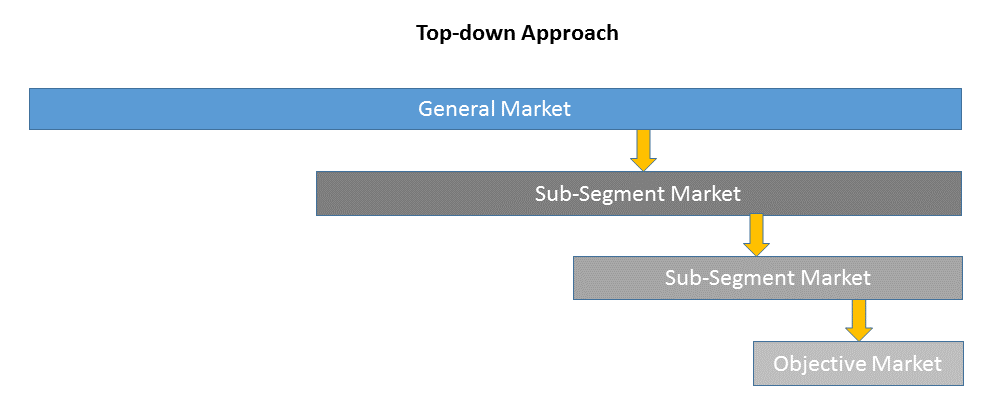
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
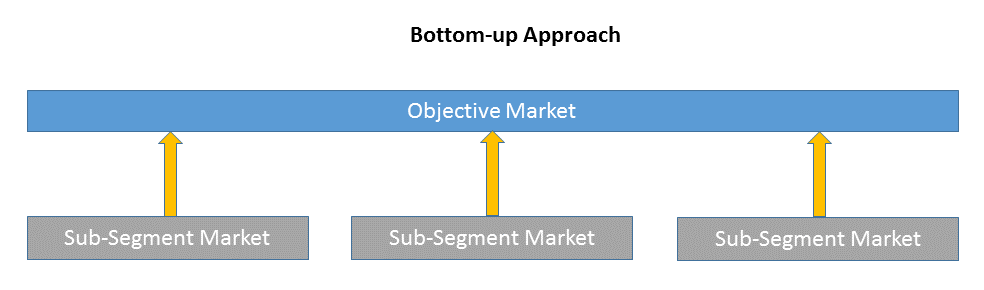
Bottom-up approach size the objective market by collecting the sub-segment information.
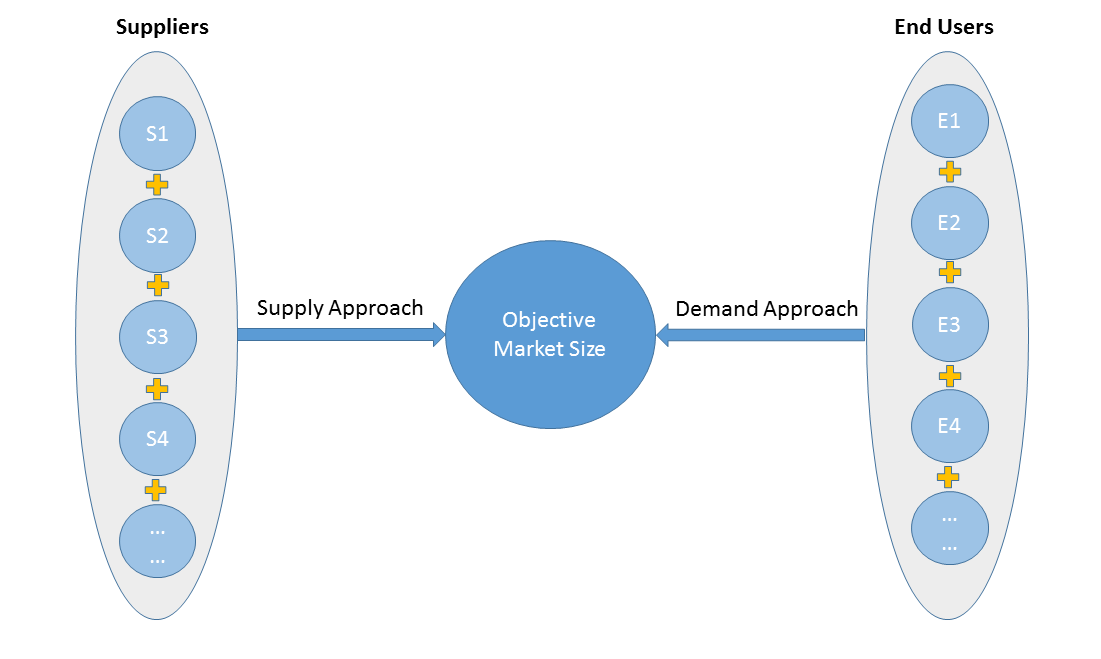
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
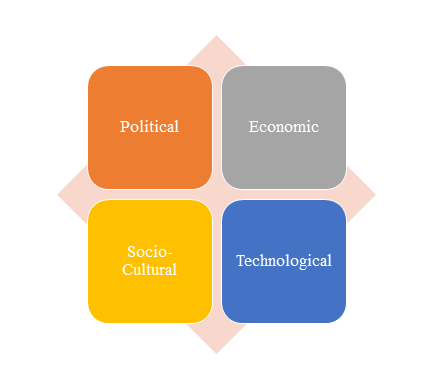
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
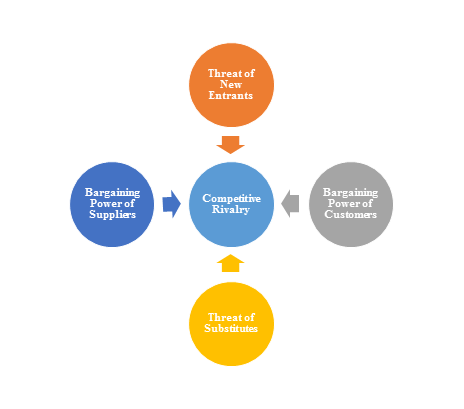
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
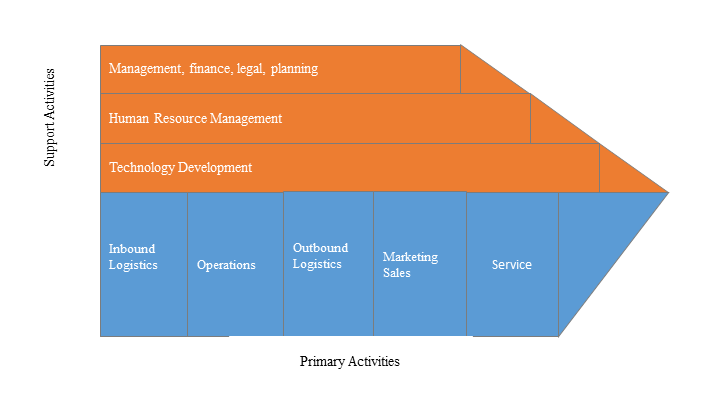
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
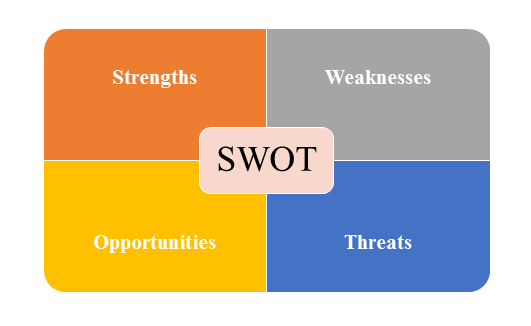
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |