Identity and Access Management (IAM) Market Insights 2026, Analysis and Forecast to 2031
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
Industry Characteristics and Technological Landscape
Identity and Access Management (IAM) has evolved into the cornerstone of modern cybersecurity, transitioning from a back-office administrative function to a strategic business enabler. As organizations embrace digital transformation, cloud migration, and decentralized work environments, the traditional network perimeter has effectively dissolved, leaving "identity" as the new perimeter. The IAM industry encompasses the framework of policies, technologies, and processes that ensure the right individuals access the right resources at the right time and for the right reasons.
The current industry landscape is defined by the rapid adoption of Zero Trust Architecture (ZTA). Unlike legacy models that assumed trust for anyone inside the network, modern IAM systems operate on the principle of "never trust, always verify." This shift has catalyzed the development of sophisticated technologies such as Multi-Factor Authentication (MFA), Single Sign-On (SSO), Identity Governance and Administration (IGA), and Privileged Access Management (PAM). Furthermore, the integration of Artificial Intelligence (AI) and Machine Learning (ML) is enabling "identity analytics," where systems can detect anomalous behavior and automatically trigger step-up authentication or block access in real-time.
Based on insights derived from global cybersecurity spending reports, cloud infrastructure benchmarks, and strategic analysis from leading management consultancies and industry bodies, the global market for Identity and Access Management is estimated to reach between USD 10.0 billion and USD 30.0 billion by 2026. The market is projected to expand at a Compound Annual Growth Rate (CAGR) of approximately 5.0% to 15.0% throughout the forecast period. This steady growth is fueled by the rising frequency of identity-based cyberattacks, such as phishing and credential stuffing, alongside increasingly stringent global data protection regulations.
Market Segmentation by Type
The IAM market is categorized into distinct types based on the user group and the specific security requirements of the interaction.
Workforce IAM is the most established segment, with an estimated growth range of 4.5% to 12.5%. This segment focuses on managing the identities of employees, contractors, and internal partners. The primary drivers here are the continued support for hybrid work models and the need to streamline employee onboarding and offboarding. Automation in this segment reduces the risk of "orphan accounts"—active credentials belonging to former employees—which are a primary target for attackers.
Consumer IAM (CIAM) is currently the fastest-growing segment, projected to increase at a CAGR of 7.0% to 16.0%. Unlike internal systems, CIAM must balance high-level security with a seamless, frictionless user experience. It is essential for B2C organizations in retail, banking, and media that need to secure millions of customer identities while gaining insights into user behavior to personalize services. CIAM solutions often include features like social login, self-service registration, and preference management.
B2B IAM is an emerging segment with a projected growth range of 6.0% to 14.5%. This type facilitates secure collaboration between organizations, allowing businesses to grant external partners, suppliers, or distributors access to specific internal applications without compromising the entire network. As global supply chains become more digitally integrated, the ability to manage federated identities across organizational boundaries has become critical.
Regional Market Trends
The demand for IAM solutions is global, yet regional market dynamics are shaped by local regulatory environments and the maturity of cloud adoption.
North America remains the dominant region, with growth estimated in the range of 4.5% to 13.5%. The market is driven by a high concentration of large enterprises, early adoption of cloud-first strategies, and strict regulations such as the California Consumer Privacy Act (CCPA) and various federal cybersecurity mandates. The region is also the primary hub for IAM innovation, hosting many of the world's leading cybersecurity vendors.
Europe represents a significant and highly regulated market, with projected growth between 5.0% and 14.0%. The implementation of the General Data Protection Regulation (GDPR) has made IAM an essential tool for compliance, as organizations must demonstrate strict control over who can access personal data. Additionally, the revised Payment Services Directive (PSD2) in the financial sector has accelerated the adoption of strong customer authentication (SCA) across the continent.
The Asia-Pacific (APAC) region is expected to exhibit the highest growth potential, with a CAGR range of 7.5% to 17.5%. Rapid digitalization in India, China, and Southeast Asia, combined with an increasing number of mobile-first consumers, is driving massive investments in CIAM. Furthermore, as regional businesses expand internationally, they are increasingly adopting global identity standards to facilitate secure cross-border trade and communication.
Latin America is a developing market with growth projected between 4.0% and 12.0%. Growth is primarily concentrated in Brazil and Mexico, where the financial services and retail sectors are investing in MFA and SSO to combat rising rates of online fraud and to comply with emerging local data protection laws.
The Middle East and Africa (MEA) region is estimated to grow at a range of 5.5% to 14.5%. Government-led digital transformation initiatives, such as Saudi Vision 2030 and digital identification projects in various African nations, are creating significant opportunities for IAM providers to establish foundational identity infrastructures.
Application Analysis by Vertical
IAM solutions are utilized across diverse industries, with each sector presenting unique challenges and growth rates.
Banking, Financial Services, and Insurance (BFSI) is the leading consumer of IAM, with growth estimated at 6.0% to 15.0%. The sector's high-risk profile makes it an early adopter of advanced biometrics and behavioral analytics to prevent fraud and satisfy rigorous audit requirements.
Healthcare is a high-growth vertical, projected at 7.0% to 16.5%. With the rise of telehealth and the digitization of patient records, protecting sensitive health information (PHI) is paramount. IAM systems here focus on ensuring that only authorized clinical staff can access specific patient data, often requiring specialized integrations with Electronic Health Record (EHR) systems.
IT and ITeS, as well as Retail & E-commerce, are expected to grow at 5.5% to 14.5% and 6.5% to 15.5% respectively. For IT companies, the focus is on managing privileged access for developers and admins, while retail focuses on securing the customer journey and preventing account takeovers (ATO).
Other verticals, including Government & Defense, Education, and Tourism & Hospitality, show growth ranges between 4.5% and 13.0%. Government sectors are particularly focused on sovereign identity and secure citizen portals, while the education sector deals with the complexities of managing identities for transient student populations.
Company Landscape
The IAM market features a diverse array of players, ranging from diversified software conglomerates to specialized security "pure-plays."
Enterprise Software Leaders:
Microsoft, IBM, Oracle, and SAP provide comprehensive identity suites that are often integrated into their broader cloud ecosystems. Microsoft’s Entra ID (formerly Azure AD) is a dominant force in the workforce market due to its deep integration with Office 365. Oracle and IBM cater primarily to large-scale legacy environments that require complex on-premises and hybrid deployments.
Identity Specialists and Pure-Plays:
Okta and Ping Identity are recognized as leaders in modern, cloud-native IAM. Okta’s focus on ease of use and a vast integration library has made it a favorite for both Workforce and CIAM (following its acquisition of Auth0). Ping Identity specializes in high-scale, complex enterprise requirements, often in the financial sector.
Governance and Privileged Access Experts:
SailPoint and Saviynt lead the Identity Governance and Administration (IGA) space, focusing on the "compliance" side of identity—managing the lifecycle and auditing access rights. CyberArk and Delinea are the primary leaders in Privileged Access Management (PAM), securing the "keys to the kingdom" by managing high-level administrative credentials.
Security and Access Providers:
Thales, Akamai Technologies, and Cisco (via Duo Security) focus on the access and authentication layer. Thales is a leader in hardware-based security and encryption, while Duo Security revolutionized the MFA market with its user-friendly mobile push notifications. Akamai has successfully pivoted from content delivery to security, offering robust CIAM and Zero Trust access solutions.
Emerging and Specialized Innovators:
Companies like Beyond Identity and Trusona are pushing the boundaries of "passwordless" authentication. IDnow and Signzy focus on the identity verification and "Know Your Customer" (KYC) aspects, particularly critical for the BFSI sector. Other players like 1Password (via Trelica) and Rippling are blurring the lines between password management, HRIS, and IAM to provide all-in-one solutions for mid-market companies.
Industry Value Chain Analysis
The IAM value chain is a multi-layered ecosystem that ensures the secure flow of identity data from creation to consumption.
Upstream: Technology and Infrastructure:
This stage involves the providers of cloud infrastructure (AWS, Azure, Google Cloud) and the developers of specialized hardware, such as biometric scanners and security keys (HID Global, Yubico). This layer also includes the providers of threat intelligence data used to inform identity risk scores.
Midstream: IAM Platform Development:
This is the core of the value chain, where software vendors (like Okta, SailPoint, or CyberArk) develop the logic, APIs, and management consoles. These platforms act as the "brains" of the operation, orchestrating authentication, authorization, and audit logs across thousands of downstream applications.
Distribution and Implementation:
The market relies heavily on a network of Global System Integrators (GSIs) and specialized cybersecurity consultants (such as Deloitte, Accenture, and Traxion). These partners are critical for large-scale enterprises that require custom integrations between their IAM platforms and legacy on-premises applications.
Downstream: End-User Consumption and Operations:
The final stage is the operational use of the system by the end-client. This includes the internal IT security teams who manage the policies, and the end-users (employees or customers) who interact with the authentication interfaces. In many cases, this is managed by Managed Security Service Providers (MSSPs) who operate the IAM system on behalf of the client.
Market Opportunities and Challenges
Opportunities:
Passwordless Future: The move toward FIDO2 standards and biometric-based authentication presents a significant opportunity to eliminate the primary vulnerability in security: the human-generated password.
Identity for Machines (Non-Human Identities): As IoT and microservices architectures proliferate, there is a massive untapped market for managing the "identities" of bots, service accounts, and connected devices, which now outnumber human users.
Decentralized Identity (SSI): Self-Sovereign Identity and blockchain-based credentials offer a path toward user-owned data, potentially revolutionizing how CIAM operates by giving consumers control over their personal information.
Challenges:
Complexity and Legacy Systems: Many enterprises struggle with "identity silos" where different departments use different systems. Integrating modern cloud IAM with 20-year-old on-premises applications remains a significant technical and financial hurdle.
The Cybersecurity Talent Gap: There is a global shortage of cybersecurity professionals who specialize in identity architecture, which can slow down deployment and lead to misconfigurations.
Sophisticated Social Engineering: As technical barriers like MFA become standard, attackers are increasingly targeting the human element through AI-powered deepfakes and sophisticated social engineering, requiring IAM systems to incorporate more advanced behavioral signals.
User Friction vs. Security: Finding the perfect balance between a secure login process and a frictionless experience remains a constant challenge, particularly in the competitive e-commerce landscape where any delay can lead to cart abandonment.
The Identity and Access Management market is characterized by its vital necessity in a cloud-first world. As identity remains the most targeted vector for cyberattacks, the industry will continue to see robust innovation and consolidation as players strive to provide a unified, secure, and user-friendly identity fabric for the global digital economy.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Identity and Access Management (IAM) Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Identity and Access Management (IAM) Market in North America (2021-2031)
8.1 Identity and Access Management (IAM) Market Size
8.2 Identity and Access Management (IAM) Market by End Use
8.3 Competition by Players/Suppliers
8.4 Identity and Access Management (IAM) Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Identity and Access Management (IAM) Market in South America (2021-2031)
9.1 Identity and Access Management (IAM) Market Size
9.2 Identity and Access Management (IAM) Market by End Use
9.3 Competition by Players/Suppliers
9.4 Identity and Access Management (IAM) Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Identity and Access Management (IAM) Market in Asia & Pacific (2021-2031)
10.1 Identity and Access Management (IAM) Market Size
10.2 Identity and Access Management (IAM) Market by End Use
10.3 Competition by Players/Suppliers
10.4 Identity and Access Management (IAM) Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Identity and Access Management (IAM) Market in Europe (2021-2031)
11.1 Identity and Access Management (IAM) Market Size
11.2 Identity and Access Management (IAM) Market by End Use
11.3 Competition by Players/Suppliers
11.4 Identity and Access Management (IAM) Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Identity and Access Management (IAM) Market in MEA (2021-2031)
12.1 Identity and Access Management (IAM) Market Size
12.2 Identity and Access Management (IAM) Market by End Use
12.3 Competition by Players/Suppliers
12.4 Identity and Access Management (IAM) Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Identity and Access Management (IAM) Market (2021-2026)
13.1 Identity and Access Management (IAM) Market Size
13.2 Identity and Access Management (IAM) Market by End Use
13.3 Competition by Players/Suppliers
13.4 Identity and Access Management (IAM) Market Size by Type
Chapter 14 Global Identity and Access Management (IAM) Market Forecast (2026-2031)
14.1 Identity and Access Management (IAM) Market Size Forecast
14.2 Identity and Access Management (IAM) Application Forecast
14.3 Competition by Players/Suppliers
14.4 Identity and Access Management (IAM) Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Microsoft
15.1.1 Company Profile
15.1.2 Main Business and Identity and Access Management (IAM) Information
15.1.3 SWOT Analysis of Microsoft
15.1.4 Microsoft Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.2 Okta
15.2.1 Company Profile
15.2.2 Main Business and Identity and Access Management (IAM) Information
15.2.3 SWOT Analysis of Okta
15.2.4 Okta Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.3 Ping Identity
15.3.1 Company Profile
15.3.2 Main Business and Identity and Access Management (IAM) Information
15.3.3 SWOT Analysis of Ping Identity
15.3.4 Ping Identity Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.4 CyberArk
15.4.1 Company Profile
15.4.2 Main Business and Identity and Access Management (IAM) Information
15.4.3 SWOT Analysis of CyberArk
15.4.4 CyberArk Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.5 SailPoint
15.5.1 Company Profile
15.5.2 Main Business and Identity and Access Management (IAM) Information
15.5.3 SWOT Analysis of SailPoint
15.5.4 SailPoint Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.6 Oracle
15.6.1 Company Profile
15.6.2 Main Business and Identity and Access Management (IAM) Information
15.6.3 SWOT Analysis of Oracle
15.6.4 Oracle Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.7 IBM
15.7.1 Company Profile
15.7.2 Main Business and Identity and Access Management (IAM) Information
15.7.3 SWOT Analysis of IBM
15.7.4 IBM Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.8 One Identity
15.8.1 Company Profile
15.8.2 Main Business and Identity and Access Management (IAM) Information
15.8.3 SWOT Analysis of One Identity
15.8.4 One Identity Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.9 Saviynt
15.9.1 Company Profile
15.9.2 Main Business and Identity and Access Management (IAM) Information
15.9.3 SWOT Analysis of Saviynt
15.9.4 Saviynt Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.10 Thales
15.10.1 Company Profile
15.10.2 Main Business and Identity and Access Management (IAM) Information
15.10.3 SWOT Analysis of Thales
15.10.4 Thales Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.11 Akamai Technologies
15.11.1 Company Profile
15.11.2 Main Business and Identity and Access Management (IAM) Information
15.11.3 SWOT Analysis of Akamai Technologies
15.11.4 Akamai Technologies Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.12 OpenText
15.12.1 Company Profile
15.12.2 Main Business and Identity and Access Management (IAM) Information
15.12.3 SWOT Analysis of OpenText
15.12.4 OpenText Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.13 Entrust
15.13.1 Company Profile
15.13.2 Main Business and Identity and Access Management (IAM) Information
15.13.3 SWOT Analysis of Entrust
15.13.4 Entrust Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.14 Duo Security
15.14.1 Company Profile
15.14.2 Main Business and Identity and Access Management (IAM) Information
15.14.3 SWOT Analysis of Duo Security
15.14.4 Duo Security Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.15 HID Global
15.15.1 Company Profile
15.15.2 Main Business and Identity and Access Management (IAM) Information
15.15.3 SWOT Analysis of HID Global
15.15.4 HID Global Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.16 Evidian
15.16.1 Company Profile
15.16.2 Main Business and Identity and Access Management (IAM) Information
15.16.3 SWOT Analysis of Evidian
15.16.4 Evidian Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.17 RSA Security
15.17.1 Company Profile
15.17.2 Main Business and Identity and Access Management (IAM) Information
15.17.3 SWOT Analysis of RSA Security
15.17.4 RSA Security Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.18 Avatier
15.18.1 Company Profile
15.18.2 Main Business and Identity and Access Management (IAM) Information
15.18.3 SWOT Analysis of Avatier
15.18.4 Avatier Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.19 ManageEngine
15.19.1 Company Profile
15.19.2 Main Business and Identity and Access Management (IAM) Information
15.19.3 SWOT Analysis of ManageEngine
15.19.4 ManageEngine Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.20 SecureAuth
15.20.1 Company Profile
15.20.2 Main Business and Identity and Access Management (IAM) Information
15.20.3 SWOT Analysis of SecureAuth
15.20.4 SecureAuth Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.21 EmpowerID
15.21.1 Company Profile
15.21.2 Main Business and Identity and Access Management (IAM) Information
15.21.3 SWOT Analysis of EmpowerID
15.21.4 EmpowerID Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.22 Simeio
15.22.1 Company Profile
15.22.2 Main Business and Identity and Access Management (IAM) Information
15.22.3 SWOT Analysis of Simeio
15.22.4 Simeio Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.23 FusionAuth
15.23.1 Company Profile
15.23.2 Main Business and Identity and Access Management (IAM) Information
15.23.3 SWOT Analysis of FusionAuth
15.23.4 FusionAuth Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.24 Auth0
15.24.1 Company Profile
15.24.2 Main Business and Identity and Access Management (IAM) Information
15.24.3 SWOT Analysis of Auth0
15.24.4 Auth0 Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.25 IDnow
15.25.1 Company Profile
15.25.2 Main Business and Identity and Access Management (IAM) Information
15.25.3 SWOT Analysis of IDnow
15.25.4 IDnow Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.26 Zuora
15.26.1 Company Profile
15.26.2 Main Business and Identity and Access Management (IAM) Information
15.26.3 SWOT Analysis of Zuora
15.26.4 Zuora Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.27 Signzy
15.27.1 Company Profile
15.27.2 Main Business and Identity and Access Management (IAM) Information
15.27.3 SWOT Analysis of Signzy
15.27.4 Signzy Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.28 Civic Technologies
15.28.1 Company Profile
15.28.2 Main Business and Identity and Access Management (IAM) Information
15.28.3 SWOT Analysis of Civic Technologies
15.28.4 Civic Technologies Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.29 Trusona
15.29.1 Company Profile
15.29.2 Main Business and Identity and Access Management (IAM) Information
15.29.3 SWOT Analysis of Trusona
15.29.4 Trusona Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
15.30 Beyond Identity
15.30.1 Company Profile
15.30.2 Main Business and Identity and Access Management (IAM) Information
15.30.3 SWOT Analysis of Beyond Identity
15.30.4 Beyond Identity Identity and Access Management (IAM) Sales, Revenue, Price and Gross Margin (2021-2026)
Please ask for sample pages for full companies list
Table Research Scope of Identity and Access Management (IAM) Report
Table Data Sources of Identity and Access Management (IAM) Report
Table Major Assumptions of Identity and Access Management (IAM) Report
Table Identity and Access Management (IAM) Classification
Table Identity and Access Management (IAM) Applications
Table Drivers of Identity and Access Management (IAM) Market
Table Restraints of Identity and Access Management (IAM) Market
Table Opportunities of Identity and Access Management (IAM) Market
Table Threats of Identity and Access Management (IAM) Market
Table Raw Materials Suppliers
Table Different Production Methods of Identity and Access Management (IAM)
Table Cost Structure Analysis of Identity and Access Management (IAM)
Table Key End Users
Table Latest News of Identity and Access Management (IAM) Market
Table Merger and Acquisition
Table Planned/Future Project of Identity and Access Management (IAM) Market
Table Policy of Identity and Access Management (IAM) Market
Table 2021-2031 North America Identity and Access Management (IAM) Market Size
Table 2021-2031 North America Identity and Access Management (IAM) Market Size by Application
Table 2021-2026 North America Identity and Access Management (IAM) Key Players Revenue
Table 2021-2026 North America Identity and Access Management (IAM) Key Players Market Share
Table 2021-2031 North America Identity and Access Management (IAM) Market Size by Type
Table 2021-2031 United States Identity and Access Management (IAM) Market Size
Table 2021-2031 Canada Identity and Access Management (IAM) Market Size
Table 2021-2031 Mexico Identity and Access Management (IAM) Market Size
Table 2021-2031 South America Identity and Access Management (IAM) Market Size
Table 2021-2031 South America Identity and Access Management (IAM) Market Size by Application
Table 2021-2026 South America Identity and Access Management (IAM) Key Players Revenue
Table 2021-2026 South America Identity and Access Management (IAM) Key Players Market Share
Table 2021-2031 South America Identity and Access Management (IAM) Market Size by Type
Table 2021-2031 Brazil Identity and Access Management (IAM) Market Size
Table 2021-2031 Argentina Identity and Access Management (IAM) Market Size
Table 2021-2031 Chile Identity and Access Management (IAM) Market Size
Table 2021-2031 Peru Identity and Access Management (IAM) Market Size
Table 2021-2031 Asia & Pacific Identity and Access Management (IAM) Market Size
Table 2021-2031 Asia & Pacific Identity and Access Management (IAM) Market Size by Application
Table 2021-2026 Asia & Pacific Identity and Access Management (IAM) Key Players Revenue
Table 2021-2026 Asia & Pacific Identity and Access Management (IAM) Key Players Market Share
Table 2021-2031 Asia & Pacific Identity and Access Management (IAM) Market Size by Type
Table 2021-2031 China Identity and Access Management (IAM) Market Size
Table 2021-2031 India Identity and Access Management (IAM) Market Size
Table 2021-2031 Japan Identity and Access Management (IAM) Market Size
Table 2021-2031 South Korea Identity and Access Management (IAM) Market Size
Table 2021-2031 Southeast Asia Identity and Access Management (IAM) Market Size
Table 2021-2031 Australia Identity and Access Management (IAM) Market Size
Table 2021-2031 Europe Identity and Access Management (IAM) Market Size
Table 2021-2031 Europe Identity and Access Management (IAM) Market Size by Application
Table 2021-2026 Europe Identity and Access Management (IAM) Key Players Revenue
Table 2021-2026 Europe Identity and Access Management (IAM) Key Players Market Share
Table 2021-2031 Europe Identity and Access Management (IAM) Market Size by Type
Table 2021-2031 Germany Identity and Access Management (IAM) Market Size
Table 2021-2031 France Identity and Access Management (IAM) Market Size
Table 2021-2031 United Kingdom Identity and Access Management (IAM) Market Size
Table 2021-2031 Italy Identity and Access Management (IAM) Market Size
Table 2021-2031 Spain Identity and Access Management (IAM) Market Size
Table 2021-2031 Belgium Identity and Access Management (IAM) Market Size
Table 2021-2031 Netherlands Identity and Access Management (IAM) Market Size
Table 2021-2031 Austria Identity and Access Management (IAM) Market Size
Table 2021-2031 Poland Identity and Access Management (IAM) Market Size
Table 2021-2031 Russia Identity and Access Management (IAM) Market Size
Table 2021-2031 MEA Identity and Access Management (IAM) Market Size
Table 2021-2031 MEA Identity and Access Management (IAM) Market Size by Application
Table 2021-2026 MEA Identity and Access Management (IAM) Key Players Revenue
Table 2021-2026 MEA Identity and Access Management (IAM) Key Players Market Share
Table 2021-2031 MEA Identity and Access Management (IAM) Market Size by Type
Table 2021-2031 Egypt Identity and Access Management (IAM) Market Size
Table 2021-2031 Israel Identity and Access Management (IAM) Market Size
Table 2021-2031 South Africa Identity and Access Management (IAM) Market Size
Table 2021-2031 Gulf Cooperation Council Countries Identity and Access Management (IAM) Market Size
Table 2021-2031 Turkey Identity and Access Management (IAM) Market Size
Table 2021-2026 Global Identity and Access Management (IAM) Market Size by Region
Table 2021-2026 Global Identity and Access Management (IAM) Market Size Share by Region
Table 2021-2026 Global Identity and Access Management (IAM) Market Size by Application
Table 2021-2026 Global Identity and Access Management (IAM) Market Share by Application
Table 2021-2026 Global Identity and Access Management (IAM) Key Vendors Revenue
Table 2021-2026 Global Identity and Access Management (IAM) Key Vendors Market Share
Table 2021-2026 Global Identity and Access Management (IAM) Market Size by Type
Table 2021-2026 Global Identity and Access Management (IAM) Market Share by Type
Table 2026-2031 Global Identity and Access Management (IAM) Market Size by Region
Table 2026-2031 Global Identity and Access Management (IAM) Market Size Share by Region
Table 2026-2031 Global Identity and Access Management (IAM) Market Size by Application
Table 2026-2031 Global Identity and Access Management (IAM) Market Share by Application
Table 2026-2031 Global Identity and Access Management (IAM) Key Vendors Revenue
Table 2026-2031 Global Identity and Access Management (IAM) Key Vendors Market Share
Table 2026-2031 Global Identity and Access Management (IAM) Market Size by Type
Table 2026-2031 Identity and Access Management (IAM) Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Identity and Access Management (IAM) Picture
Figure 2021-2031 North America Identity and Access Management (IAM) Market Size and CAGR
Figure 2021-2031 South America Identity and Access Management (IAM) Market Size and CAGR
Figure 2021-2031 Asia & Pacific Identity and Access Management (IAM) Market Size and CAGR
Figure 2021-2031 Europe Identity and Access Management (IAM) Market Size and CAGR
Figure 2021-2031 MEA Identity and Access Management (IAM) Market Size and CAGR
Figure 2021-2026 Global Identity and Access Management (IAM) Market Size and Growth Rate
Figure 2026-2031 Global Identity and Access Management (IAM) Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
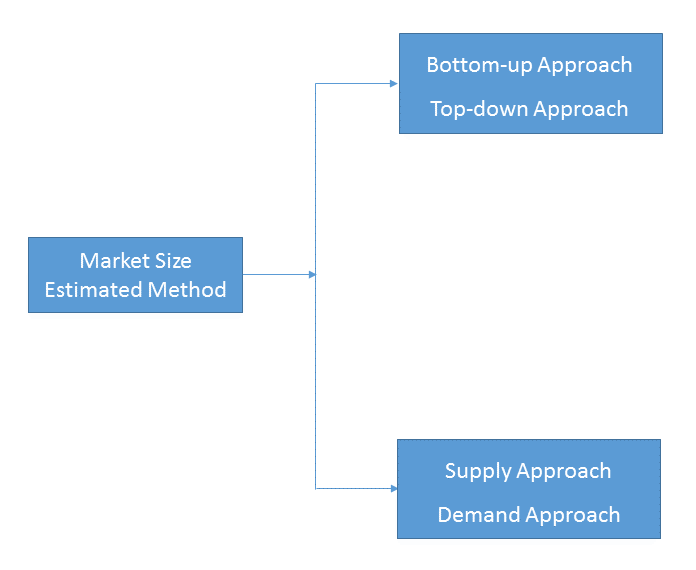
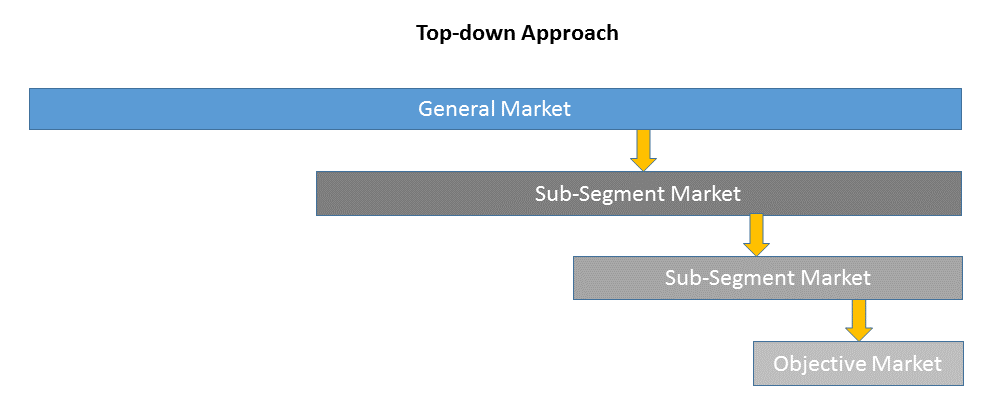
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
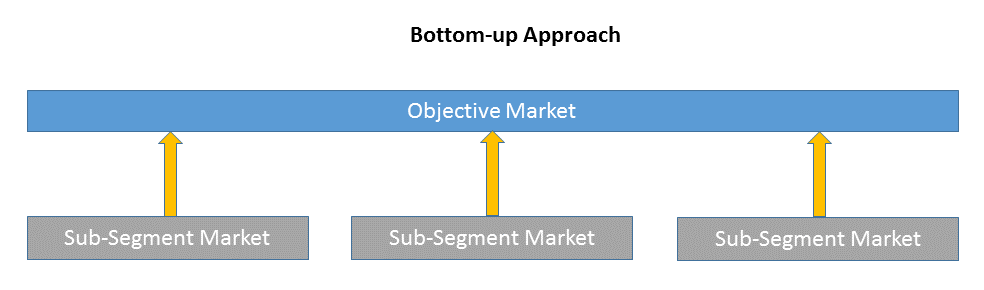
Bottom-up approach size the objective market by collecting the sub-segment information.
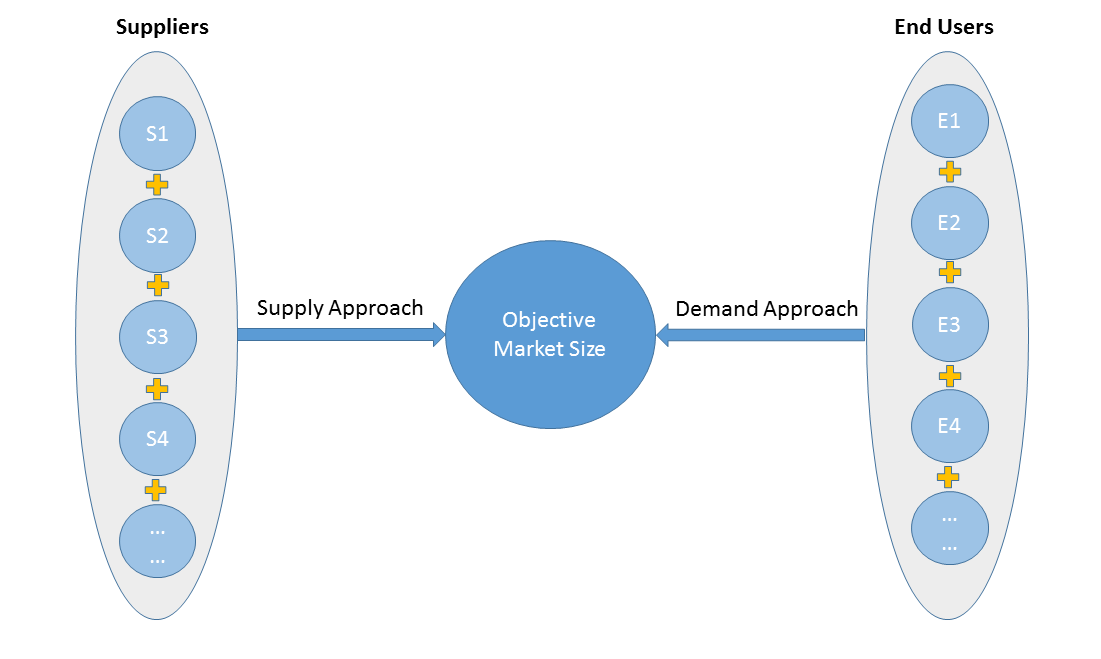
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
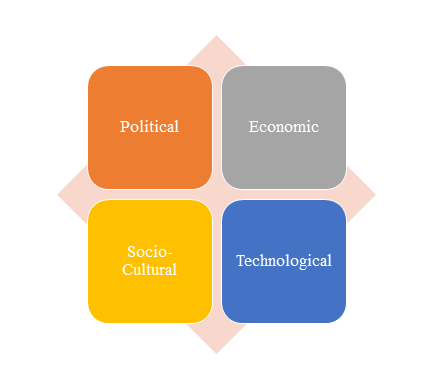
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
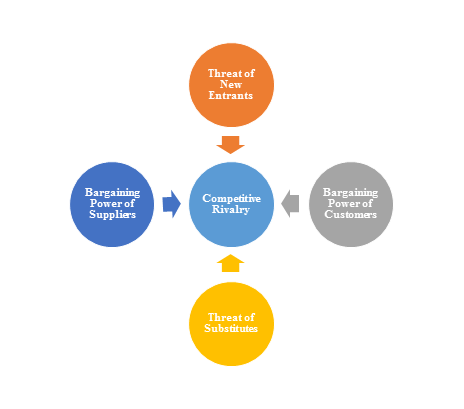
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
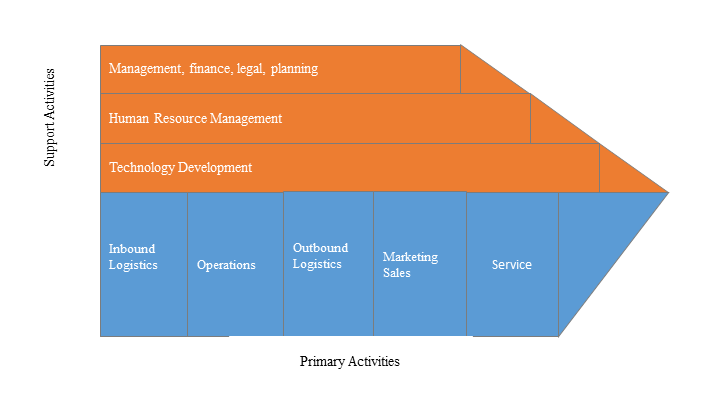
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
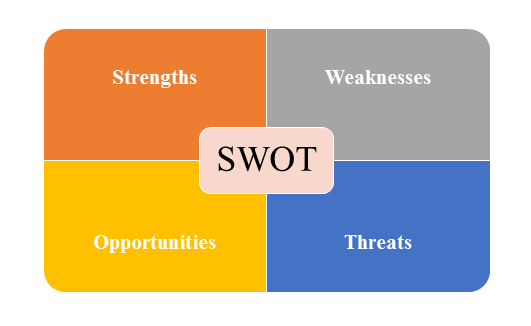
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |