Network Security Market Insights 2026, Analysis and Forecast to 2031
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
Industry Characteristics and Technological Evolution
The network security industry stands as the foundational pillar of the global digital economy, evolving from traditional perimeter-based defense systems into highly dynamic, identity-centric security architectures. Historically defined by hardware-based firewalls and Virtual Private Networks (VPNs), the industry is currently undergoing a structural transformation driven by the "Cloud-First" paradigm and the rise of remote work. Modern network security is increasingly characterized by the convergence of networking and security functions, commonly referred to as Secure Access Service Edge (SASE), which integrates Security Service Edge (SSE) with Software-Defined Wide Area Networking (SD-WAN).
A core characteristic of the contemporary landscape is the shift from "Implicit Trust" to "Zero Trust Architecture" (ZTA). In this model, the network assumes every connection attempt is a potential threat, requiring continuous verification of identity, device health, and context before granting access to specific applications rather than the entire network. This move toward granular micro-segmentation is a direct response to the increasing sophistication of cyber threats, including ransomware-as-a-service and advanced persistent threats (APTs) that exploit lateral movement within compromised networks.
As digital transformation accelerates across all industrial verticals, the demand for integrated security platforms that offer unified visibility across hybrid and multi-cloud environments has become paramount. Organizations are increasingly consolidating their security stacks to reduce complexity and "vendor fatigue," favoring "platformization"—the procurement of comprehensive security suites from a single provider rather than disparate point solutions. Based on capital expenditure trends in IT infrastructure, global cybersecurity spending patterns, and high-level corporate filings from leading technology firms, the global market size for Network Security is estimated to reach between USD 20.0 billion and USD 50.0 billion by 2026. The industry is projected to maintain a steady Compound Annual Growth Rate (CAGR) ranging from 7.0% to 17.0% through the 2026–2031 period, reflecting the non-discretionary nature of security spending in an era of heightened geopolitical and digital risk.
Regional Market Trends
The global demand for network security is distributed across all major geographic regions, though the drivers of growth vary significantly based on the maturity of local digital infrastructure and the stringency of data protection regulations.
North America remains the dominant regional market, with an estimated growth range of 6.5% to 15.5%. This growth is anchored by the United States, which hosts a significant portion of the world's leading security vendors and a high concentration of Global 2000 enterprises. The region's market is characterized by rapid early adoption of Zero Trust frameworks and SASE models. Furthermore, evolving federal mandates and executive orders regarding national cybersecurity resilience have compelled both public and private sector entities to upgrade legacy network defenses, particularly in critical infrastructure sectors like energy and finance.
The Asia-Pacific (APAC) region is expected to be the fastest-growing market, with a projected CAGR between 8.5% and 19.5% through 2031. This expansion is driven by massive investments in digital infrastructure in China, India, and Southeast Asia. In China, the market is influenced by robust national data security laws and the rapid build-out of 5G networks, which require sophisticated network slicing security. In India, the "Digital India" initiative and the burgeoning fintech ecosystem are creating a surge in demand for cloud-based network security to protect a vast, newly digitized consumer base. The region is also seeing a shift as domestic enterprises move directly from legacy systems to cloud-native security models, bypassing intermediate hardware-centric stages.
Europe represents a mature yet high-growth market, with an estimated growth range of 7.0% to 16.0%. The European landscape is heavily influenced by the General Data Protection Regulation (GDPR) and the Network and Information Security (NIS2) Directive. These regulatory frameworks place immense pressure on organizations to implement "Security by Design" and maintain high levels of network visibility. Consequently, there is strong demand in Germany, France, and the UK for sovereign cloud security solutions and localized data residency capabilities, as organizations seek to balance advanced threat protection with strict compliance requirements.
Latin America is a developing market with a projected growth range of 6.0% to 14.5%. Brazil and Mexico are the primary markets, where growth is fueled by the expansion of digital banking and the modernization of telecommunications infrastructure. While economic volatility can influence short-term IT budgets, the rising frequency of high-profile cyberattacks in the region has elevated network security to a board-level priority.
The Middle East and Africa (MEA) region is estimated to grow in the 7.5% to 18.0% range. The Gulf Cooperation Council (GCC) countries, particularly Saudi Arabia and the UAE, are investing heavily in "Vision 2030" style digital transformations. These initiatives involve the creation of smart cities and digital government platforms that require comprehensive, AI-driven network security to defend against increasingly complex regional cyber-threat actors.
Deployment and Application Analysis
Deployment Models
The network security market is bifurcated by deployment type: Cloud-based and On-premises.
Cloud-based: This is the fastest-growing segment, with an estimated growth range of 10.0% to 22.0%. The agility, scalability, and "pay-as-you-go" nature of cloud-native security (such as Firewall-as-a-Service and Secure Web Gateways) align perfectly with the needs of modern, distributed workforces. Enterprises are increasingly moving security controls to the "Edge" to reduce latency and improve the user experience.
On-premises: While the focus has shifted toward the cloud, on-premises deployment remains critical for highly regulated industries and legacy data centers. This segment is projected to grow at a more modest range of 3.0% to 8.5%. Innovation in this space is centered around High-Performance Firewalls capable of inspecting encrypted traffic (SSL/TLS) at multi-gigabit speeds without performance degradation.
Application Analysis
Large Enterprises: This segment accounts for the majority of market revenue, with a projected growth range of 7.5% to 16.5%. These organizations face the most complex threat landscapes and have the budgets to implement multi-layered, platform-centric security architectures. They are currently focusing on consolidating tools and improving Security Operations Center (SOC) efficiency through automation and AI.
Small & Medium Enterprises (SMEs): The SME segment is expected to grow at a higher CAGR of 9.0% to 18.5%. Historically underserved, SMEs are now high-priority targets for attackers. The shift toward simplified, cloud-based Managed Security Services (MSS) allows these organizations to access enterprise-grade network security without the need for a large internal cybersecurity team.
Company Landscape
The network security market is highly competitive, featuring a mix of legacy networking giants, cybersecurity platform leaders, and cloud-native disruptors.
Palo Alto Networks Inc. and Fortinet Inc. are recognized as the primary "Platform" leaders. Palo Alto has successfully pivoted from a hardware firewall leader to a comprehensive provider of SASE (Prisma Access) and automated security operations (Cortex). Fortinet differentiates itself through its proprietary SPU (Security Processing Unit) technology, which offers industry-leading price-performance for integrated networking and security, particularly for SD-WAN deployments.
Cisco Systems Inc. and Juniper Networks represent the traditional backbone of networking. Cisco is aggressively integrating security into its massive installed base of networking hardware, utilizing its "Cisco Security Cloud" to provide unified visibility. Juniper Networks, recently undergoing significant strategic shifts including acquisition activity by HPE, focuses on "AI-driven Networking" to simplify operations and enhance security through its Mist AI platform.
Check Point Software Technologies remains a stalwart in the industry, known for its high-security standards and "Infinity" architecture which provides consolidated protection across networks, clouds, and mobile devices.
CrowdStrike Holdings, Zscaler Inc., and Cloudflare Inc. represent the "Cloud-Native" vanguard. Zscaler is a pioneer in the Zero Trust Exchange, focusing on secure user-to-app and app-to-app connectivity without traditional network perimeters. Cloudflare leverages its massive global edge network to provide integrated security and performance, effectively making the Internet the corporate network. CrowdStrike, while primarily an endpoint leader, is expanding rapidly into network visibility and identity protection through its Falcon platform.
Broadcom Inc. (through its acquisition of Symantec and VMware) and Trend Micro are significant players serving the global enterprise and service provider markets. Broadcom focuses on high-end enterprise security and hybrid-cloud infrastructure, while Trend Micro provides a broad platform (Vision One) that integrates network security with endpoint and server protection.
Industry Value Chain Analysis
The value chain of network security is a complex ecosystem involving hardware manufacturing, software development, and service delivery.
Upstream: The value chain begins with the design and manufacturing of specialized semiconductors and networking hardware. Companies like Intel, NVIDIA, and specialized ASIC designers provide the raw processing power required for high-speed packet inspection. This stage also includes the development of foundational software and threat intelligence databases, where researchers identify new vulnerabilities and malware signatures.
Midstream: This is the core of the market, where security vendors integrate hardware and software into finished products and platforms. Significant value is added through the development of proprietary algorithms for intrusion prevention, sandboxing, and AI-driven behavioral analysis. In the cloud-native era, this stage also involves the management of global points of presence (PoPs) to deliver security services at the edge.
Distribution and Integration: Security solutions are delivered to end-users through a tiered system of distributors, Value-Added Resellers (VARs), and System Integrators. These partners provide critical localization, implementation, and training services. For many SMEs, Managed Security Service Providers (MSSPs) act as the primary interface, managing the security stack on the customer's behalf.
Downstream: The end-users—ranging from government agencies to small businesses—incorporate these solutions into their IT infrastructure. Value is realized here through risk mitigation, the prevention of costly data breaches, and the enablement of secure digital business processes.
Market Opportunities and Challenges
Opportunities
AI-Driven Automation: The integration of Generative AI into network security (AIOps) provides a massive opportunity to solve the "Cybersecurity Skills Gap." AI can automate the analysis of millions of network alerts, allowing human analysts to focus on the most critical threats.
IoT and OT Security: The proliferation of Internet of Things (IoT) and Operational Technology (OT) in manufacturing and utilities creates a vast new attack surface. Specialized network security solutions that understand industrial protocols (like Modbus or SCADA) represent a high-growth niche.
Secure Digital Sovereignty: As nations become more concerned about data localization and geopolitical influence, there is a rising opportunity for "Sovereign Cloud" security solutions that guarantee data remains within specific borders and is protected by local laws.
Challenges
Increasing Complexity: The paradox of modern security is that as tools become more powerful, the overall system becomes harder to manage. Misconfigurations in complex hybrid-cloud network security are a leading cause of data breaches.
Encrypted Traffic Inspection: With over 90% of web traffic now encrypted, attackers are increasingly hiding malware within encrypted streams. Inspecting this traffic at scale without violating privacy or slowing down the network is a major technical challenge.
Sophisticated Evasion Techniques: Threat actors are using AI to develop "Polymorphic Malware" and automated phishing campaigns that can bypass traditional signature-based network defenses, requiring a shift toward purely behavioral and identity-based security.
Macroeconomic and Geopolitical Pressures: Trade tensions and "Rip and Replace" mandates regarding certain national vendors can disrupt supply chains and force organizations to undergo unplanned, costly infrastructure overhauls.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Network Security Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Network Security Market in North America (2021-2031)
8.1 Network Security Market Size
8.2 Network Security Market by End Use
8.3 Competition by Players/Suppliers
8.4 Network Security Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Network Security Market in South America (2021-2031)
9.1 Network Security Market Size
9.2 Network Security Market by End Use
9.3 Competition by Players/Suppliers
9.4 Network Security Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Network Security Market in Asia & Pacific (2021-2031)
10.1 Network Security Market Size
10.2 Network Security Market by End Use
10.3 Competition by Players/Suppliers
10.4 Network Security Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Network Security Market in Europe (2021-2031)
11.1 Network Security Market Size
11.2 Network Security Market by End Use
11.3 Competition by Players/Suppliers
11.4 Network Security Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Network Security Market in MEA (2021-2031)
12.1 Network Security Market Size
12.2 Network Security Market by End Use
12.3 Competition by Players/Suppliers
12.4 Network Security Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Network Security Market (2021-2026)
13.1 Network Security Market Size
13.2 Network Security Market by End Use
13.3 Competition by Players/Suppliers
13.4 Network Security Market Size by Type
Chapter 14 Global Network Security Market Forecast (2026-2031)
14.1 Network Security Market Size Forecast
14.2 Network Security Application Forecast
14.3 Competition by Players/Suppliers
14.4 Network Security Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Palo Alto Networks Inc.
15.1.1 Company Profile
15.1.2 Main Business and Network Security Information
15.1.3 SWOT Analysis of Palo Alto Networks Inc.
15.1.4 Palo Alto Networks Inc. Network Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.2 Cisco Systems Inc.
15.2.1 Company Profile
15.2.2 Main Business and Network Security Information
15.2.3 SWOT Analysis of Cisco Systems Inc.
15.2.4 Cisco Systems Inc. Network Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.3 Fortinet Inc.
15.3.1 Company Profile
15.3.2 Main Business and Network Security Information
15.3.3 SWOT Analysis of Fortinet Inc.
15.3.4 Fortinet Inc. Network Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.4 Check Point Software Technologies
15.4.1 Company Profile
15.4.2 Main Business and Network Security Information
15.4.3 SWOT Analysis of Check Point Software Technologies
15.4.4 Check Point Software Technologies Network Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.5 Juniper Networks
15.5.1 Company Profile
15.5.2 Main Business and Network Security Information
15.5.3 SWOT Analysis of Juniper Networks
15.5.4 Juniper Networks Network Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.6 CrowdStrike Holdings
15.6.1 Company Profile
15.6.2 Main Business and Network Security Information
15.6.3 SWOT Analysis of CrowdStrike Holdings
15.6.4 CrowdStrike Holdings Network Security Sales, Revenue, Price and Gross Margin (2021-2026)
Please ask for sample pages for full companies list
Table Research Scope of Network Security Report
Table Data Sources of Network Security Report
Table Major Assumptions of Network Security Report
Table Network Security Classification
Table Network Security Applications
Table Drivers of Network Security Market
Table Restraints of Network Security Market
Table Opportunities of Network Security Market
Table Threats of Network Security Market
Table Raw Materials Suppliers
Table Different Production Methods of Network Security
Table Cost Structure Analysis of Network Security
Table Key End Users
Table Latest News of Network Security Market
Table Merger and Acquisition
Table Planned/Future Project of Network Security Market
Table Policy of Network Security Market
Table 2021-2031 North America Network Security Market Size
Table 2021-2031 North America Network Security Market Size by Application
Table 2021-2026 North America Network Security Key Players Revenue
Table 2021-2026 North America Network Security Key Players Market Share
Table 2021-2031 North America Network Security Market Size by Type
Table 2021-2031 United States Network Security Market Size
Table 2021-2031 Canada Network Security Market Size
Table 2021-2031 Mexico Network Security Market Size
Table 2021-2031 South America Network Security Market Size
Table 2021-2031 South America Network Security Market Size by Application
Table 2021-2026 South America Network Security Key Players Revenue
Table 2021-2026 South America Network Security Key Players Market Share
Table 2021-2031 South America Network Security Market Size by Type
Table 2021-2031 Brazil Network Security Market Size
Table 2021-2031 Argentina Network Security Market Size
Table 2021-2031 Chile Network Security Market Size
Table 2021-2031 Peru Network Security Market Size
Table 2021-2031 Asia & Pacific Network Security Market Size
Table 2021-2031 Asia & Pacific Network Security Market Size by Application
Table 2021-2026 Asia & Pacific Network Security Key Players Revenue
Table 2021-2026 Asia & Pacific Network Security Key Players Market Share
Table 2021-2031 Asia & Pacific Network Security Market Size by Type
Table 2021-2031 China Network Security Market Size
Table 2021-2031 India Network Security Market Size
Table 2021-2031 Japan Network Security Market Size
Table 2021-2031 South Korea Network Security Market Size
Table 2021-2031 Southeast Asia Network Security Market Size
Table 2021-2031 Australia Network Security Market Size
Table 2021-2031 Europe Network Security Market Size
Table 2021-2031 Europe Network Security Market Size by Application
Table 2021-2026 Europe Network Security Key Players Revenue
Table 2021-2026 Europe Network Security Key Players Market Share
Table 2021-2031 Europe Network Security Market Size by Type
Table 2021-2031 Germany Network Security Market Size
Table 2021-2031 France Network Security Market Size
Table 2021-2031 United Kingdom Network Security Market Size
Table 2021-2031 Italy Network Security Market Size
Table 2021-2031 Spain Network Security Market Size
Table 2021-2031 Belgium Network Security Market Size
Table 2021-2031 Netherlands Network Security Market Size
Table 2021-2031 Austria Network Security Market Size
Table 2021-2031 Poland Network Security Market Size
Table 2021-2031 Russia Network Security Market Size
Table 2021-2031 MEA Network Security Market Size
Table 2021-2031 MEA Network Security Market Size by Application
Table 2021-2026 MEA Network Security Key Players Revenue
Table 2021-2026 MEA Network Security Key Players Market Share
Table 2021-2031 MEA Network Security Market Size by Type
Table 2021-2031 Egypt Network Security Market Size
Table 2021-2031 Israel Network Security Market Size
Table 2021-2031 South Africa Network Security Market Size
Table 2021-2031 Gulf Cooperation Council Countries Network Security Market Size
Table 2021-2031 Turkey Network Security Market Size
Table 2021-2026 Global Network Security Market Size by Region
Table 2021-2026 Global Network Security Market Size Share by Region
Table 2021-2026 Global Network Security Market Size by Application
Table 2021-2026 Global Network Security Market Share by Application
Table 2021-2026 Global Network Security Key Vendors Revenue
Table 2021-2026 Global Network Security Key Vendors Market Share
Table 2021-2026 Global Network Security Market Size by Type
Table 2021-2026 Global Network Security Market Share by Type
Table 2026-2031 Global Network Security Market Size by Region
Table 2026-2031 Global Network Security Market Size Share by Region
Table 2026-2031 Global Network Security Market Size by Application
Table 2026-2031 Global Network Security Market Share by Application
Table 2026-2031 Global Network Security Key Vendors Revenue
Table 2026-2031 Global Network Security Key Vendors Market Share
Table 2026-2031 Global Network Security Market Size by Type
Table 2026-2031 Network Security Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Network Security Picture
Figure 2021-2031 North America Network Security Market Size and CAGR
Figure 2021-2031 South America Network Security Market Size and CAGR
Figure 2021-2031 Asia & Pacific Network Security Market Size and CAGR
Figure 2021-2031 Europe Network Security Market Size and CAGR
Figure 2021-2031 MEA Network Security Market Size and CAGR
Figure 2021-2026 Global Network Security Market Size and Growth Rate
Figure 2026-2031 Global Network Security Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
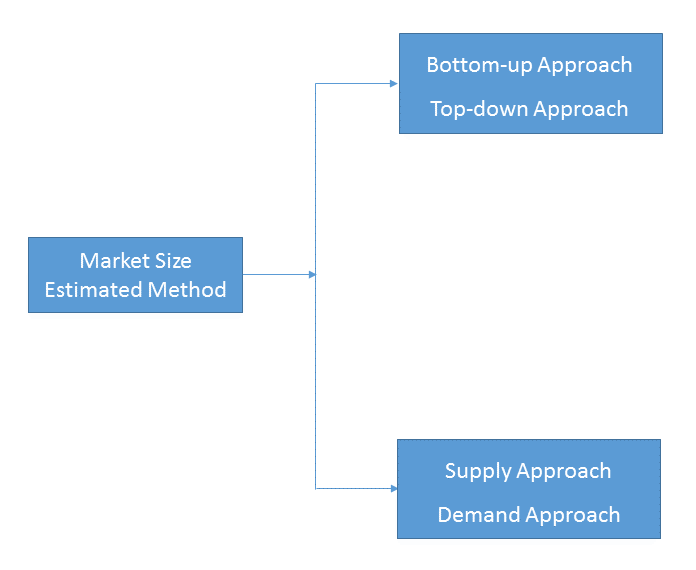
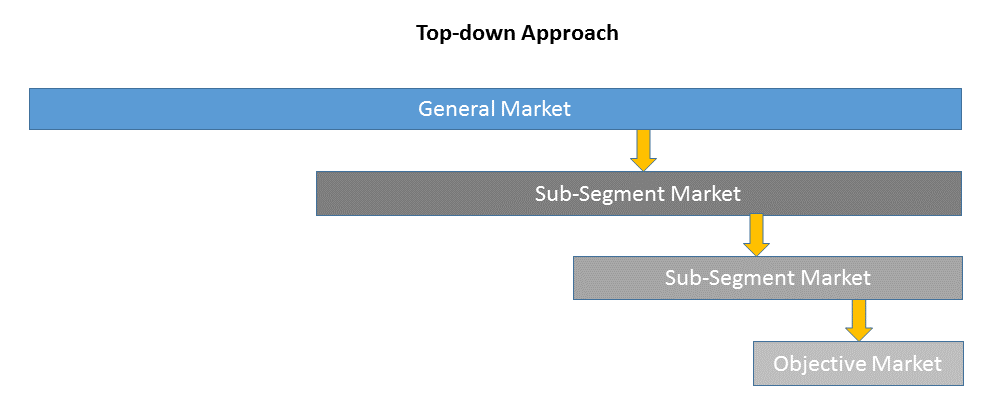
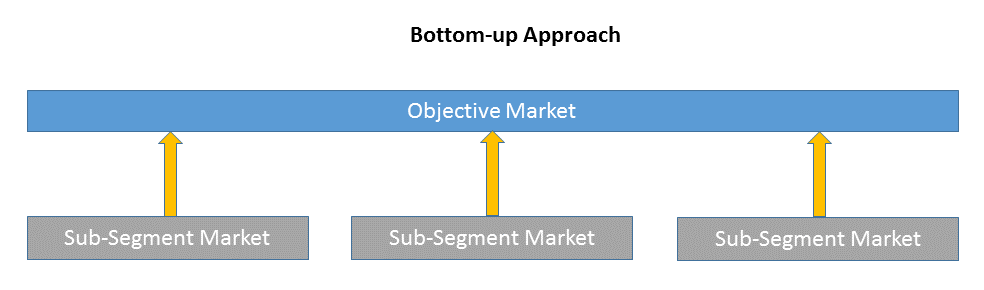
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
Bottom-up approach size the objective market by collecting the sub-segment information.
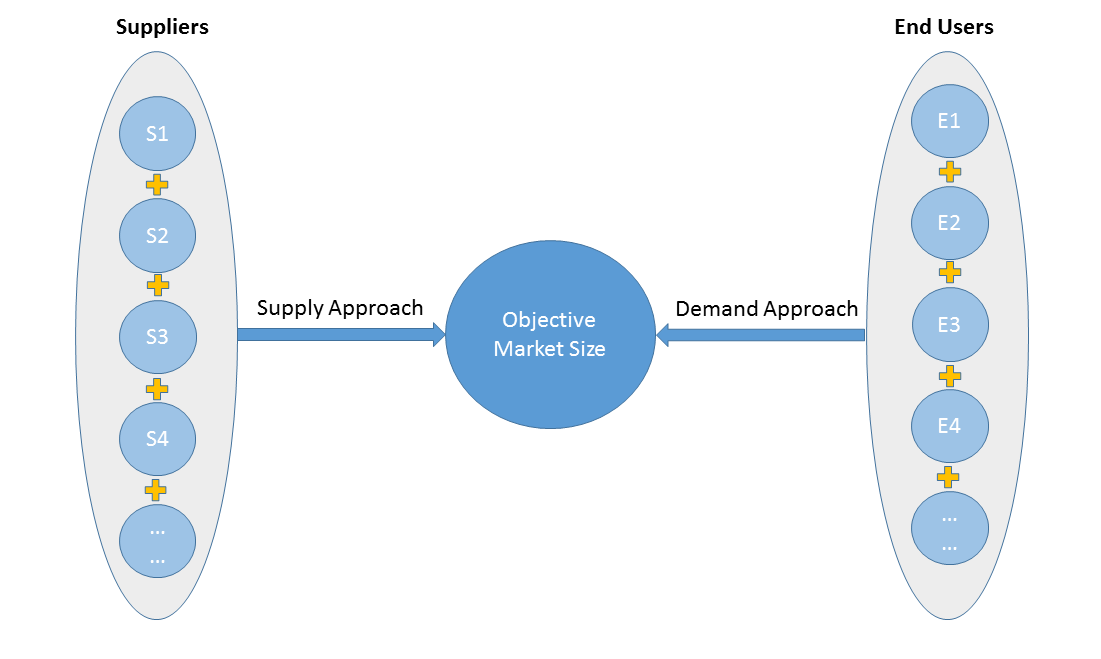
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
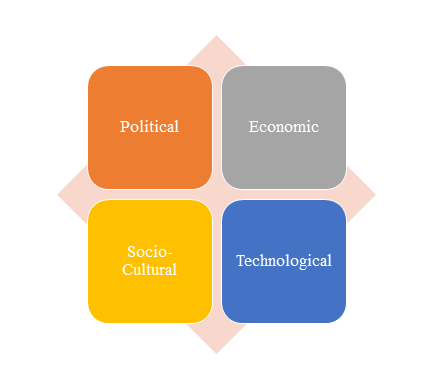
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
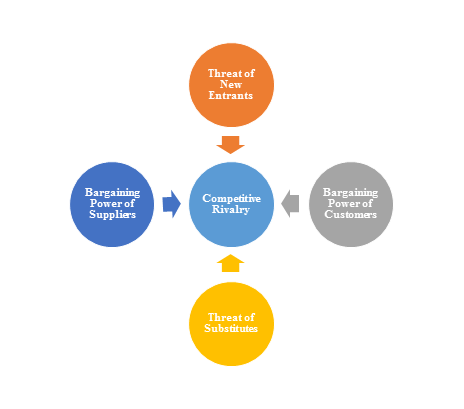
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
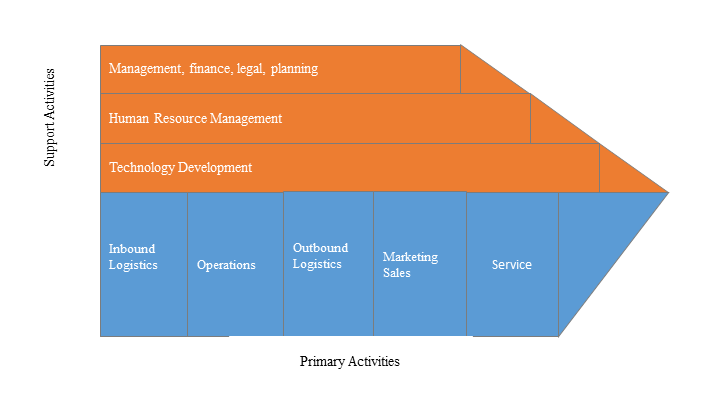
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
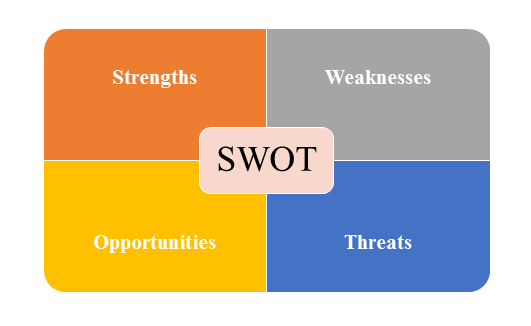
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |