Connected Car Security Market Insights 2026, Analysis and Forecast to 2031
- Single User License (1 Users) $ 3,500
- Team License (2~5 Users) $ 4,500
- Corporate License (>5 Users) $ 5,500
The Connected Car Security market represents one of the most critical frontiers in the modern automotive and cybersecurity landscape. As vehicles transition into "software-defined vehicles" (SDVs), they essentially become mobile data centers, integrating over 100 million lines of code and numerous Electronic Control Units (ECUs). This evolution, while enhancing driver experience through advanced telematics and autonomous capabilities, significantly expands the cyber-attack surface. The market is defined by a shift from reactive hardware-centric safety to proactive, software-driven security frameworks designed to protect against remote hacking, data breaches, and system manipulation.
Driven by stringent global regulations—such as UN R155/R156 and ISO/SAE 21434—and the mass adoption of 5G-enabled V2X (Vehicle-to-Everything) communication, the global Connected Car Security market is estimated to reach a valuation of approximately USD 2.0–5.0 billion in 2025. This specialized sector is projected to experience robust growth, with a compound annual growth rate (CAGR) ranging between 6.0%–15.0% through 2030. The disparity in growth rates often reflects the varying pace of legislative enforcement and the speed of transition from internal combustion engines to more digitally-intensive electric vehicle architectures.
Application Analysis and Market Segmentation
The integration of security solutions is increasingly tailored to the specific powertrain and architectural needs of the vehicle, as well as the technical layer being protected.
By Application (Vehicle Type)
Battery Electric Vehicles (BEV): This segment is expected to witness the highest growth, projected at 10%–17% annually. BEVs are built on modern, centralized electronic architectures that rely heavily on Over-the-Air (OTA) updates and cloud-based battery management systems, making integrated security a foundational requirement.
Plug-in Hybrid Electric Vehicles (PHEV) and Hybrid Electric Vehicles (HEV): These segments show steady growth in the range of 6%–12%. While these vehicles retain traditional mechanical systems, their increasingly sophisticated infotainment and diagnostic tools necessitate robust security patches to prevent lateral movement of threats within the vehicle network.
Fuel Cell Electric Vehicles (FCEV): Though currently a niche segment, FCEV security is anticipated to grow at 5%–9%, primarily driven by commercial fleet applications where secure telemetry is vital for hydrogen infrastructure monitoring and route optimization.
By Security Type
Network Security: Projected to grow at 8%–15%, network security remains the dominant segment. It focuses on protecting the "pipes" through which data flows, including the CAN bus, Automotive Ethernet, and cellular links. With the rise of V2X, securing these communication channels against interception is paramount.
Endpoint Security: Estimated growth of 7%–13%. This involves securing individual ECUs and sensors within the car. As vehicles adopt more "edge" processing for autonomous driving, protecting these localized intelligence points from tampering becomes critical.
Application Security: Projected to expand at 9%–16%. This covers the protection of third-party apps, infotainment services, and mobile-to-car interfaces. As consumers demand "smartphone-like" experiences in their dashboards, the risk of malware through these portals increases.
Cloud Security: This is a rapidly emerging segment with a projected growth of 10%–18%. Since much of a connected car’s data is processed off-board, securing the vehicle-to-cloud (V2C) pipeline and the backend infrastructure where vehicle data is stored is essential for fleet management and insurance telematics.
Regional Market Distribution and Geographic Trends
The demand for connected car security is deeply influenced by regional automotive production volumes and the maturity of local cybersecurity legislation.
North America: Projected annual growth of 7%–14%. The United States is a primary hub for security innovation, led by a strong ecosystem of tech giants and early adoption of V2V safety standards. Trends here focus on protecting the large-scale commercial fleet and premium passenger vehicle markets.
Asia-Pacific: This region is expected to be the most dynamic, with growth rates of 9%–16%. China, as the world’s largest producer of EVs, is a significant driver of demand, supported by the Ministry of Industry and Information Technology (MIIT) mandates for automotive data security. Japan and South Korea also contribute through their global OEMs who are increasingly prioritizing standardizing security across all export models.
Europe: Estimated growth of 6.5%–13%. Growth is heavily mandated by the European Union’s Cybersecurity Act and the implementation of UNECE WP.29 regulations. Germany, France, and the UK are leading in the deployment of secure gateways and Intrusion Detection and Prevention Systems (IDPS).
Latin America: Projected growth of 4%–8%. Adoption is led by Brazil and Mexico, primarily driven by the export requirements of local manufacturing plants supplying North American and European markets.
Middle East & Africa (MEA): Anticipated growth of 5%–10%. The region, particularly the GCC, is seeing increased interest in "Smart City" infrastructures and luxury connected vehicles, which require high-end, cloud-integrated security solutions.
Key Market Players and Competitive Landscape
The market features a complex interplay between traditional Tier-1 automotive suppliers and specialized cybersecurity firms.
Harman International: A subsidiary of Samsung, Harman integrates security deeply into its "Digital Cockpit" and telematics solutions. Their approach emphasizes end-to-end protection from the vehicle to the cloud.
Argus Cyber Security Ltd. & Karamba Security: These Israel-based firms are pioneers in the niche. Argus focuses on multi-layered IDPS and fleet protection, while Karamba is known for "Autonomous Security" that hardens the vehicle's software during the development phase.
VicOne Inc.: Backed by Trend Micro, VicOne leverages extensive threat intelligence to provide vulnerability management and security operations center (SOC) services specifically for OEMs and fleet operators.
GuardKnox Cyber Technologies Ltd.: Specializes in high-performance computing (HPC) and SOA (Service Oriented Architecture) security, positioning themselves as a provider of the "secure brain" for future vehicles.
Continental AG, Bosch Mobility Solutions, and Denso Corporation: As global Tier-1 suppliers, these companies are embedding security into their hardware components, such as gateways and smart sensors, ensuring that security is a built-in feature of the vehicle’s physical architecture.
NXP Semiconductors N.V. & Infineon Technologies AG: These semiconductor leaders provide the underlying hardware security modules (HSMs) and secure microcontrollers that serve as the "root of trust" for all software-level security measures.
BlackBerry Limited (QNX): Once a mobile giant, BlackBerry has pivoted to become a leader in secure embedded operating systems, with its QNX platform powering the safety-critical systems of millions of vehicles.
Industry Value Chain Analysis
The Connected Car Security value chain is a multi-tiered ecosystem where value is increasingly migrating from hardware to software and services.
Semiconductor and Hardware Layer: This upstream stage involves the production of secure chips and hardware security modules. Companies like Infineon and NXP provide the physical foundation, ensuring that encryption keys and sensitive data are stored in tamper-proof environments.
Software and Operating System Layer: Here, specialized security vendors and OS providers like BlackBerry QNX or Escrypt GmbH integrate security protocols into the vehicle's software stack. This includes secure booting, code signing, and the development of the vehicle's internal firewalls.
Tier-1 Integration: Major suppliers like Bosch and Continental integrate these secure components into larger subsystems, such as ADAS or Infotainment units, before delivering them to the vehicle manufacturer.
OEM Deployment and Orchestration: The vehicle manufacturers (OEMs) are responsible for the final integration of these systems. They also manage the lifecycle of security through OTA updates and maintain Automotive Security Operations Centers (ASOCs) to monitor for fleet-wide threats in real-time.
Service and Data Providers: Downstream, companies like Upstream Security or Cisco Systems provide cloud-based analytics and threat intelligence. They analyze the massive streams of data coming from connected fleets to identify anomalies that could indicate a zero-day exploit or a coordinated attack.
Market Opportunities and Challenges
Opportunities
The Rise of Autonomous Driving: As vehicles take over control from humans, the "cost of failure" for a cyber-attack rises to life-threatening levels. This creates an urgent, high-value market for fail-safe security systems and redundant protective layers.
Software-as-a-Service (SaaS) and Security-as-a-Service: There is a significant opportunity for security firms to move toward recurring revenue models, providing ongoing threat monitoring, vulnerability management, and OTA security patches throughout the 10-15 year lifespan of a vehicle.
V2X and Infrastructure Integration: As cars begin communicating with smart traffic lights and grid infrastructure, the need for mutual authentication and secure messaging protocols will open new revenue streams for network security providers.
Challenges
Complexity of Legacy Systems: Automakers often use a mix of modern and legacy components from hundreds of different suppliers. Achieving a unified security posture across this heterogeneous environment is a massive technical challenge.
Supply Chain Vulnerabilities: A security breach at a small, third-tier software component provider can compromise the entire vehicle. Ensuring "software bill of materials" (SBOM) transparency across the supply chain remains difficult.
Computational Constraints: While cars are becoming more powerful, many ECUs still have limited processing power and memory. Implementing robust encryption and monitoring without causing latency in safety-critical systems (like braking) requires highly optimized, efficient software.
Chapter 1 Executive Summary
Chapter 2 Abbreviation and Acronyms
Chapter 3 Preface
3.1 Research Scope
3.2 Research Sources
3.2.1 Data Sources
3.2.2 Assumptions
3.3 Research Method
Chapter 4 Market Landscape
4.1 Market Overview
4.2 Classification/Types
4.3 Application/End Users
Chapter 5 Market Trend Analysis
5.1 introduction
5.2 Drivers
5.3 Restraints
5.4 Opportunities
5.5 Threats
Chapter 6 Industry Chain Analysis
6.1 Upstream/Suppliers Analysis
6.2 Connected Car Security Analysis
6.2.1 Technology Analysis
6.2.2 Cost Analysis
6.2.3 Market Channel Analysis
6.3 Downstream Buyers/End Users
Chapter 7 Latest Market Dynamics
7.1 Latest News
7.2 Merger and Acquisition
7.3 Planned/Future Project
7.4 Policy Dynamics
Chapter 8 Historical and Forecast Connected Car Security Market in North America (2021-2031)
8.1 Connected Car Security Market Size
8.2 Connected Car Security Market by End Use
8.3 Competition by Players/Suppliers
8.4 Connected Car Security Market Size by Type
8.5 Key Countries Analysis
8.5.1 United States
8.5.2 Canada
8.5.3 Mexico
Chapter 9 Historical and Forecast Connected Car Security Market in South America (2021-2031)
9.1 Connected Car Security Market Size
9.2 Connected Car Security Market by End Use
9.3 Competition by Players/Suppliers
9.4 Connected Car Security Market Size by Type
9.5 Key Countries Analysis
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Chile
9.5.4 Peru
Chapter 10 Historical and Forecast Connected Car Security Market in Asia & Pacific (2021-2031)
10.1 Connected Car Security Market Size
10.2 Connected Car Security Market by End Use
10.3 Competition by Players/Suppliers
10.4 Connected Car Security Market Size by Type
10.5 Key Countries Analysis
10.5.1 China
10.5.2 India
10.5.3 Japan
10.5.4 South Korea
10.5.5 Southest Asia
10.5.6 Australia
Chapter 11 Historical and Forecast Connected Car Security Market in Europe (2021-2031)
11.1 Connected Car Security Market Size
11.2 Connected Car Security Market by End Use
11.3 Competition by Players/Suppliers
11.4 Connected Car Security Market Size by Type
11.5 Key Countries Analysis
11.5.1 Germany
11.5.2 France
11.5.3 United Kingdom
11.5.4 Italy
11.5.5 Spain
11.5.6 Belgium
11.5.7 Netherlands
11.5.8 Austria
11.5.9 Poland
11.5.10 Russia
Chapter 12 Historical and Forecast Connected Car Security Market in MEA (2021-2031)
12.1 Connected Car Security Market Size
12.2 Connected Car Security Market by End Use
12.3 Competition by Players/Suppliers
12.4 Connected Car Security Market Size by Type
12.5 Key Countries Analysis
12.5.1 Egypt
12.5.2 Israel
12.5.3 South Africa
12.5.4 Gulf Cooperation Council Countries
12.5.5 Turkey
Chapter 13 Summary For Global Connected Car Security Market (2021-2026)
13.1 Connected Car Security Market Size
13.2 Connected Car Security Market by End Use
13.3 Competition by Players/Suppliers
13.4 Connected Car Security Market Size by Type
Chapter 14 Global Connected Car Security Market Forecast (2026-2031)
14.1 Connected Car Security Market Size Forecast
14.2 Connected Car Security Application Forecast
14.3 Competition by Players/Suppliers
14.4 Connected Car Security Type Forecast
Chapter 15 Analysis of Global Key Vendors
15.1 Harman International
15.1.1 Company Profile
15.1.2 Main Business and Connected Car Security Information
15.1.3 SWOT Analysis of Harman International
15.1.4 Harman International Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.2 Argus Cyber Security Ltd.
15.2.1 Company Profile
15.2.2 Main Business and Connected Car Security Information
15.2.3 SWOT Analysis of Argus Cyber Security Ltd.
15.2.4 Argus Cyber Security Ltd. Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.3 Karamba Security
15.3.1 Company Profile
15.3.2 Main Business and Connected Car Security Information
15.3.3 SWOT Analysis of Karamba Security
15.3.4 Karamba Security Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.4 GuardKnox Cyber Technologies Ltd.
15.4.1 Company Profile
15.4.2 Main Business and Connected Car Security Information
15.4.3 SWOT Analysis of GuardKnox Cyber Technologies Ltd.
15.4.4 GuardKnox Cyber Technologies Ltd. Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.5 VicOne Inc.
15.5.1 Company Profile
15.5.2 Main Business and Connected Car Security Information
15.5.3 SWOT Analysis of VicOne Inc.
15.5.4 VicOne Inc. Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.6 Escrypt GmbH
15.6.1 Company Profile
15.6.2 Main Business and Connected Car Security Information
15.6.3 SWOT Analysis of Escrypt GmbH
15.6.4 Escrypt GmbH Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.7 Upstream Security Ltd.
15.7.1 Company Profile
15.7.2 Main Business and Connected Car Security Information
15.7.3 SWOT Analysis of Upstream Security Ltd.
15.7.4 Upstream Security Ltd. Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.8 NXP Semiconductors N.V.
15.8.1 Company Profile
15.8.2 Main Business and Connected Car Security Information
15.8.3 SWOT Analysis of NXP Semiconductors N.V.
15.8.4 NXP Semiconductors N.V. Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.9 Continental AG
15.9.1 Company Profile
15.9.2 Main Business and Connected Car Security Information
15.9.3 SWOT Analysis of Continental AG
15.9.4 Continental AG Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
15.10 Bosch Mobility Solutions
15.10.1 Company Profile
15.10.2 Main Business and Connected Car Security Information
15.10.3 SWOT Analysis of Bosch Mobility Solutions
15.10.4 Bosch Mobility Solutions Connected Car Security Sales, Revenue, Price and Gross Margin (2021-2026)
Please ask for sample pages for full companies list
Table Research Scope of Connected Car Security Report
Table Data Sources of Connected Car Security Report
Table Major Assumptions of Connected Car Security Report
Table Connected Car Security Classification
Table Connected Car Security Applications
Table Drivers of Connected Car Security Market
Table Restraints of Connected Car Security Market
Table Opportunities of Connected Car Security Market
Table Threats of Connected Car Security Market
Table Raw Materials Suppliers
Table Different Production Methods of Connected Car Security
Table Cost Structure Analysis of Connected Car Security
Table Key End Users
Table Latest News of Connected Car Security Market
Table Merger and Acquisition
Table Planned/Future Project of Connected Car Security Market
Table Policy of Connected Car Security Market
Table 2021-2031 North America Connected Car Security Market Size
Table 2021-2031 North America Connected Car Security Market Size by Application
Table 2021-2026 North America Connected Car Security Key Players Revenue
Table 2021-2026 North America Connected Car Security Key Players Market Share
Table 2021-2031 North America Connected Car Security Market Size by Type
Table 2021-2031 United States Connected Car Security Market Size
Table 2021-2031 Canada Connected Car Security Market Size
Table 2021-2031 Mexico Connected Car Security Market Size
Table 2021-2031 South America Connected Car Security Market Size
Table 2021-2031 South America Connected Car Security Market Size by Application
Table 2021-2026 South America Connected Car Security Key Players Revenue
Table 2021-2026 South America Connected Car Security Key Players Market Share
Table 2021-2031 South America Connected Car Security Market Size by Type
Table 2021-2031 Brazil Connected Car Security Market Size
Table 2021-2031 Argentina Connected Car Security Market Size
Table 2021-2031 Chile Connected Car Security Market Size
Table 2021-2031 Peru Connected Car Security Market Size
Table 2021-2031 Asia & Pacific Connected Car Security Market Size
Table 2021-2031 Asia & Pacific Connected Car Security Market Size by Application
Table 2021-2026 Asia & Pacific Connected Car Security Key Players Revenue
Table 2021-2026 Asia & Pacific Connected Car Security Key Players Market Share
Table 2021-2031 Asia & Pacific Connected Car Security Market Size by Type
Table 2021-2031 China Connected Car Security Market Size
Table 2021-2031 India Connected Car Security Market Size
Table 2021-2031 Japan Connected Car Security Market Size
Table 2021-2031 South Korea Connected Car Security Market Size
Table 2021-2031 Southeast Asia Connected Car Security Market Size
Table 2021-2031 Australia Connected Car Security Market Size
Table 2021-2031 Europe Connected Car Security Market Size
Table 2021-2031 Europe Connected Car Security Market Size by Application
Table 2021-2026 Europe Connected Car Security Key Players Revenue
Table 2021-2026 Europe Connected Car Security Key Players Market Share
Table 2021-2031 Europe Connected Car Security Market Size by Type
Table 2021-2031 Germany Connected Car Security Market Size
Table 2021-2031 France Connected Car Security Market Size
Table 2021-2031 United Kingdom Connected Car Security Market Size
Table 2021-2031 Italy Connected Car Security Market Size
Table 2021-2031 Spain Connected Car Security Market Size
Table 2021-2031 Belgium Connected Car Security Market Size
Table 2021-2031 Netherlands Connected Car Security Market Size
Table 2021-2031 Austria Connected Car Security Market Size
Table 2021-2031 Poland Connected Car Security Market Size
Table 2021-2031 Russia Connected Car Security Market Size
Table 2021-2031 MEA Connected Car Security Market Size
Table 2021-2031 MEA Connected Car Security Market Size by Application
Table 2021-2026 MEA Connected Car Security Key Players Revenue
Table 2021-2026 MEA Connected Car Security Key Players Market Share
Table 2021-2031 MEA Connected Car Security Market Size by Type
Table 2021-2031 Egypt Connected Car Security Market Size
Table 2021-2031 Israel Connected Car Security Market Size
Table 2021-2031 South Africa Connected Car Security Market Size
Table 2021-2031 Gulf Cooperation Council Countries Connected Car Security Market Size
Table 2021-2031 Turkey Connected Car Security Market Size
Table 2021-2026 Global Connected Car Security Market Size by Region
Table 2021-2026 Global Connected Car Security Market Size Share by Region
Table 2021-2026 Global Connected Car Security Market Size by Application
Table 2021-2026 Global Connected Car Security Market Share by Application
Table 2021-2026 Global Connected Car Security Key Vendors Revenue
Table 2021-2026 Global Connected Car Security Key Vendors Market Share
Table 2021-2026 Global Connected Car Security Market Size by Type
Table 2021-2026 Global Connected Car Security Market Share by Type
Table 2026-2031 Global Connected Car Security Market Size by Region
Table 2026-2031 Global Connected Car Security Market Size Share by Region
Table 2026-2031 Global Connected Car Security Market Size by Application
Table 2026-2031 Global Connected Car Security Market Share by Application
Table 2026-2031 Global Connected Car Security Key Vendors Revenue
Table 2026-2031 Global Connected Car Security Key Vendors Market Share
Table 2026-2031 Global Connected Car Security Market Size by Type
Table 2026-2031 Connected Car Security Global Market Share by Type
Figure Market Size Estimated Method
Figure Major Forecasting Factors
Figure Connected Car Security Picture
Figure 2021-2031 North America Connected Car Security Market Size and CAGR
Figure 2021-2031 South America Connected Car Security Market Size and CAGR
Figure 2021-2031 Asia & Pacific Connected Car Security Market Size and CAGR
Figure 2021-2031 Europe Connected Car Security Market Size and CAGR
Figure 2021-2031 MEA Connected Car Security Market Size and CAGR
Figure 2021-2026 Global Connected Car Security Market Size and Growth Rate
Figure 2026-2031 Global Connected Car Security Market Size and Growth Rate
Research Methodology
- Market Estimated Methodology:
Bottom-up & top-down approach, supply & demand approach are the most important method which is used by HDIN Research to estimate the market size.
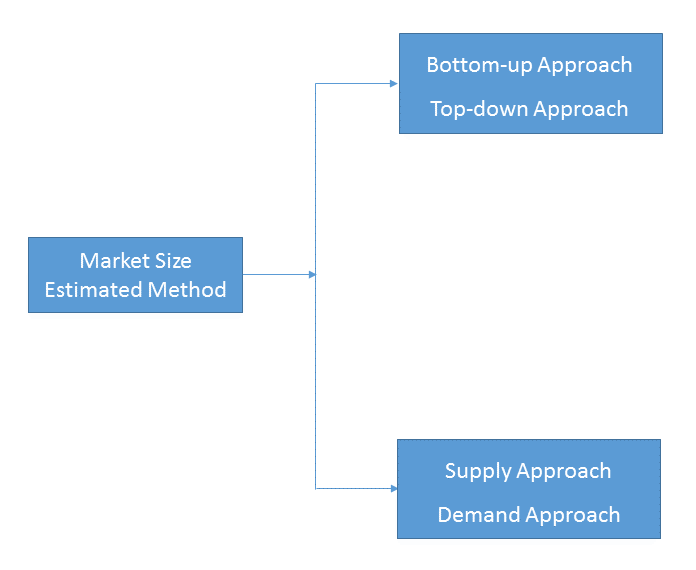
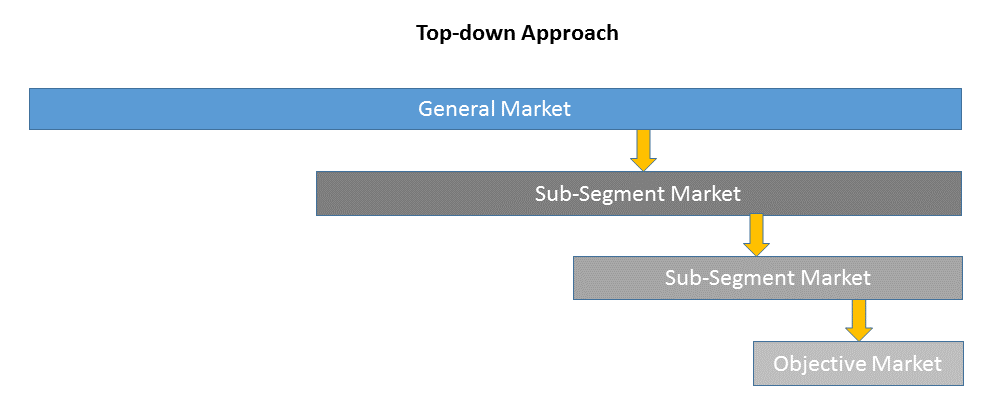
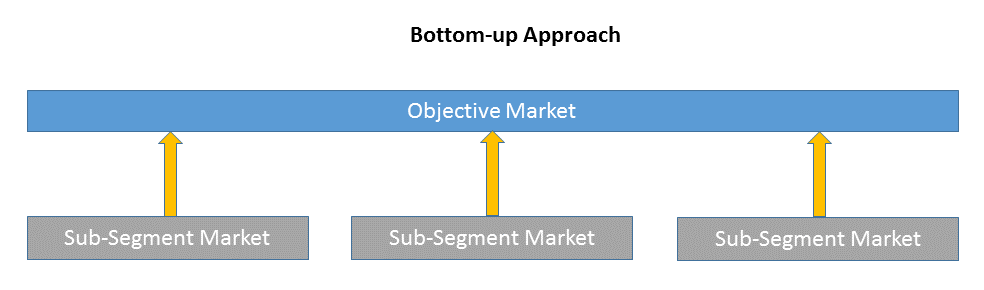
1)Top-down & Bottom-up Approach
Top-down approach uses a general market size figure and determines the percentage that the objective market represents.
Bottom-up approach size the objective market by collecting the sub-segment information.
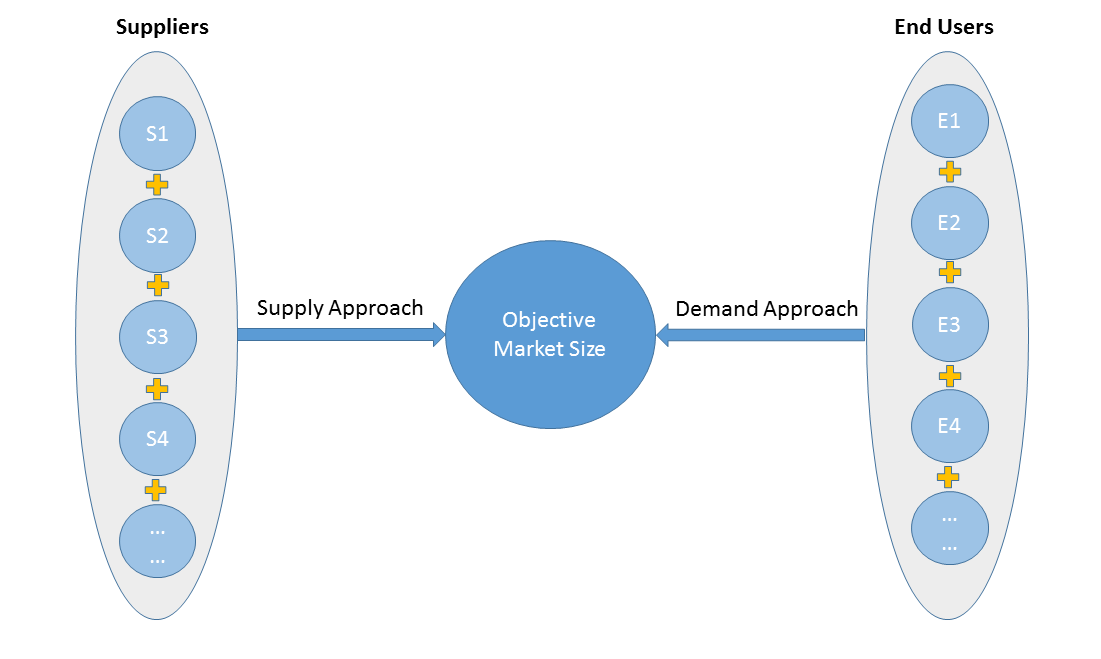
2)Supply & Demand Approach
Supply approach is based on assessments of the size of each competitor supplying the objective market.
Demand approach combine end-user data within a market to estimate the objective market size. It is sometimes referred to as bottom-up approach.
- Forecasting Methodology
- Numerous factors impacting the market trend are considered for forecast model:
- New technology and application in the future;
- New project planned/under contraction;
- Global and regional underlying economic growth;
- Threatens of substitute products;
- Industry expert opinion;
- Policy and Society implication.
- Analysis Tools
1)PEST Analysis
PEST Analysis is a simple and widely used tool that helps our client analyze the Political, Economic, Socio-Cultural, and Technological changes in their business environment.
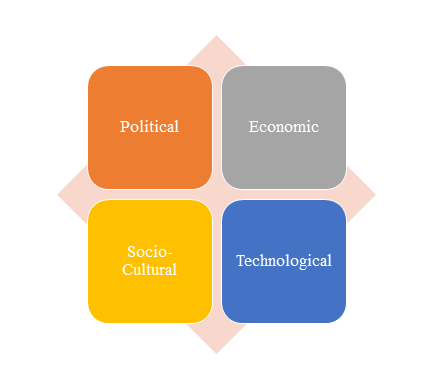
- Benefits of a PEST analysis:
- It helps you to spot business opportunities, and it gives you advanced warning of significant threats.
- It reveals the direction of change within your business environment. This helps you shape what you’re doing, so that you work with change, rather than against it.
- It helps you avoid starting projects that are likely to fail, for reasons beyond your control.
- It can help you break free of unconscious assumptions when you enter a new country, region, or market; because it helps you develop an objective view of this new environment.
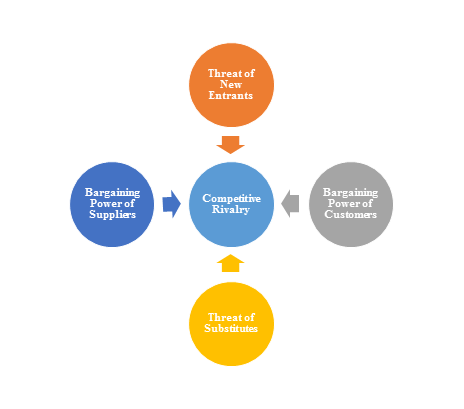
2)Porter’s Five Force Model Analysis
The Porter’s Five Force Model is a tool that can be used to analyze the opportunities and overall competitive advantage. The five forces that can assist in determining the competitive intensity and potential attractiveness within a specific area.
- Threat of New Entrants: Profitable industries that yield high returns will attract new firms.
- Threat of Substitutes: A substitute product uses a different technology to try to solve the same economic need.
- Bargaining Power of Customers: the ability of customers to put the firm under pressure, which also affects the customer's sensitivity to price changes.
- Bargaining Power of Suppliers: Suppliers of raw materials, components, labor, and services (such as expertise) to the firm can be a source of power over the firm when there are few substitutes.
- Competitive Rivalry: For most industries the intensity of competitive rivalry is the major determinant of the competitiveness of the industry.
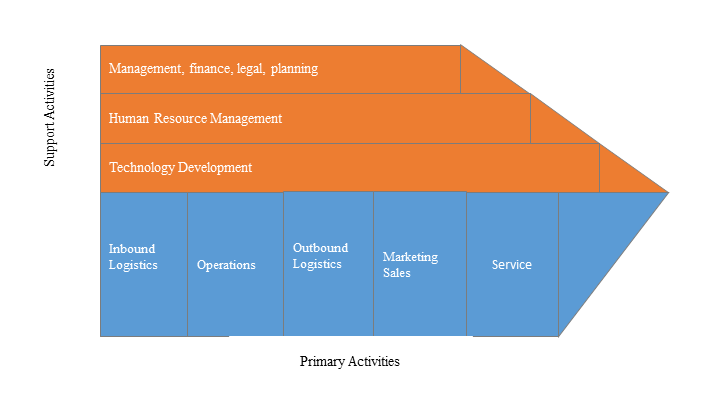
3)Value Chain Analysis
Value chain analysis is a tool to identify activities, within and around the firm and relating these activities to an assessment of competitive strength. Value chain can be analyzed by primary activities and supportive activities. Primary activities include: inbound logistics, operations, outbound logistics, marketing & sales, service. Support activities include: technology development, human resource management, management, finance, legal, planning.
4)SWOT Analysis
SWOT analysis is a tool used to evaluate a company's competitive position by identifying its strengths, weaknesses, opportunities and threats. The strengths and weakness is the inner factor; the opportunities and threats are the external factor. By analyzing the inner and external factors, the analysis can provide the detail information of the position of a player and the characteristics of the industry.
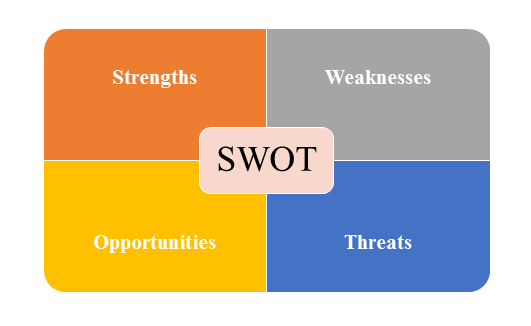
- Strengths describe what the player excels at and separates it from the competition
- Weaknesses stop the player from performing at its optimum level.
- Opportunities refer to favorable external factors that the player can use to give it a competitive advantage.
- Threats refer to factors that have the potential to harm the player.
- Data Sources
| Primary Sources | Secondary Sources |
|---|---|
| Face to face/Phone Interviews with market participants, such as: Manufactures; Distributors; End-users; Experts. Online Survey |
Government/International Organization Data: Annual Report/Presentation/Fact Book Internet Source Information Industry Association Data Free/Purchased Database Market Research Report Book/Journal/News |